How to Avoid Email Spam Filters: Mastering Authentication
Email marketing and communication are vital for businesses, but landing in the spam folder is a common and frustrating problem. While content plays a role, proper email authentication is the foundation for deliverability. This article delves into the technical aspects of email authentication and provides a detailed guide to implementing SPF, DKIM, and DMARC to significantly improve your email delivery rates and avoid spam filters. We will focus on practical implementation and troubleshooting common issues.
Understanding Email Authentication: SPF, DKIM, and DMARC
Email authentication is a set of standards designed to verify the identity of the sender and prevent spoofing. Spammers often forge the “From” address to impersonate legitimate organizations. SPF, DKIM, and DMARC are three key protocols that work together to combat this and ensure your emails reach their intended recipients. Understanding how they function is crucial before implementing them.
Sender Policy Framework (SPF)
SPF is a DNS record that lists the IP addresses authorized to send emails on behalf of your domain. When a receiving mail server receives an email, it checks the SPF record for the sending domain. If the sending IP address is listed in the SPF record, the email passes the SPF check; otherwise, it fails. This helps prevent spammers from using your domain to send unauthorized emails.
Example: Let’s say your domain is `example.com`, and you send emails from your web server’s IP address `192.0.2.10` and Google Workspace. Your SPF record in your DNS settings would look like this:v=spf1 ip4:192.0.2.10 include:_spf.google.com ~allExplanation:
v=spf1: Specifies the SPF version.ip4:192.0.2.10: Authorizes the IP address 192.0.2.10 to send emails.include:_spf.google.com: Includes Google’s SPF record, allowing Google Workspace to send emails on your behalf.~all: This is a “soft fail” mechanism. If an email doesn’t match the specified IP address or included SPF records, the email will still be accepted, but it will be marked as suspicious. A “hard fail” option would be “-all” which means the email should be rejected. Use “~all” for testing.
include: mechanism. Failure to do so will result in legitimate emails failing the SPF check and potentially being marked as spam.
DomainKeys Identified Mail (DKIM)
DKIM uses cryptographic signatures to verify that an email was sent from an authorized mail server and that the message content hasn’t been altered during transit. When an email is sent, the sending server generates a digital signature based on a private key. The corresponding public key is published in your domain’s DNS records. The receiving server uses the public key to verify the signature. If the signature is valid, it confirms that the email originated from your domain and hasn’t been tampered with.
Example: To set up DKIM for `example.com` using Postfix, you’ll need to install and configure a DKIM signing tool like OpenDKIM. After installing OpenDKIM (instructions vary based on your Linux distribution, so consult your OS documentation), generate a DKIM key pair:opendkim-genkey -t -d example.com -s mailThis command generates two files: mail.private (your private key) and mail.txt (which contains the public key for your DNS record). The `mail` part defines the selector. Next, configure OpenDKIM to use the private key and sign outgoing emails. This involves editing the OpenDKIM configuration file (usually /etc/opendkim.conf):
# /etc/opendkim.conf
Socket inet:12301@localhost
Domain example.com
KeyFile /etc/opendkim/keys/mail.private
Selector mail
Also, configure Postfix to use OpenDKIM for signing. Edit /etc/postfix/main.cf and add the following lines:
# /etc/postfix/main.cf
milter_default_action = accept
milter_protocol = 2
smtpd_milters = inet:127.0.0.1:12301
non_smtpd_milters = inet:127.0.0.1:12301
Finally, add the DKIM public key to your DNS records. The contents of mail.txt will look something like this:
mail._domainkey.example.com. IN TXT ( "v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAy0XW..." )
Create a TXT record named `mail._domainkey.example.com` and paste the value from `mail.txt`.
Expert Tip: Regularly rotate your DKIM keys to enhance security. This involves generating a new key pair, updating your DNS records, and configuring your mail server to use the new private key.Domain-based Message Authentication, Reporting & Conformance (DMARC)
DMARC builds upon SPF and DKIM by specifying how receiving mail servers should handle emails that fail SPF and/or DKIM checks. It allows you to define a policy, such as “reject” (reject emails that fail authentication), “quarantine” (mark them as spam), or “none” (take no action). DMARC also provides reporting, allowing you to receive reports about emails using your domain, including authentication results and potential abuse. This feedback is invaluable for identifying and addressing deliverability issues.
