
How to Avoid Spam Filters: Focusing on Email Authentication
Getting your emails delivered to the inbox can feel like a constant battle against spam filters. While many factors contribute to deliverability, email authentication is a critical and often overlooked aspect. This article will delve into the specifics of email authentication protocols – SPF, DKIM, and DMARC – and provide practical examples to help you configure them correctly, significantly improving your chances of landing in the inbox rather than the spam folder.
Understanding SPF (Sender Policy Framework)
SPF records specify which mail servers are authorized to send emails on behalf of your domain. Failing to set up an SPF record or having an incorrectly configured record can lead to your emails being flagged as spam.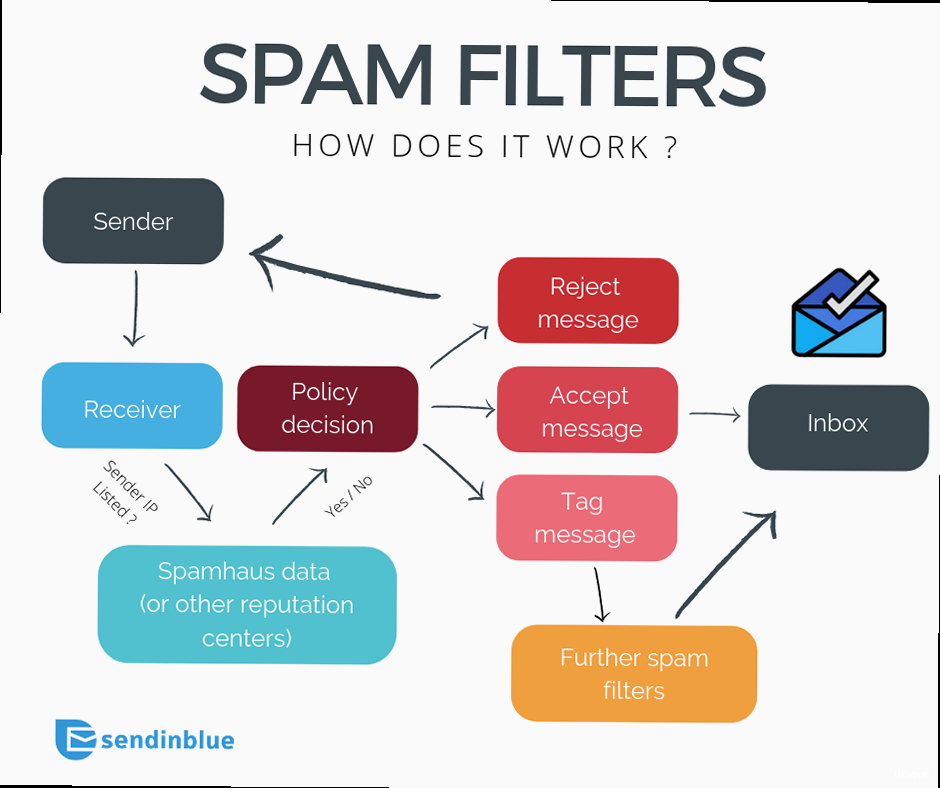
- v=spf1: This indicates the SPF version being used (currently, only spf1 exists). It’s mandatory and must be the first element in the record.
- ip4: Specifies an IPv4 address that is authorized to send email.
- ip6: Specifies an IPv6 address that is authorized to send email.
- a: Authorizes the IPv4 and IPv6 addresses associated with the specified hostname.
- mx: Authorizes the IPv4 and IPv6 addresses associated with the mail exchangers for the domain.
- include: Includes the SPF record of another domain. This is useful if you use a third-party service like Google Workspace or SendGrid to send emails.
- -all: A hard fail. If an email doesn’t match any of the previous mechanisms, it should be rejected.
- ~all: A soft fail. If an email doesn’t match any of the previous mechanisms, it should be accepted but marked as suspicious. It’s generally recommended to use `-all` for stricter enforcement.
- ?all: Neutral. The receiving server should accept the email and do not mark it as suspicious.
v=spf1 ip4:192.0.2.1 -allv=spf1 include:_spf.google.com ~allv=spf1 ip4:192.0.2.1 ip4:198.51.100.0/24 a:mail.example.com -allv=spf1 include:servers.mailchimp.com ~all- MXToolbox: https://mxtoolbox.com/spf.aspx
- Dmarcian: https://dmarcian.com/spf-survey/
- Having Multiple SPF Records: As mentioned earlier, having multiple SPF records for a domain is a common mistake that can cause SPF checks to fail.
- Incorrect Syntax: SPF records are sensitive to syntax errors. Double-check your record for typos and ensure that all elements are correctly formatted.
- Missing the `include` Directive for Third-Party Services: If you use third-party email services, make sure to include their SPF records in your SPF record.
