dig txt example.comdig txt example.comnslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
dig txt example.comnslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
nslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
SPF Record Configuration for Google Hosted Email
Ensuring proper email deliverability is crucial for any organization relying on Google Workspace (formerly G Suite). A Sender Policy Framework (SPF) record is a vital DNS record that helps prevent spammers from forging your domain in the “From” address. This article provides a comprehensive guide to configuring an SPF record specifically for Google-hosted email, covering common scenarios, troubleshooting tips, and best practices to maximize email delivery rates and minimize the risk of your emails being marked as spam. We’ll delve into practical examples and provide step-by-step instructions to ensure your SPF record is correctly configured and effective.
Table of Contents:
- Understanding SPF and Its Importance
- Creating Your SPF Record for Google Workspace
- Handling Multiple Senders and Third-Party Services
- Testing and Validating Your SPF Record
- Troubleshooting Common SPF Issues
Understanding SPF and Its Importance
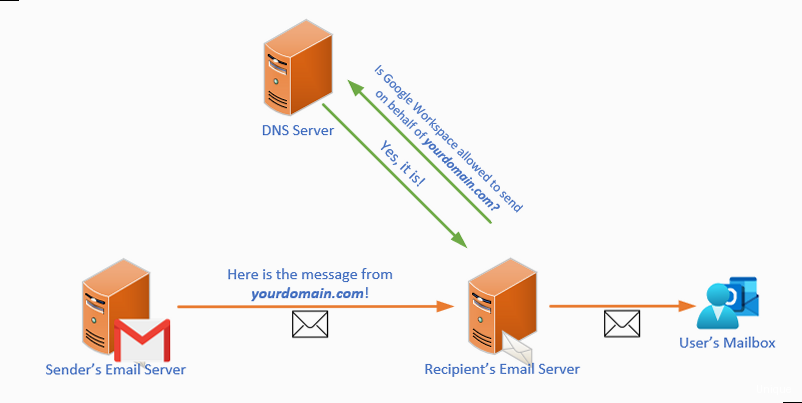
- Email Deliverability: ISPs and email providers use SPF as one factor in determining whether to deliver emails to the inbox or mark them as spam.
- Domain Reputation: Protecting your domain from being used in spam campaigns maintains a positive reputation, leading to better deliverability across all email services.
- Brand Protection: Preventing phishing attacks that impersonate your brand helps maintain customer trust and avoids potential financial or reputational damage.
- Compliance: Some regulations and industry standards require email authentication measures like SPF.
v=spf1 [mechanisms] [modifiers]- v=spf1: This is the version of SPF being used. It’s mandatory and must be the first element in the record.
- Mechanisms: These define the authorized sending sources. Common mechanisms include:
ip4:Specifies an IPv4 address or range. Example:ip4:192.0.2.0/24ip6:Specifies an IPv6 address or range. Example:ip6:2001:db8::/32a:Specifies the IP address(es) of the domain’s A record. Example:a:example.commx:Specifies the IP address(es) of the domain’s MX record(s). Example:mx:example.cominclude:Includes another domain’s SPF record. This is crucial for Google Workspace. Example:include:_spf.google.comexists:Checks if a given domain name resolves. Rarely used directly. Example:exists:%{s}.example.com
- Qualifiers: Precede each mechanism and determine how the check is handled:
+(Pass): Explicitly allows the sending server (default if no qualifier is specified).-(Fail): Explicitly denies the sending server. Recipient servers should reject the email.~(SoftFail): Indicates the email might be from an unauthorized source, but the recipient server should accept it with a warning (e.g., mark it as spam).?(Neutral): Indicates the domain owner makes no assertion about whether the sending server is authorized. Effectively disables SPF checking.