Example: To implement DMARC for `example.com`, you need to create a TXT record named `_dmarc.example.com` in your DNS settings. Here’s a common DMARC record:v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; adkim=r; aspf=r;Explanation:
v=DMARC1: Specifies the DMARC version.p=none: Sets the policy to “none,” meaning receiving servers should take no specific action on emails that fail authentication. This is ideal for initial testing. You will eventually want to change this to “quarantine” or “reject”.rua=mailto:dmarc-reports@example.com: Specifies the email address to which aggregate reports (daily summaries of authentication results) should be sent.ruf=mailto:dmarc-forensic@example.com: Specifies the email address to which forensic reports (detailed information about individual failed emails) should be sent. Use with caution; these can contain personally identifiable information.adkim=r: DKIM alignment mode. ‘r’ means relaxed. The domain in the ‘d=’ tag of the DKIM signature can be a subdomain of the domain in the ‘From:’ header. ‘s’ would mean strict, requiring an exact match.aspf=r: SPF alignment mode. ‘r’ means relaxed. The domain used for the SPF check can be a subdomain of the domain in the ‘From:’ header. ‘s’ would mean strict, requiring an exact match.
After monitoring the reports for a while and ensuring that your legitimate emails are passing authentication, you can gradually tighten your DMARC policy to p=quarantine and then p=reject. This will instruct receiving servers to either mark failing emails as spam or reject them outright, providing the strongest protection against email spoofing.
Configuring DNS Records Correctly: Common Pitfalls and Best Practices
Incorrect DNS configuration is a major reason why email authentication fails. Understanding common pitfalls and following best practices is essential for ensuring your records are valid and effective. Even a small syntax error can render your SPF, DKIM, or DMARC record useless. Careful attention to detail is paramount.
Common SPF Configuration Mistakes
SPF records can be tricky to configure correctly. Here are some common mistakes to avoid:
- Exceeding the 10-lookup limit: SPF records have a limit of 10 DNS lookups, including
include:,a:,mx:,ptr:andexists:mechanisms. Exceeding this limit will cause the SPF check to fail. Avoid using too manyinclude:statements or overly complexa:ormx:mechanisms. Flattening your SPF record can help. This means resolving the included domains and listing the IP addresses directly. This should be done with caution and maintained regularly. - Using the
ptrmechanism: Theptrmechanism is deprecated and should be avoided. It performs a reverse DNS lookup, which is unreliable and can significantly impact performance. - Incorrect syntax: SPF records must adhere to strict syntax rules. Even a small typo can invalidate the entire record. Double-check your syntax carefully.
- Missing the
allmechanism: Every SPF record should end with anallmechanism to specify how to handle emails that don’t match any of the preceding rules. Using-all(hard fail) or~all(soft fail) is important to ensure proper policy enforcement.
v=spf1 include:_spf1.example.com include:_spf2.example.com include:_spf3.example.com include:_spf4.example.com include:_spf5.example.com include:_spf6.example.com include:_spf7.example.com include:_spf8.example.com include:_spf9.example.com include:_spf10.example.com -allThis record has 10 include: mechanisms, which is the maximum allowed. However, if any of those included records also contain include: mechanisms, the total lookup count will exceed 10, causing SPF failures. To fix this, you could investigate each `include` and determine the actual IP addresses that they resolve to. Then, add those IPs directly to your main SPF record, removing the need for multiple lookups.
Common DKIM Configuration Mistakes
DKIM configuration also has its share of potential pitfalls:
- Incorrect key length: Ensure your DKIM key length is sufficient. While 1024-bit keys were once common, 2048-bit keys are now recommended for stronger security.
- Invalid public key syntax: The DKIM public key in your DNS record must be correctly formatted. Ensure there are no typos or extra spaces. The entire key should be a single string, even though it’s long.
- Selector mismatch: The selector specified in your DKIM signature must match the selector used in your DNS record.
- Key not matching: Ensure the private key used for signing matches the public key published in your DNS record. This is a common source of errors during initial setup.
mail._domainkey.example.com. IN TXT ( "v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAy0XW... " )
Notice the extra space at the end of the key (“… “). This seemingly small error will cause the DKIM verification to fail. Remove the space to correct the issue. Also, make sure the key is all on one line, even though it is very long.
Common DMARC Configuration Mistakes
DMARC configuration requires careful planning and monitoring:
- Not starting with
p=none: It’s crucial to start with ap=nonepolicy to monitor your email traffic and identify any legitimate emails that are failing authentication. Jumping straight top=quarantineorp=rejectcan lead to unintended consequences, such as blocking legitimate emails. - Incorrect reporting email address: Ensure the email address specified in the
ruaandruftags is valid and that you are actively monitoring the reports. These reports provide valuable insights into your email authentication performance and potential spoofing attempts. - Missing SPF or DKIM alignment: DMARC requires either SPF or DKIM alignment (or both). Alignment means that the domain used for SPF or DKIM verification matches the domain in the “From” header. If neither SPF nor DKIM is aligned, DMARC will fail.
