Email Marketing Secrets to Avoid Spam Filters: Authentication is Key
In the competitive landscape of email marketing, reaching the inbox is half the battle. Spam filters are becoming increasingly sophisticated, making it crucial for marketers to implement robust authentication measures to protect their sender reputation and ensure their messages land where they’re intended. This article dives deep into the world of email authentication, revealing the secrets to configuring SPF, DKIM, and DMARC to bypass spam filters and improve email deliverability.
Understanding Email Authentication: SPF, DKIM, and DMARC

Email authentication protocols are the cornerstone of modern email deliverability. They provide a mechanism for receiving mail servers to verify the legitimacy of sending servers, reducing the risk of phishing, spoofing, and spam. Understanding how SPF, DKIM, and DMARC work individually and together is the first step toward improving your email marketing campaign’s success.
SPF (Sender Policy Framework) allows you to specify which mail servers are authorized to send emails on behalf of your domain. This helps prevent spammers from forging the ‘From’ address and impersonating your brand. When a receiving mail server receives an email claiming to be from your domain, it checks the SPF record to see if the sending server is authorized.
DKIM (DomainKeys Identified Mail) uses cryptographic signatures to verify that an email was indeed sent by the domain it claims to be from and that the message content has not been altered in transit. A DKIM signature is added to the email header and verified by the receiving server using a public key published in the domain’s DNS records.
DMARC (Domain-based Message Authentication, Reporting & Conformance) builds upon SPF and DKIM by providing a policy for how receiving mail servers should handle emails that fail SPF and/or DKIM checks. It also provides reporting mechanisms, allowing you to receive feedback on your email authentication setup and identify potential issues. DMARC policies can range from simply monitoring authentication results to rejecting emails that fail authentication.
SPF Configuration Examples
Configuring SPF involves creating a TXT record in your domain’s DNS settings. Here are a few examples:
- Basic SPF Record:
v=spf1 a mx -all
This record allows emails sent from the domain’s A record (IP address) and MX records (mail servers). The-allat the end signifies that any other source should be hard failed. - Including a Third-Party Email Service:
v=spf1 include:servers.mcsv.net ~all
This is a common setup when using a service like Mailchimp. It tells receiving servers to also check the SPF record forservers.mcsv.net. The~allmeans a soft fail, meaning emails from other sources might be accepted but flagged as potentially suspicious. - Allowing Multiple Sources:
v=spf1 ip4:192.0.2.0/24 ip6:2001:db8::/32 a mx include:example.com -all
This more complex record allows emails from a specific IPv4 range (192.0.2.0/24), an IPv6 range (2001:db8::/32), the domain’s A and MX records, and any sources authorized byexample.com‘s SPF record.
Important Considerations: Avoid exceeding the 10-lookup limit in SPF records, which can cause authentication failures. Use the include mechanism judiciously and flatten your SPF record if necessary using tools available online.
DKIM Configuration Examples
DKIM configuration generally involves generating a public/private key pair. The private key is used by your email server to sign outgoing emails, and the public key is published in your DNS records. The receiving server uses the public key to verify the signature.
- Adding the DKIM Record: After generating the key pair, you’ll typically add a TXT record to your DNS with the following format:
selector._domainkey.yourdomain.com IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQD..."
Replaceselectorwith the selector you chose during key generation (often ‘default’ or ‘mail’). Replaceyourdomain.comwith your actual domain. Thep=value contains your public key. - Example DKIM Key Generation (Linux command):
openssl genrsa -out private.key 2048
This command generates a 2048-bit RSA private key. You’ll then need to extract the public key from the private key. Specific instructions vary based on your email server software. - Configuring Postfix with DKIM: Assuming you’re using OpenDKIM with Postfix, you’ll need to configure the
/etc/opendkim.conffile to specify the location of your private key and other settings. You’ll also need to update your Postfix configuration in/etc/postfix/main.cfto enable DKIM signing. Restart Postfix after making these changes.
Important Considerations: Keep your private key secure. Rotate your DKIM keys periodically for enhanced security.
