Email Advertising Tips to Avoid Email marketing secrets to avoid spam filters?">Spam Filters
Email marketing can be a powerful tool, but it’s only effective if your messages reach the intended recipients’ inboxes. Spam filters are constantly evolving, making it challenging to consistently land in the primary inbox. This article provides practical, actionable strategies to improve your email deliverability and avoid being marked as spam, focusing on key technical and content-related aspects of email marketing.
Table of Contents
- Email Authentication: Setting Up SPF, DKIM, and DMARC
- Crafting High-Quality Email Content to Bypass Spam Filters
- Effective Email List Management and Hygiene Practices
- Technical Configuration for Optimal Email Deliverability
- Monitoring and Maintaining Your Sender Reputation
Email Authentication: Setting Up SPF, DKIM, and DMARC
SPF (Sender Policy Framework)
SPF specifies which mail servers are authorized to send emails on behalf of your domain. By creating an SPF record in your DNS settings, you’re telling receiving servers to only accept emails from the listed IPs. This significantly reduces the chance of spammers forging your email address. Example: Let’s say your domain is `example.com`, and you send emails using Google Workspace (Gmail) and your own server with the IP address `203.0.113.45`. Here’s how you would create an SPF record:v=spf1 include:_spf.google.com ip4:203.0.113.45 -all- `v=spf1`: Specifies the SPF version.
- `include:_spf.google.com`: Includes Google’s SPF records, allowing them to send emails on your behalf.
- `ip4:203.0.113.45`: Allows the server with this IP address to send emails.
- `-all`: Specifies that any server not listed is not authorized, and emails from them should be rejected. Using `-all` is generally recommended for stricter security. You could also use `~all` which means softfail and the receiving server is more lenient.
- Log in to your domain registrar’s DNS management panel.
- Create a new TXT record.
- In the “Name/Host” field, enter `@` or leave it blank (depending on your registrar).
- In the “Value/Text” field, paste the SPF record.
- Save the record.
DKIM (DomainKeys Identified Mail)
DKIM adds a digital signature to your email’s header. This signature is encrypted using your private key and verified by receiving servers using your public key, which is stored in your DNS records. DKIM ensures that the email’s content hasn’t been altered during transit and confirms the sender’s identity. Example: Generating a DKIM key involves several steps, usually handled through your email sending service or server. Here’s a simplified example of how you might add the DKIM record to your DNS, *after* you’ve generated the key pair: Let’s say your selector is `s1` and the public key provided by your email service is `MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC4bV…`. You would add a TXT record like this:s1._domainkey.example.com. IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC4bV..."- `s1._domainkey.example.com`: Specifies the hostname for the DKIM record, including the selector (`s1`) and the domain.
- `IN TXT`: Indicates that this is a TXT record.
- `v=DKIM1`: Specifies the DKIM version.
- `k=rsa`: Specifies the key type (RSA).
- `p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC4bV…`: The public key. This is a shortened version. Your actual key will be much longer.
- Go to the Google Admin console.
- Navigate to Apps -> Google Workspace -> Gmail -> Authenticate email.
- Select your domain and click “Generate new record.”
- Copy the generated TXT record (hostname and value).
- Add the record to your domain’s DNS settings.
DMARC (Domain-based Message Authentication, Reporting & Conformance)
DMARC builds upon SPF and DKIM by specifying how receiving servers should handle emails that fail authentication. It allows you to set policies such as “none,” “quarantine,” or “reject” and provides reporting to help you monitor your email authentication performance. DMARC is essential for protecting your domain from phishing and spoofing attacks. Example: Here’s a DMARC record that requests email providers to quarantine failing emails and send reports to a specific email address:_dmarc.example.com. IN TXT "v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com; adkim=r; aspf=r;"- `_dmarc.example.com`: Specifies the hostname for the DMARC record.
- `v=DMARC1`: Specifies the DMARC version.
- `p=quarantine`: Sets the policy to “quarantine.” Emails that fail SPF and DKIM checks should be marked as spam or placed in a quarantine folder. Other options include `p=reject` (reject failing emails) and `p=none` (monitor only, no action taken).
- `rua=mailto:dmarc-reports@example.com`: Specifies the email address to which aggregate reports should be sent. These reports provide insights into your email authentication performance.
- `adkim=r`: DKIM alignment mode. ‘r’ means relaxed, allowing for subdomain mismatches. ‘s’ means strict.
- `aspf=r`: SPF alignment mode. ‘r’ means relaxed, allowing for subdomain mismatches. ‘s’ means strict.
- Start with a `p=none` policy to monitor your email flow without impacting deliverability.
- Analyze the DMARC reports to identify any authentication issues and adjust your SPF and DKIM configurations accordingly.