- Modifiers: Provide additional instructions or information.
redirect=:Redirects the SPF check to another domain’s SPF record. Example:redirect=example.netexp=:Provides an explanation string for why an email failed the SPF check (rarely used). Example:exp=email.example.com
- all: Matches all IP addresses. It’s usually placed at the end of the record and used with a qualifier to define the default behavior for addresses not matched by other mechanisms. Common uses:
-all: Fail all unmatched addresses (strict policy).~all: SoftFail all unmatched addresses (more lenient).?all: Neutral for all unmatched addresses (effectively disables SPF).
v=spf1 include:_spf.google.com -all- Only one SPF record per domain: Having multiple SPF records can cause issues with SPF evaluation. If you need to include multiple sources, combine them into a single record.
- The 10-lookup limit: SPF records can include nested `include:` mechanisms. However, the total number of DNS lookups performed during an SPF evaluation is limited to 10. Exceeding this limit can cause SPF checks to fail. Try to consolidate your SPF record to minimize lookups.
- Prioritize security: Use the `-all` mechanism at the end of your record to enforce a strict policy and reject unauthorized emails. If you’re unsure, `~all` (SoftFail) is a safer initial option.
Creating Your SPF Record for Google Workspace
- Google Workspace Servers: This is the primary source when using Google Workspace for email. You’ll use the
include:_spf.google.commechanism to authorize these servers. - Web Servers: If your website sends emails (e.g., contact form submissions, password reset emails), you need to include the IP address of your web server or use the
aormxmechanisms if the server is associated with your domain. - Marketing Automation Platforms: If you use services like Mailchimp, SendGrid, or HubSpot, you’ll need to include their SPF records using the
include:mechanism they provide. - Transactional Email Services: Services like Sendinblue or Amazon SES also require including their SPF records.
- On-Premise Email Servers: If you have any on-premise email servers that send email for your domain, you need to include their IP addresses or hostnames.
v=spf1 include:_spf.google.com- Adding a web server with IP address 192.0.2.10:
v=spf1 include:_spf.google.com ip4:192.0.2.10 -all- Adding Mailchimp: (Replace `servers.mcsv.net` with the correct value for your Mailchimp account if different).
v=spf1 include:_spf.google.com include:servers.mcsv.net -all- Adding SendGrid:
v=spf1 include:_spf.google.com include:sendgrid.net -allv=spf1 include:_spf.google.com include:servers.mcsv.net -all- Log in to your domain registrar or hosting provider’s control panel.
- Navigate to the DNS management section. This might be called “DNS Zone Editor,” “DNS Records,” or something similar.
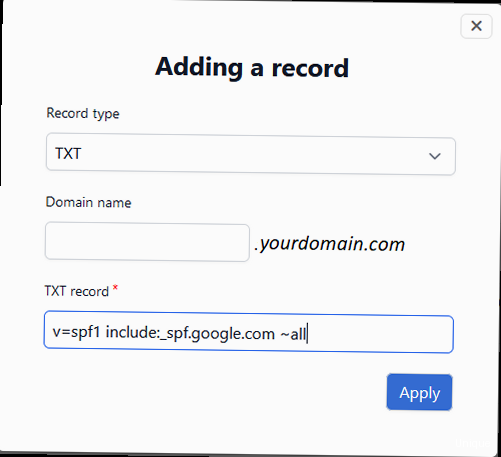
- Create a new TXT record.
- Enter the following values:
- Host/Name: Enter
@or leave it blank to apply the record to the root domain (e.g., example.com). If you’re creating the record for a subdomain (e.g., mail.example.com), enter the subdomain. - Type: Select
TXT. - Value/Text: Enter the SPF record you constructed in Step 2 (e.g.,
v=spf1 include:_spf.google.com include:servers.mcsv.net -all). - TTL (Time to Live): This determines how long DNS servers cache the record. The default TTL is usually fine (e.g., 3600 seconds or 1 hour).
- Host/Name: Enter
- Save the record.
- Log in to Google Domains.
- Select your domain.
- Click on “DNS.”
- Scroll down to “Custom resource records.”
- Enter the following:
- Name:
@ - Type:
TXT - TTL:
3600 - Data:
v=spf1 include:_spf.google.com include:servers.mcsv.net -all
- Name:
- Click “Add.”
- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/
- SPF Record Testing Tools: Search Google for “SPF record checker” to find other options.
- Go to https://mxtoolbox.com/spf.aspx.
- Enter your domain name (e.g., example.com).
- Click “SPF Record Lookup.”
Handling Multiple Senders and Third-Party Services
In today’s digital landscape, it’s common for organizations to use multiple services for sending emails, including Google Workspace, marketing automation platforms, transactional email services, and more. Managing SPF records for these diverse senders can be complex. This section provides guidance on how to create a comprehensive SPF record that authorizes all your legitimate sending sources while maintaining optimal email deliverability. The `include:` Mechanism: Delegation is Key The `include:` mechanism is the cornerstone of managing multiple senders. It allows you to delegate the responsibility of specifying authorized sending servers to the third-party service itself. Instead of manually adding IP addresses for each service, you simply include their SPF record in your own. This makes maintenance much easier, as the service provider is responsible for keeping their SPF record up-to-date. Example:v=spf1 include:_spf.google.com include:servers.mcsv.net include:sendgrid.net -all- Mailchimp: Search their help documentation for “SPF record” or “email authentication.” The correct value is usually
include:servers.mcsv.net(but verify this for your specific account). - SendGrid: Search their help documentation for “SPF record.” The correct value is
include:sendgrid.net. - HubSpot: Search their help documentation for “SPF record.” The correct value is
include:hs-spf.hubspotemail.net. - Amazon SES: The correct value depends on the AWS region you’re using. Refer to the Amazon SES documentation for the correct
include:value for your region (e.g.,include:amazonses.comfor the default region). - Sendinblue: The correct value is
include:spf.sendinblue.com.
v=spf1 include:_spf.google.com include:servers.mcsv.net include:sendgrid.net include:hs-spf.hubspotemail.net include:spf.sendinblue.com -all- Minimize `include:` statements: Only include the SPF records for services you actively use. Remove any unused or outdated `include:` statements.
- Flatten your SPF record (Use with Caution): Instead of using `include:`, you can manually add the IP addresses of the sending servers directly to your SPF record using the `ip4:` and `ip6:` mechanisms. However, this is generally not recommended because it requires you to manually update your SPF record whenever the service provider changes their sending infrastructure. It’s also time-consuming and error-prone. This method is generally advised against unless absolutely necessary.
- Use a dedicated email sending domain or subdomain: If you are using a large number of third-party senders, consider using a separate domain or subdomain (e.g., `mail.example.com`) specifically for sending email. This allows you to create a separate SPF record for that subdomain with only the necessary `include:` statements. This isolates the impact of the 10-lookup limit to that subdomain.
- Use SPF Record Checkers: Use online SPF record checkers (like MXToolbox) to verify that your SPF record is valid and doesn’t exceed the 10-lookup limit.
- Send Test Emails: Send test emails from each of your sending sources (Google Workspace, Mailchimp, SendGrid, etc.) to an email address you control (e.g., a Gmail account). Check the email headers to confirm that the SPF check passed.
- Monitor Email Deliverability: Pay attention to your email deliverability rates. If you notice a sudden drop in deliverability, it could indicate an issue with your SPF record.
- Use DMARC Reporting: Implement DMARC (Domain-based Message Authentication, Reporting & Conformance) and enable DMARC reporting. DMARC reports provide valuable insights into how your emails are being authenticated and whether SPF and DKIM (DomainKeys Identified Mail) are passing. This allows you to identify and address any authentication issues.
Testing and Validating Your SPF Record
Once you’ve created or modified your SPF record, rigorous testing and validation are essential to ensure its effectiveness. A faulty SPF record can lead to legitimate emails being rejected or marked as spam, negating the benefits of implementing SPF in the first place. This section details various methods for testing and validating your SPF record, providing practical examples and tools to help you identify and resolve any potential issues. Using Online SPF Record Checkers Online SPF record checkers are the most convenient and readily accessible tools for validating your SPF record. These tools analyze your record for syntax errors, DNS lookup issues, and other common problems. Several reputable options are available:- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx – Provides a detailed analysis of your SPF record, including syntax validation, DNS lookup checks, and warnings for common issues like exceeding the 10-lookup limit.