DMARC Configuration Examples
DMARC allows you to specify a policy for how receiving mail servers should handle emails that fail SPF and DKIM checks. It also enables reporting, providing valuable insights into your email authentication setup.
- DMARC Policy Record:
_dmarc.yourdomain.com IN TXT "v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:dmarc-forensic@yourdomain.com"
This record sets the policy tonone, meaning that no action should be taken on emails that fail authentication. It also specifies email addresses (ruaandruf) to which aggregate and forensic reports should be sent. - Moving to a Quarantine Policy:
_dmarc.yourdomain.com IN TXT "v=DMARC1; p=quarantine; pct=10; rua=mailto:dmarc-reports@yourdomain.com"
This record sets the policy toquarantine, instructing receiving servers to place emails that fail authentication into the spam folder. Thepct=10attribute specifies that only 10% of failing emails should be quarantined, allowing you to gradually roll out the policy. - Implementing a Reject Policy:
_dmarc.yourdomain.com IN TXT "v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.com"
This is the most restrictive policy, instructing receiving servers to reject emails that fail authentication. Only implement this policy after carefully monitoring your DMARC reports and ensuring that all legitimate emails are properly authenticated.
Important Considerations: Start with a p=none policy and gradually move towards p=quarantine and eventually p=reject as you gain confidence in your email authentication setup. Regularly monitor your DMARC reports to identify and address any issues.
“Email authentication is not a one-time setup; it’s an ongoing process that requires continuous monitoring and adjustments.” – Email Deliverability Expert
Optimizing Email Content for Deliverability
 subject lines, links, and attachments." title="Illustration for An image depicting various elements of an email that can affect deliverability, such as subject lines, links, and attachments." width="512" height="512" / class="wp-image-220 wp-image-12401">
subject lines, links, and attachments." title="Illustration for An image depicting various elements of an email that can affect deliverability, such as subject lines, links, and attachments." width="512" height="512" / class="wp-image-220 wp-image-12401">Beyond authentication, the content of your emails plays a significant role in determining whether they reach the inbox or end up in the spam folder. Spam filters analyze various aspects of your email content, including subject lines, body text, links, and attachments, to identify potentially malicious or unwanted messages. Optimizing your email content is therefore crucial for improving deliverability and ensuring that your message is seen by your intended audience.
Crafting Effective Subject Lines
The subject line is the first impression your email makes. It’s crucial to craft subject lines that are both engaging and informative while avoiding language that might trigger spam filters.
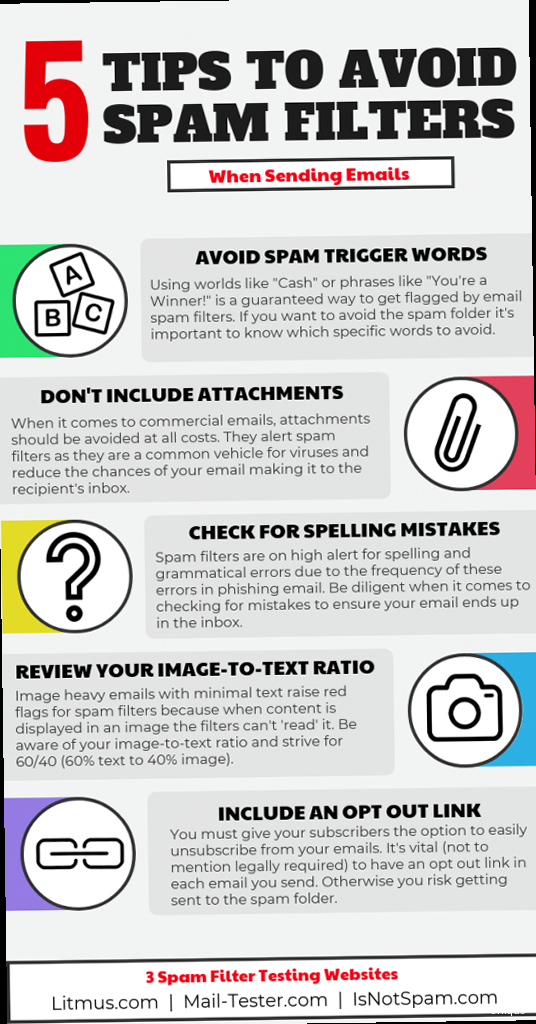
- Avoid Spam Trigger Words: Words like “free,” “guaranteed,” “urgent,” and excessive use of exclamation points are red flags for spam filters. Use a thesaurus to find alternative words or phrases.