- Gradually move to a stricter policy (`p=quarantine` or `p=reject`) once you’re confident that your email authentication is properly configured.
Crafting High-Quality Email Content to Bypass Spam Filters
 subject lines, personalized messages, clear calls to action, and mobile-friendly design." title="Illustration for A graphic illustrating the key elements of high-quality email content: relevant subject lines, personalized messages, clear calls to action, and mobile-friendly design." width="512" height="512" / class="wp-image-252 wp-image-12401">
subject lines, personalized messages, clear calls to action, and mobile-friendly design." title="Illustration for A graphic illustrating the key elements of high-quality email content: relevant subject lines, personalized messages, clear calls to action, and mobile-friendly design." width="512" height="512" / class="wp-image-252 wp-image-12401">Subject Line Optimization
Your subject line is the first impression you make on your subscribers. A poorly crafted subject line can trigger spam filters and deter recipients from opening your email. Examples of subject lines to avoid:- “FREE! Get yours now!”
- “URGENT: Claim your prize!”
- “Act now or miss out!”
- “Earn $$$ working from home!”
- “Exclusive Discount for Our Valued Customers”
- “New Blog Post: [Topic]”
- “Quick Question About Your [Product/Service] Experience”
- “Invitation to Our Upcoming Webinar”
- Keep it short and sweet (under 50 characters).
- Avoid spam trigger words and phrases.
- Use personalization (e.g., including the recipient’s name).
- Clearly communicate the email’s purpose.
- Test different subject lines to see what works best.
Content Formatting and Structure
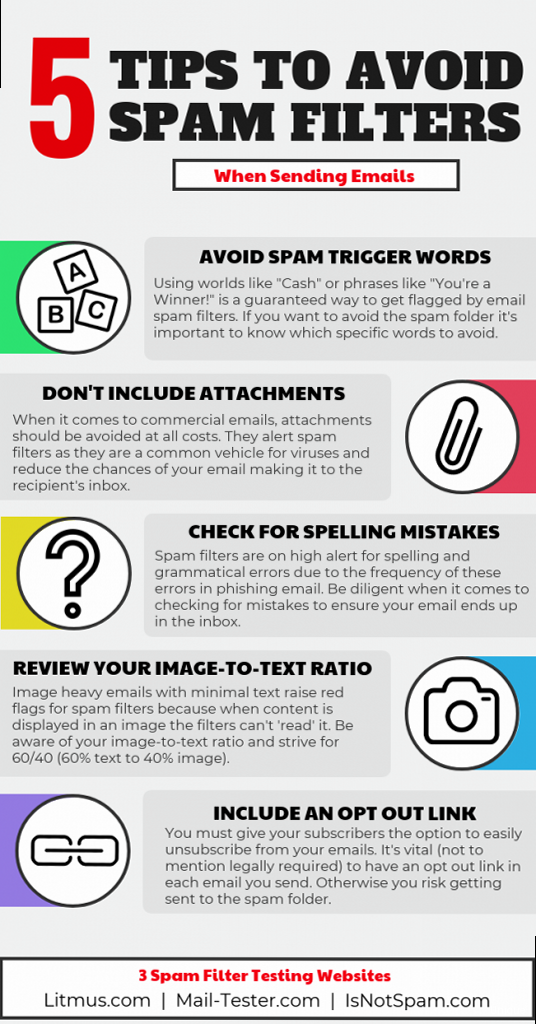
The way you format and structure your email content can also impact deliverability. Spam filters are more likely to flag emails with poor formatting, excessive use of images, and broken links. Example of poorly formatted email content: Imagine an email with a single large image, very little text, and a bunch of generic links. This is a red flag for spam filters because it lacks context and appears unprofessional. Example of well-formatted email content: A well-formatted email would include:- A clear and concise introduction.
- Well-structured paragraphs with headings and subheadings.
- A balance of text and images.
- Alt text for all images.
- Clear and prominent calls to action.
- A working unsubscribe link.
- Use a clean and professional email template.
- Maintain a healthy text-to-image ratio (aim for at least 60% text).
- Optimize images for web use (reduce file size).
- Use alt text for images to provide context.
- Test your email on different devices and email clients.
- Check for broken links and spelling errors.
Avoiding Spam Trigger Words and Phrases
Certain words and phrases are commonly associated with spam and can trigger spam filters. Avoid using these words excessively or in misleading ways. Examples of spam trigger words:- Free
- Urgent
- Guarantee
- Opportunity
- Winner
- Act now
- Click here
- Password
- Credit card
- Instead of “Free,” use “Complimentary” or “Bonus.”
- Instead of “Urgent,” use “Important” or “Time-Sensitive.”