- Not monitoring DMARC reports: Setting up DMARC is only half the battle. Actively monitoring the aggregate and forensic reports is essential for identifying and addressing deliverability issues and potential security threats.
v=DMARC1; p=reject;This DMARC record sets the policy to “reject” but doesn’t specify a reporting address. Without reports, you won’t know if legitimate emails are being incorrectly rejected. Always include `rua` and `ruf` addresses, even if you are initially only monitoring them infrequently. You may want to set up a dedicated email address specifically for these reports.
Best Practice: Use a DMARC record validator to check your DMARC record for syntax errors and other issues. Several free online tools can help you identify and correct potential problems.Troubleshooting Email Authentication Failures: Identifying and Resolving Issues
Even with careful configuration, email authentication failures can still occur. Knowing how to identify and resolve these issues is crucial for maintaining good email deliverability. Start by examining the headers of emails that are being marked as spam. These headers often contain information about why the authentication checks failed.
Analyzing Email Headers for Authentication Results
Email headers contain valuable information about the path an email took and the authentication checks it underwent. Look for headers like “Authentication-Results,” “Received-SPF,” and “DKIM-Signature.” These headers provide details about the SPF, DKIM, and DMARC results. The exact headers and their format may vary depending on the receiving mail server.
Example: An “Authentication-Results” header might look like this:Authentication-Results: mx.google.com;
dkim=pass header.i=@example.com header.s=mail header.b=abc123xyz;
spf=pass (google.com: domain of sender@example.com designates 192.0.2.10 as permitted sender) client-ip=192.0.2.10;
dmarc=pass (p=none sp=none dis=none) dmarc.domain=example.com header.from=example.com
In this example, DKIM, SPF, and DMARC all passed. The dkim=pass indicates that the DKIM signature was successfully verified. The spf=pass indicates that the sending IP address (192.0.2.10) is authorized to send emails on behalf of `example.com`. The dmarc=pass indicates that the DMARC policy was satisfied.
Authentication-Results: mx.google.com;
dkim=neutral (bad key) header.i=@example.com header.s=mail header.b=abc123xyz;
spf=fail (google.com: domain of sender@example.com does not designate 192.0.2.11 as permitted sender) client-ip=192.0.2.11;
dmarc=fail (p=none sp=none dis=none) dmarc.domain=example.com header.from=example.com
In this case, DKIM is “neutral” (likely meaning invalid or missing key), SPF failed because the sending IP address (192.0.2.11) is not authorized, and DMARC failed because at least one of DKIM or SPF must pass *and* be aligned with the ‘From:’ domain. The fixes would involve making sure the DKIM key is valid and the IP address 192.0.2.11 is added to the SPF record.
Troubleshooting SPF Failures
If your emails are failing SPF checks, here are some steps you can take to troubleshoot the issue:
- Verify your SPF record: Use an online SPF record validator to check your SPF record for syntax errors.
- Check the sending IP address: Ensure that the IP address of the mail server sending the email is included in your SPF record.
- Check for SPF record limitations: Make sure your SPF record doesn’t exceed the 10-lookup limit.
- Verify includes: Ensure that any `include:` statements in your SPF record are correctly configured and that the included domains have valid SPF records.
v=spf1 ip4:192.0.2.10 ip4:203.0.113.0/24 include:_spf.google.com ~allIn this example, ip4:203.0.113.0/24 adds the CRM system’s IP address range to the SPF record. You should get the specific IP address range directly from the CRM provider’s documentation.
Troubleshooting DKIM Failures
If your emails are failing DKIM checks, consider the following:
- Verify your DKIM record: Use an online DKIM record validator to check your DKIM record for syntax errors and ensure that the public key is valid.
- Check the selector: Ensure that the selector specified in your DKIM signature matches the selector used in your DNS record.
- Verify key matching: Ensure that the private key used for signing matches the public key published in your DNS record.
- Check for message alteration: Ensure that the email message is not being altered during transit. Some email servers or security appliances may modify the message content, which can invalidate the DKIM signature. Things like adding footers or disclaimers can break the DKIM signature.