- Personalization: Personalizing subject lines (e.g., using the recipient’s name) can improve open rates and deliverability. However, avoid over-personalization, which can also trigger spam filters.
- Keep it Concise: Shorter subject lines (under 50 characters) are more likely to be fully displayed on mobile devices and less likely to be flagged as spam.
- A/B Testing: Experiment with different subject lines to see what resonates best with your audience and improves your deliverability.
Example: Instead of “FREE! Guaranteed Weight Loss,” try “Healthy Weight Loss Tips for You.”
Optimizing Email Body Text
The body of your email should be well-written, informative, and free of spam triggers. Pay attention to formatting, links, and image usage to ensure optimal deliverability.
- Maintain a Good Text-to-Image Ratio: Avoid sending emails that are primarily images. Spam filters can’t “read” images, so they often flag image-heavy emails as suspicious. Aim for a text-to-image ratio of at least 60:40.
- Use Alt Text for Images: Always include descriptive alt text for images. This helps users understand the image content if it doesn’t load and provides context for spam filters.
- Avoid Excessive HTML Formatting: Keep your HTML code clean and simple. Avoid using excessive colors, fonts, and tables.
- Use Authentic Links: Avoid using URL shorteners, as they can be associated with spam. Ensure that all links in your email point to legitimate websites.
- Plain Text Version: Always include a plain text version of your email in addition to the HTML version. This ensures that your message is accessible to recipients who have disabled HTML email and provides a fallback for spam filters.
Example: Instead of a single large image with text overlaid, break the information into smaller images with descriptive alt text and supporting text paragraphs.
Managing Attachments
Attachments can be a significant spam trigger. Use them sparingly and only when necessary.
- Avoid Executable Files: Never send executable files (e.g., .exe, .bat, .scr) as attachments. These are almost always blocked by spam filters.
- Use Common File Formats: Stick to common file formats like PDF, DOC, and JPG.
- Compress Large Files: Compress large files using ZIP or other archiving tools to reduce their size.
- Consider Cloud Storage: Instead of attaching files directly, consider uploading them to a cloud storage service like Google Drive or Dropbox and including a link in your email.
Example: Instead of attaching a large PDF document, upload it to Google Drive and share a link to the document in your email.
Maintaining a Clean Email List
The health of your email list is a critical factor in determining your sender reputation and deliverability. Sending emails to outdated, inactive, or invalid email addresses can significantly damage your reputation and increase the likelihood of your emails being flagged as spam. Maintaining a clean and engaged email list is therefore essential for successful email marketing.
Implementing Double Opt-In
Double opt-in is the practice of requiring subscribers to confirm their email address before being added to your mailing list. This helps ensure that the email address is valid and that the subscriber genuinely wants to receive your emails.
- Subscription Form: Include a clear and concise subscription form on your website.
- Confirmation Email: Send a confirmation email to new subscribers with a link they must click to confirm their subscription.
- Welcome Email: Once the subscriber confirms their subscription, send a welcome email introducing your brand and providing valuable content.
Example: After a user fills out your signup form, immediately send an email with the subject “Confirm Your Subscription!” and a link that directs them back to your website to verify their email address.
Regularly Removing Inactive Subscribers
Inactive subscribers can negatively impact your sender reputation. Regularly identify and remove subscribers who haven’t engaged with your emails in a long time.
- Define Inactivity: Determine what constitutes an inactive subscriber (e.g., hasn’t opened or clicked an email in six months).
- Segmentation: Segment your email list based on engagement.
- Re-engagement Campaign: Send a re-engagement campaign to inactive subscribers, offering them an incentive to stay subscribed.
- Removal: If subscribers don’t respond to the re-engagement campaign, remove them from your list.