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/ – Offers a comprehensive SPF record analysis and visualization, highlighting potential issues and providing recommendations for improvement.
- SPF Check by Agari (now Proofpoint): https://spfcheck.agari.com/ (May require account creation) – Checks the validity and structure of your SPF record.
- Navigate to https://mxtoolbox.com/spf.aspx.
- Enter your domain name (e.g., example.com) in the “Domain Name” field.
- Click the “SPF Record Lookup” button.
- Syntax Errors: The tool will highlight any syntax errors in your SPF record, such as missing spaces or incorrect qualifiers.
- Multiple SPF Records: The tool will warn you if you have multiple SPF records, which is invalid and can cause SPF checks to fail.
- DNS Lookup Issues: The tool will check if all the domains listed in your `include:` mechanisms can be resolved and if you’re exceeding the 10-lookup limit.
- Warnings: The tool may provide warnings about potential issues, such as using the `ptr` mechanism (which is generally not recommended) or not having a final `all` mechanism.
- Open the email you want to analyze.
- Click the three dots in the upper right corner of the email.
- Select “Show original.”
- Pass: The SPF check passed. The sending server is authorized to send email on behalf of the domain.
- Fail: The SPF check failed. The sending server is not authorized to send email on behalf of the domain.
- SoftFail: The SPF check resulted in a soft fail. The sending server is not explicitly authorized, but the email is not necessarily rejected. The recipient server might mark the email as spam.
- Neutral: The SPF record is neutral (e.g., `?all`). The SPF check doesn’t provide any information about whether the sending server is authorized.
- None: No SPF record was found for the domain.
- Error: An error occurred during the SPF check.
Received-SPF: pass (google.com: domain of test@example.com designates 203.0.113.123 as permitted sender) client-ip=203.0.113.123; envelope-from=test@example.com;dig txt example.comnslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
dig txt example.comnslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
SPF Record Configuration for Google Hosted Email
Ensuring proper email deliverability is crucial for any organization relying on Google Workspace (formerly G Suite). A Sender Policy Framework (SPF) record is a vital DNS record that helps prevent spammers from forging your domain in the “From” address. This article provides a comprehensive guide to configuring an SPF record specifically for Google-hosted email, covering common scenarios, troubleshooting tips, and best practices to maximize email delivery rates and minimize the risk of your emails being marked as spam. We’ll delve into practical examples and provide step-by-step instructions to ensure your SPF record is correctly configured and effective.
Table of Contents:
- Understanding SPF and Its Importance
- Creating Your SPF Record for Google Workspace
- Handling Multiple Senders and Third-Party Services
- Testing and Validating Your SPF Record
- Troubleshooting Common SPF Issues
Understanding SPF and Its Importance

- Email Deliverability: ISPs and email providers use SPF as one factor in determining whether to deliver emails to the inbox or mark them as spam.
- Domain Reputation: Protecting your domain from being used in spam campaigns maintains a positive reputation, leading to better deliverability across all email services.
- Brand Protection: Preventing phishing attacks that impersonate your brand helps maintain customer trust and avoids potential financial or reputational damage.
- Compliance: Some regulations and industry standards require email authentication measures like SPF.
v=spf1 [mechanisms] [modifiers]- v=spf1: This is the version of SPF being used. It’s mandatory and must be the first element in the record.