Troubleshooting DMARC Failures
If your emails are failing DMARC checks, the following steps might help:
- Review DMARC reports: Analyze your DMARC reports to identify the source of the failures and the specific emails that are failing authentication.
- Verify SPF and DKIM alignment: Ensure that either SPF or DKIM is aligned with the domain in the “From” header.
- Check your DMARC policy: Ensure that your DMARC policy is appropriate for your current email authentication setup. Starting with
p=noneis recommended until you have a good understanding of your email traffic. - Investigate third-party senders: If you use third-party services to send emails, ensure that they are properly configured to authenticate emails on your behalf.
Beyond Authentication: Content and Reputation Factors
While proper email authentication is crucial, it’s not the only factor that determines whether your emails land in the inbox or the spam folder. Content and sender reputation also play significant roles. Even with perfect SPF, DKIM, and DMARC configurations, poor content or a bad reputation can still lead to deliverability issues. Think of authentication as the foundation, and content/reputation as the walls and roof.
Crafting Spam-Free Email Content
The content of your emails can significantly impact their deliverability. Avoid using spam trigger words, excessive punctuation, and misleading subject lines. Focus on providing valuable and relevant information to your recipients. Here are some content-related best practices:
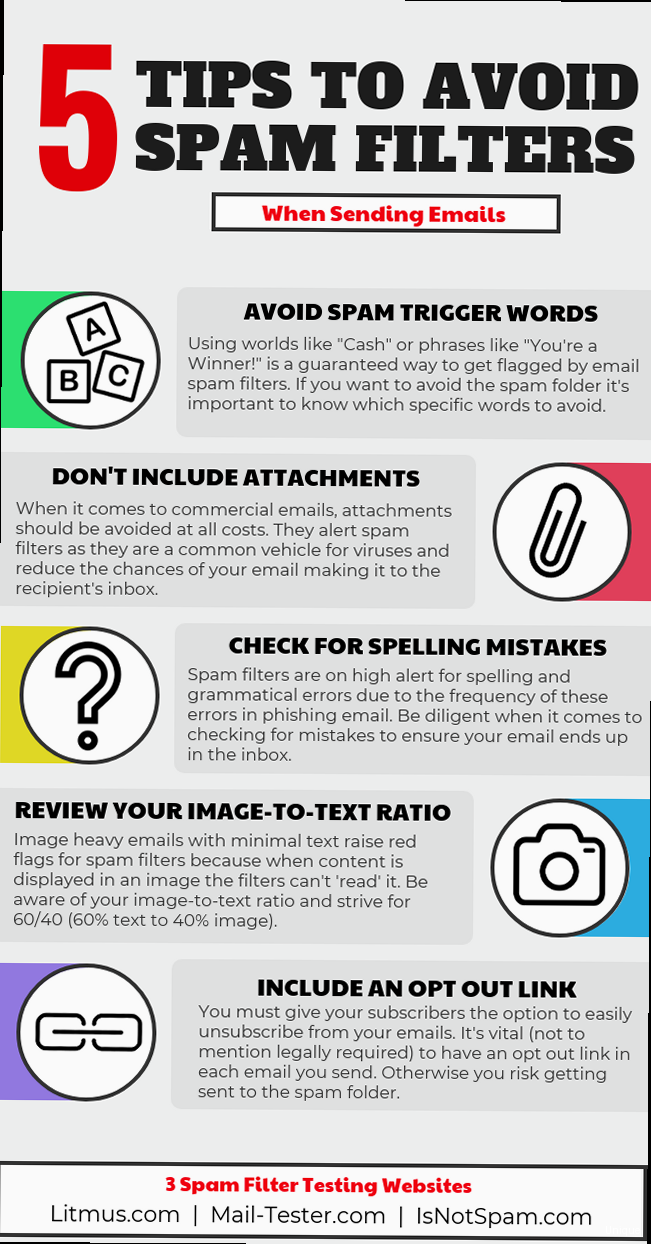
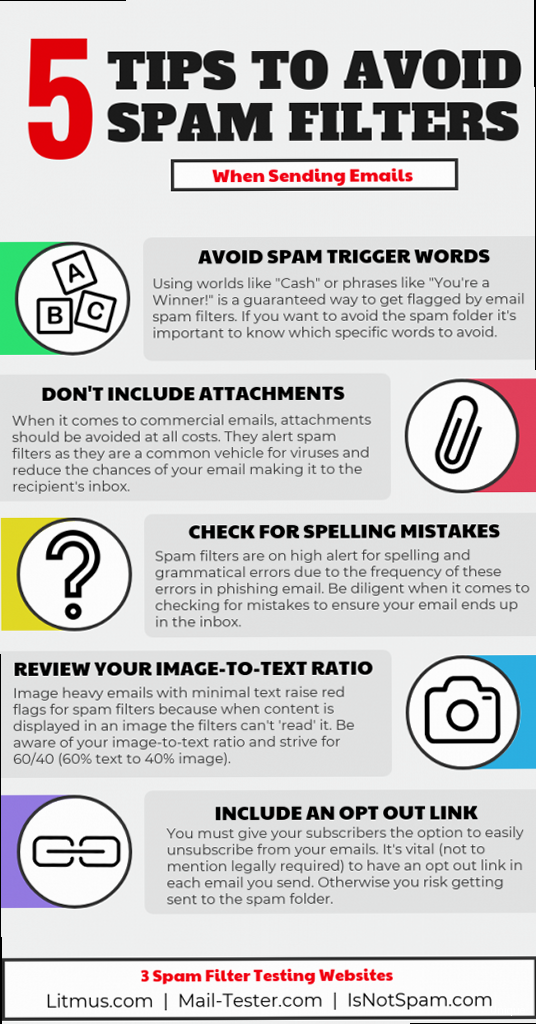
- Avoid spam trigger words: Words like “free,” “guarantee,” “urgent,” and “limited time offer” are often used in spam emails and can trigger spam filters. Use these words sparingly or avoid them altogether.
- Use proper formatting: Avoid using excessive capitalization, exclamation points, or unusual fonts. Use clear and concise language and format your emails in a professional manner.
- Avoid excessive links: Too many links in an email can raise red flags with spam filters. Limit the number of links and ensure that they are relevant and trustworthy.
- Personalize your emails: Personalization can improve engagement and reduce the likelihood of your emails being marked as spam. Use your recipients’ names and tailor the content to their interests.
- Use a clear call to action: Make it clear what you want your recipients to do, whether it’s visiting your website, making a purchase, or signing up for a newsletter.
This subject line is full of spam trigger words and excessive capitalization. A better subject line would be something like: “Exclusive Offer for Our Valued Customers” or “Learn More About Our New Product.”