- Instead of “Guarantee,” use “Commitment” or “Promise.”
“Email marketing is not about blasting your message to as many people as possible. It’s about building relationships with your subscribers and providing them with value.”
Neil Patel, Digital Marketing Expert
Effective Email List Management and Hygiene Practices
Building and maintaining a healthy email list is paramount for deliverability. Sending emails to outdated, inactive, or unengaged subscribers significantly increases your spam complaints and damages your sender reputation. Effective list management and hygiene practices are essential for ensuring your messages reach interested recipients.Obtaining Consent and Using Double Opt-In
The foundation of a healthy email list is obtaining explicit consent from subscribers before sending them any emails. Using a double opt-in process ensures that subscribers genuinely want to receive your messages. Single opt-in vs. double opt-in:| Feature | Single Opt-In | Double Opt-In |
|---|---|---|
| Subscription Process | Subscriber enters email address and is immediately added to the list. | Subscriber enters email address and receives a confirmation email with a link to verify their subscription. |
| Verification | No verification of email address ownership. | Requires verification of email address ownership. |
| List Quality | Lower quality, may contain typos or invalid addresses. | Higher quality, more likely to contain valid and engaged subscribers. |
| Deliverability | Lower deliverability due to higher spam complaints. | Higher deliverability due to lower spam complaints. |
| Legality | May not comply with GDPR and other privacy regulations. | More likely to comply with GDPR and other privacy regulations. |
- A user enters their email address on your website’s signup form.
- The user receives an email with a confirmation link (e.g., “Confirm your subscription”).
- The user clicks the confirmation link to verify their email address.
- The user is then added to your email list.
- Reduces the risk of spam complaints.
- Improves email deliverability.
- Ensures compliance with privacy regulations (e.g., GDPR).
- Builds a more engaged and responsive subscriber base.
Regularly Cleaning Your Email List
Over time, email lists naturally degrade as subscribers change email addresses, lose interest, or mark emails as spam. Regularly cleaning your email list is crucial for maintaining its health and improving deliverability. Methods for cleaning your email list:- Remove hard bounces: Hard bounces indicate permanent delivery failures (e.g., invalid email address). These addresses should be removed immediately.
- Remove unsubscribes: Honor all unsubscribe requests promptly. Failing to do so can lead to spam complaints and legal issues.
- Identify and remove inactive subscribers: Subscribers who haven’t opened or clicked on your emails in a certain period (e.g., 6-12 months) are likely inactive. Consider sending them a re-engagement campaign or removing them from your list.
- Use email validation services: These services can help identify invalid, risky, or disposable email addresses before you even send them an email.
Segmentation and Targeting
Instead of sending the same email to your entire list, segment your subscribers based on their demographics, interests, behavior, or purchase history. This allows you to send more targeted and relevant emails, which increases engagement and reduces the likelihood of spam complaints. Examples of email list segmentation:- Demographic segmentation: Segmenting subscribers based on age, gender, location, or job title.
- Interest-based segmentation: Segmenting subscribers based on their expressed interests or preferences.
- Behavioral segmentation: Segmenting subscribers based on their past interactions with your emails or website (e.g., opened emails, clicked links, purchased products).
- Purchase history segmentation: Segmenting subscribers based on their past purchases.
Technical Configuration for Optimal Email Deliverability
Beyond authentication and content, certain technical configurations play a vital role in email deliverability. Proper setup of your sending infrastructure, including IP addresses, reverse DNS records, and feedback loops, can significantly impact whether your emails land in the inbox or the spam folder.IP Address Reputation and Warming Up
Your sending IP address has a reputation that influences your email deliverability. A new IP address has no established reputation, so it’s crucial to “warm it up” gradually before sending large volumes of emails. IP address warming process:- Start with a small volume of emails: Begin by sending emails to your most engaged subscribers.
- Gradually increase the sending volume over time: Monitor your deliverability metrics (e.g., open rates, bounce rates, spam complaints) and adjust your sending volume accordingly.
- Maintain consistent sending patterns: Avoid sudden spikes in sending volume.
- Engage with recipients: Encourage recipients to add your email address to their address book and mark your emails as “not spam.”
| Day | Volume | Target Audience |
|---|---|---|
| Day 1-3 | 500 emails | Most engaged subscribers |
| Day 4-7 | 1,000 emails | Engaged subscribers |
| Day 8-14 | 2,500 emails | Active subscribers |
| Day 15-21 | 5,000 emails | Subscribers who have opened emails in the last 3 months |
| Day 22-30 | 10,000+ emails | Remaining subscribers |
Reverse DNS (rDNS) Configuration
Reverse DNS (rDNS) maps an IP address to a domain name. It helps verify that the IP address is associated with the sending domain and is not being used for spamming. Configuring rDNS is an important step in establishing your sender reputation. How to configure rDNS:- Contact your ISP or hosting provider to request the rDNS record for your sending IP address.