- Using `+all`: This allows any server to send email on your behalf, defeating the purpose of SPF. Avoid it at all costs.
- Exceeding the 10 DNS Lookup Limit: SPF records can trigger DNS lookups when using mechanisms like `include`, `a`, or `mx`. SPF specifications limit the number of DNS lookups to 10. Exceeding this limit can cause SPF checks to fail, even if your record is syntactically correct. Flattening your SPF record by replacing `include` statements with the actual IP addresses can help avoid this limit, but requires more maintenance.
Implementing DKIM (DomainKeys Identified Mail)
DKIM provides an encrypted digital signature that verifies the sender and ensures the message hasn’t been altered during transit. This helps receiving mail servers confirm that the email genuinely originated from your domain.
openssl genrsa -out private.key 2048
openssl rsa -in private.key -pubout -out public.keyopendkim-genkey -t -d example.com -s mailv=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwWx6VjJ9vQ0hT8fV73w79Jys5qJvL+l5v8WvQnQ6Z0U7xZ8Y0bJ2a3R9iU6o+p4iO3l3K6j8g7h5f4v2c1b9a8z7x0y5w4v3u2r1t9s8q7p6n5m4l3k2j1i0h8g7f6e5d4c3b2a1z9y8x7w6v5u4t3s2r1q0p9o8n7m6l5k4j3i2h1g0f8e7d6c5b4a3z2y1x9w8v7u6t5s4r3q2p1o0n9m8l7k6j5i4h3g2f1e0d8c7b6a5z4y3x2w1v9u8t7s6r5q4p3o2n1m0l9k8j7i6h5g4f3e2d1c0b8a7z6y5x4w3v2u1t9s8r7q6p5o4n3m2l1k0j9i8h7g6f5e4d3c2b1a0z9y8x7w6v5u4t3s2r1q0p9o8n7m6l5k4j3i2h1g0f8e7d6c5b4a3z2y1x9w==- v=DKIM1: Specifies the DKIM version.
- k=rsa: Specifies the key type (RSA).
- p=: Contains the base64-encoded public key.
| Hostname | Type | Value |
|---|---|---|
| mail._domainkey.example.com | TXT | v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwWx6VjJ9vQ0hT8fV73w79Jys5qJvL+l5v8WvQnQ6Z0U7xZ8Y0bJ2a3R9iU6o+p4iO3l3K6j8g7h5f4v2c1b9a8z7x0y5w4v3u2r1t9s8q7p6n5m4l3k2j1i0h8g7f6e5d4c3b2a1z9y8x7w6v5u4t3s2r1q0p9o8n7m6l5k4j3i2h1g0f8e7d6c5b4a3z2y1x9w== |
apt-get install opendkim opendkim-tools
Socket inet:8891@localhost
PidFile /var/run/opendkim/opendkim.pid
User opendkim:opendkim
SigningTable refile:/etc/opendkim/SigningTable
KeyTable refile:/etc/opendkim/KeyTable
TrustAnchorFile /usr/share/dns/root.key
*@example.com mail._domainkey.example.commail._domainkey.example.com example.com:mail:/etc/opendkim/keys/mail.privatemkdir /etc/opendkim/keys
mv mail.private /etc/opendkim/keys/
chown opendkim:opendkim /etc/opendkim/keys/mail.private
chmod 600 /etc/opendkim/keys/mail.privatemilter_default_action = accept
milter_protocol = 2
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = inet:127.0.0.1:8891systemctl restart opendkim
systemctl restart postfix- Mail-Tester: https://www.mail-tester.com/
- Check-Auth: Send an email to `check-auth@verifier.port25.com`
Configuring DMARC (Domain-based Message Authentication, Reporting & Conformance)
DMARC builds upon SPF and DKIM, allowing you to tell receiving mail servers what to do with emails that fail authentication checks. It also provides reporting, so you can monitor your email authentication performance and identify potential issues. DMARC essentially acts as a policy layer on top of SPF and DKIM. It allows you to specify how receiving mail servers should handle emails that fail SPF and/or DKIM checks. You can choose to have these emails quarantined (sent to spam), rejected outright, or treated normally. DMARC also provides a reporting mechanism, allowing you to receive reports from receiving mail servers about the authentication results of emails claiming to be from your domain. This valuable feedback helps you identify and address any authentication issues. Creating a DMARC Record A DMARC record is another TXT record that you add to your domain’s DNS settings. The name of the record is always `_dmarc.yourdomain.com`. The value of the record specifies your DMARC policy and reporting preferences. Here’s a breakdown of common DMARC record elements:- v=DMARC1: Specifies the DMARC version. This is mandatory and must be the first element.
- p=: Specifies the policy to be applied to emails that fail DMARC authentication. Possible values are:
- `none`: Take no specific action. The receiving server should treat the email as normal. This is useful for monitoring.