Building and Maintaining a Good Sender Reputation
Your sender reputation is a measure of your trustworthiness as an email sender. It’s based on factors like your IP address, domain, and sending history. A good sender reputation can significantly improve your email deliverability, while a bad reputation can lead to your emails being blocked or marked as spam. Here’s how to build and maintain a good sender reputation:
- Use a dedicated IP address: Using a dedicated IP address gives you more control over your sender reputation. Avoid using shared IP addresses, as the actions of other senders can affect your reputation.
- Warm up your IP address: If you’re using a new IP address, gradually increase your sending volume over time to establish a good reputation. Sending too many emails too quickly can raise red flags with spam filters.
- Authenticate your emails: Implement SPF, DKIM, and DMARC to verify your identity and prevent spoofing.
- Maintain a clean email list: Regularly remove inactive or invalid email addresses from your list. Sending emails to non-existent addresses can damage your sender reputation.
- Monitor your bounce rates: High bounce rates can indicate that your email list is outdated or that you’re sending emails to invalid addresses. Monitor your bounce rates and take steps to reduce them.
- Encourage recipients to report spam: Make it easy for recipients to unsubscribe from your emails and report spam. This will help you identify and address any issues that may be affecting your deliverability.
- Comply with CAN-SPAM Act: Ensure your emails comply with the CAN-SPAM Act. This includes providing a clear and conspicuous way for recipients to unsubscribe from your emails, including a valid physical postal address in your emails, and accurately representing the content of your emails in the subject line.
| Factor | Good Impact on Deliverability | Bad Impact on Deliverability |
|---|---|---|
| Authentication (SPF, DKIM, DMARC) | Properly configured and passing | Missing or failing checks |
| Content | Relevant, personalized, well-formatted | Spam trigger words, excessive links, poor formatting |
| Sender Reputation | High engagement, low bounce rates, low spam complaints | Blacklisted IP address, high bounce rates, high spam complaints |
| List Hygiene | Regularly cleaned, engaged subscribers | Outdated, invalid addresses, purchased lists |
By focusing on both technical aspects like email authentication and softer factors like content and reputation, you significantly increase your chances of avoiding spam filters and reaching your intended audience.
External Link: For more information on CAN-SPAM compliance, visit the FTC website: https://www.ftc.gov/tips-advice/business-center/guidance/can-spam-act-compliance-guide-business