Example: Send a series of emails to subscribers who haven’t opened an email in 6 months with subject lines like “We miss you!” and “Are you still interested?” If they don’t respond, automatically unsubscribe them.
Handling Bounces and Unsubscribes
Properly managing bounces and unsubscribes is crucial for maintaining a healthy email list.
- Hard Bounces: Immediately remove email addresses that result in hard bounces (permanent delivery failures).
- Soft Bounces: Monitor soft bounces (temporary delivery failures) and remove email addresses that consistently result in soft bounces.
- Unsubscribe Link: Include a clear and easy-to-find unsubscribe link in every email.
- Honor Unsubscribes: Immediately honor unsubscribe requests and remove the email address from your mailing list.
Example: Configure your email marketing platform to automatically remove email addresses that result in a hard bounce. Make sure the unsubscribe link is prominent and works correctly.
Monitoring and Maintaining Sender Reputation
Your sender reputation is a critical asset in the world of email marketing. It’s a score assigned to your sending IP address and domain by email providers, reflecting the trustworthiness of your email program. A good sender reputation increases the likelihood of your emails reaching the inbox, while a poor sender reputation can result in your emails being flagged as spam or even blocked entirely. Regularly monitoring and maintaining your sender reputation is therefore essential for ensuring the long-term success of your email marketing campaigns.
Using Postmaster Tools
Major email providers like Gmail and Outlook offer postmaster tools that provide valuable insights into your sender reputation and email delivery performance. These tools allow you to monitor metrics like spam complaints, bounce rates, and authentication status.
- Gmail Postmaster Tools: Google’s Postmaster Tools provide data on spam rate, IP reputation, domain reputation, feedback loop, authentication, and encryption. You’ll need to verify your domain to access this data.
- Microsoft SNDS (Smart Network Data Services): Microsoft’s SNDS provides information on IP address reputation, spam trap hits, and complaint rates. You’ll need to sign up for SNDS and add your IP addresses to monitor them.
Example: Regularly check Gmail Postmaster Tools to monitor your spam rate. If your spam rate exceeds 0.3%, investigate the cause and take steps to reduce it.
Monitoring Blacklists
Being blacklisted by a major email blacklist provider can severely impact your email deliverability. Regularly monitor your IP address and domain against popular blacklists to identify and address any issues.
- Blacklist Check Tools: Use online blacklist check tools like MXToolbox, MultiRBL, and WhatIsMyIPAddress to check your IP address and domain against multiple blacklists.
- Blacklist Removal Process: If you find your IP address or domain listed on a blacklist, follow the blacklist’s removal process. This typically involves addressing the underlying issue that led to the listing and submitting a delisting request.
Example: Use MXToolbox to check your IP address against various blacklists. If you find your IP listed on Spamhaus, follow Spamhaus’s delisting process to remove it.
Analyzing Bounce Codes
Bounce codes provide valuable information about why your emails are not being delivered. Analyzing these codes can help you identify and address deliverability issues.
- Hard Bounce Codes: Hard bounce codes (e.g., 5.1.1 – User unknown) indicate permanent delivery failures and typically require removing the email address from your list.
- Soft Bounce Codes: Soft bounce codes (e.g., 4.2.1 – Mailbox full) indicate temporary delivery failures and may require further investigation.
- Interpreting Bounce Codes: Consult a list of common SMTP bounce codes to understand the meaning of each code and take appropriate action.
Example: If you see a high number of 5.7.1 bounce codes (Relay access denied), it could indicate that your IP address is being blocked by the recipient’s mail server. Investigate the cause and contact the mail server administrator to request delisting.
| Metric | Importance | How to Monitor | Action if Problematic |
|---|---|---|---|
| Spam Complaint Rate | High | Gmail Postmaster Tools, Feedback Loops | Investigate content, improve targeting, remove complainers |
| Bounce Rate | High | Email Marketing Platform Reporting | Clean email list, address server configuration issues |
| Blacklist Status | High | MXToolbox, MultiRBL | Address the cause, request delisting |
| Authentication Status (SPF, DKIM, DMARC) | High | DMARC Reports, DNS record checks | Correct DNS records, troubleshoot configuration |