- Provide them with your domain name (e.g., mail.example.com).
- They will create the rDNS record, which maps your IP address to your domain name.
dig -x 203.0.113.45; <<>> DiG 9.11.5-P4-5.1+deb10u2 <<>> -x 203.0.113.45
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52805
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;45.113.0.203.in-addr.arpa. IN PTR
;; ANSWER SECTION:
45.113.0.203.in-addr.arpa. 3600 IN PTR mail.example.com.
;; Query time: 0 msec
;; SERVER: 1.1.1.1#53(1.1.1.1)
;; WHEN: Sun Jan 01 12:00:00 2024
;; MSG SIZE rcvd: 91
Setting Up Feedback Loops (FBLs)
Feedback loops (FBLs) provide you with information about spam complaints from recipients. By subscribing to FBLs with major ISPs, you can identify subscribers who are marking your emails as spam and remove them from your list. This helps reduce your spam complaint rate and improve your sender reputation. How to set up FBLs:- Identify the FBL programs offered by major ISPs (e.g., Gmail, Outlook, Yahoo).
- Register your sending IP address with each FBL program.
- Configure your email system to include a unique identifier in the email headers. This identifier allows the ISP to associate the spam complaint with a specific subscriber.
- Process the FBL reports and remove the complaining subscribers from your list.
- Implement the `List-Unsubscribe` header in your emails: This allows recipients to easily unsubscribe from your emails, reducing the likelihood of them marking your emails as spam.
- Register with Gmail’s Postmaster Tools and verify your domain. This gives you access to data about your email deliverability and spam complaints.
List-Unsubscribe: <mailto:unsubscribe@example.com>, <https://www.example.com/unsubscribe>
- `mailto:unsubscribe@example.com`: Provides a one-click unsubscribe option.
- `https://www.example.com/unsubscribe`: Provides a web-based unsubscribe option.
Monitoring and Maintaining Your Sender Reputation
Your sender reputation is a crucial factor in determining your email deliverability. It’s a measure of how trustworthy email providers perceive you to be, based on your sending behavior and the feedback they receive from recipients. Regularly monitoring and maintaining your sender reputation is essential for ensuring that your emails consistently reach the inbox.Key Metrics to Track
Several key metrics provide insights into your sender reputation and email deliverability performance. Monitoring these metrics regularly allows you to identify and address any potential issues before they negatively impact your ability to reach your subscribers.- Open Rate: The percentage of recipients who opened your email. A low open rate may indicate that your subject lines are not compelling or that your emails are being filtered into the spam folder.
- Click-Through Rate (CTR): The percentage of recipients who clicked on a link in your email. A low CTR may indicate that your content is not engaging or relevant to your subscribers.
- Bounce Rate: The percentage of emails that failed to be delivered. A high bounce rate can damage your sender reputation. Hard bounces (invalid email addresses) should be removed immediately. Soft bounces (temporary delivery failures) may indicate temporary server issues or full mailboxes.
- Spam Complaint Rate: The percentage of recipients who marked your email as spam. A high spam complaint rate is a major red flag for email providers and can lead to your emails being blocked.
- Unsubscribe Rate: The percentage of recipients who unsubscribed from your email list. A high unsubscribe rate may indicate that your content is not relevant or that you are sending emails too frequently.
- Delivery Rate: The percentage of emails that were successfully delivered to recipients’ inboxes. This is arguably the most important metric.
- Open Rate: 15-25%
- CTR: 2-5%
- Bounce Rate: Under 2%
- Spam Complaint Rate: Under 0.1% (ideally, significantly lower)
- Unsubscribe Rate: Under 0.5%
- Log in to Google Postmaster Tools.
- Select your domain.
- Review the dashboards for “Spam Rate,” “IP Reputation,” “Domain Reputation,” and “Feedback Loop.”
- Identify any issues and take corrective action.
Using Postmaster Tools and Monitoring Services
Several tools and services can help you monitor your sender reputation and email deliverability. These tools provide valuable insights into your sending performance and help you identify and address any potential issues.- Google Postmaster Tools: A free service that provides data on your email deliverability to Gmail users.
- Microsoft SNDS (Smart Network Data Services): A free service that provides data on your email deliverability to Outlook.com users.
- Third-party monitoring services: Several commercial services offer more comprehensive monitoring and analysis of your sender reputation and email deliverability across multiple ISPs. Examples include Return Path, Validity, and 250ok.
- Check your sending volume: Did you recently send a large email