- `quarantine`: The receiving server should quarantine the email (e.g., send it to the spam folder).
- `reject`: The receiving server should reject the email outright.
- rua=: Specifies the email address(es) to which aggregate reports should be sent. Aggregate reports provide a summary of the authentication results of emails claiming to be from your domain.
- ruf=: Specifies the email address(es) to which forensic reports (also known as failure reports) should be sent. Forensic reports provide detailed information about individual emails that failed authentication. This is often disabled for privacy reasons.
- adkim=: Specifies alignment mode for DKIM. `r` for relaxed, `s` for strict.
- aspf=: Specifies alignment mode for SPF. `r` for relaxed, `s` for strict.
- fo=: Specifies failure reporting options. `0` to generate a report if all underlying authentication checks fail. `1` to generate a report if either DKIM or SPF fails. `d` to generate a DKIM failure report, and `s` to generate an SPF failure report.
- rf=: Specifies the format for forensic reports. `afrf` is the standard.
- ri=: Specifies the interval (in seconds) at which aggregate reports should be sent. The default is 86400 (one day).
- pct=: Specifies the percentage of emails to which the DMARC policy should be applied. This allows you to gradually roll out a DMARC policy. A value of 100 means that the policy should be applied to all emails.
v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com; pct=100;v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com; ruf=mailto:forensic-reports@example.com; pct=100;v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com; aspf=s; adkim=s;- Legitimate emails that are failing authentication.
- Unauthorized senders who are spoofing your domain.
- Configuration errors in your SPF or DKIM records.
- Dmarcian
- Proofpoint
- Valimail
Beyond Authentication: Additional Factors for Inbox Placement
While SPF, DKIM, and DMARC are crucial, they are not the only factors that determine whether your emails reach the inbox. Email providers consider various other elements when filtering spam. Email authentication establishes your legitimacy, but factors such as your sender reputation, email content, and recipient engagement also play significant roles in determining whether your emails land in the inbox or the spam folder. A holistic approach to email deliverability requires attention to these additional areas. Sender Reputation Your sender reputation is a measure of how trustworthy your email sending practices are perceived to be by email providers. It’s based on factors like your IP address history, sending volume, and complaint rates. A poor sender reputation can significantly impact your deliverability, even if your email authentication is properly configured. Here are some tips for maintaining a good sender reputation:- Use a Dedicated IP Address: Using a dedicated IP address gives you more control over your sender reputation. Shared IP addresses can be affected by the sending practices of other users.
- Warm Up Your IP Address: If you’re using a new IP address, gradually increase your sending volume over time. This helps email providers establish a positive reputation for your IP address.
- Maintain Low Complaint Rates: Encourage recipients to unsubscribe rather than marking your emails as spam. Keep your complaint rates below 0.1%.
- Authenticate Your Emails: As discussed earlier, SPF, DKIM, and DMARC are essential for establishing your legitimacy and protecting your sender reputation.
- Monitor Blacklists: Regularly check your IP address and domain against email blacklists. If you find yourself on a blacklist, take immediate action to get removed. Tools like MXToolbox can help with this.
- Avoid Spam Trigger Words: Be mindful of the words and phrases you use in your emails. Avoid using words like “free,” “guaranteed,” “urgent,” and “limited time offer” excessively. A quick online search will reveal lists of common spam trigger words.
- Use Proper Grammar and Spelling: Poor grammar and spelling can make your emails look unprofessional and suspicious. Proofread your emails carefully before sending them.
- Avoid Excessive Use of Capital Letters and Exclamation Points: Using too many capital letters and exclamation points can make your emails look like spam.
- Include a Clear Unsubscribe Link: Make it easy for recipients to unsubscribe from your emails. This shows that you respect their preferences and are not trying to trap them.
- Use Alt Text for Images: Always include alt text for images in your emails. Some email clients block images by default, so alt text ensures that recipients can understand the content of your email even if the images are not displayed.
- Maintain a Good Text-to-Image Ratio: Don’t rely solely on images to convey your message. Use a good balance of text and images. Emails with only images are more likely to be flagged as spam.
- Send Relevant and Personalized Emails: Tailor your emails to the interests and preferences of your recipients. Use personalization to make your emails more engaging.
- Segment Your Email List: Segment your email list based on demographics, interests, and behavior. This allows you to send more targeted emails to specific groups of recipients.
- Clean Your Email List Regularly: Remove inactive subscribers from your email list. Sending emails to inactive subscribers can hurt your engagement rates and sender reputation.
- Use A/B Testing: Experiment with different subject lines, email content, and sending times to see what works best for your audience.
- Ask Recipients to Add You to Their Address Book: This can help improve deliverability by ensuring that your emails are not filtered into the spam folder.
- Use a Reliable Mail Server: Choose
person
Article Monster
Email marketing expert sharing insights about cold outreach, deliverability, and sales growth strategies.