- Mechanisms: These define the authorized sending sources. Common mechanisms include:
ip4:Specifies an IPv4 address or range. Example:ip4:192.0.2.0/24ip6:Specifies an IPv6 address or range. Example:ip6:2001:db8::/32a:Specifies the IP address(es) of the domain’s A record. Example:a:example.commx:Specifies the IP address(es) of the domain’s MX record(s). Example:mx:example.cominclude:Includes another domain’s SPF record. This is crucial for Google Workspace. Example:include:_spf.google.comexists:Checks if a given domain name resolves. Rarely used directly. Example:exists:%{s}.example.com
- Qualifiers: Precede each mechanism and determine how the check is handled:
+(Pass): Explicitly allows the sending server (default if no qualifier is specified).-(Fail): Explicitly denies the sending server. Recipient servers should reject the email.~(SoftFail): Indicates the email might be from an unauthorized source, but the recipient server should accept it with a warning (e.g., mark it as spam).?(Neutral): Indicates the domain owner makes no assertion about whether the sending server is authorized. Effectively disables SPF checking.
- Modifiers: Provide additional instructions or information.
redirect=:Redirects the SPF check to another domain’s SPF record. Example:redirect=example.netexp=:Provides an explanation string for why an email failed the SPF check (rarely used). Example:exp=email.example.com
- all: Matches all IP addresses. It’s usually placed at the end of the record and used with a qualifier to define the default behavior for addresses not matched by other mechanisms. Common uses:
-all: Fail all unmatched addresses (strict policy).~all: SoftFail all unmatched addresses (more lenient).?all: Neutral for all unmatched addresses (effectively disables SPF).
v=spf1 include:_spf.google.com -all- Only one SPF record per domain: Having multiple SPF records can cause issues with SPF evaluation. If you need to include multiple sources, combine them into a single record.
- The 10-lookup limit: SPF records can include nested `include:` mechanisms. However, the total number of DNS lookups performed during an SPF evaluation is limited to 10. Exceeding this limit can cause SPF checks to fail. Try to consolidate your SPF record to minimize lookups.
- Prioritize security: Use the `-all` mechanism at the end of your record to enforce a strict policy and reject unauthorized emails. If you’re unsure, `~all` (SoftFail) is a safer initial option.
Creating Your SPF Record for Google Workspace

- Google Workspace Servers: This is the primary source when using Google Workspace for email. You’ll use the
include:_spf.google.commechanism to authorize these servers. - Web Servers: If your website sends emails (e.g., contact form submissions, password reset emails), you need to include the IP address of your web server or use the
aormxmechanisms if the server is associated with your domain. - Marketing Automation Platforms: If you use services like Mailchimp, SendGrid, or HubSpot, you’ll need to include their SPF records using the
include:mechanism they provide. - Transactional Email Services: Services like Sendinblue or Amazon SES also require including their SPF records.
- On-Premise Email Servers: If you have any on-premise email servers that send email for your domain, you need to include their IP addresses or hostnames.
v=spf1 include:_spf.google.com- Adding a web server with IP address 192.0.2.10:
v=spf1 include:_spf.google.com ip4:192.0.2.10 -all- Adding Mailchimp: (Replace `servers.mcsv.net` with the correct value for your Mailchimp account if different).
v=spf1 include:_spf.google.com include:servers.mcsv.net -all- Adding SendGrid:
v=spf1 include:_spf.google.com include:sendgrid.net -allv=spf1 include:_spf.google.com include:servers.mcsv.net -all- Log in to your domain registrar or hosting provider’s control panel.
- Navigate to the DNS management section. This might be called “DNS Zone Editor,” “DNS Records,” or something similar.
- Create a new TXT record.
- Enter the following values:
- Host/Name: Enter
@or leave it blank to apply the record to the root domain (e.g., example.com). If you’re creating the record for a subdomain (e.g., mail.example.com), enter the subdomain. - Type: Select
TXT. - Value/Text: Enter the SPF record you constructed in Step 2 (e.g.,
v=spf1 include:_spf.google.com include:servers.mcsv.net -all). - TTL (Time to Live): This determines how long DNS servers cache the record. The default TTL is usually fine (e.g., 3600 seconds or 1 hour).
- Host/Name: Enter
- Save the record.
- Log in to Google Domains.
- Select your domain.
- Click on “DNS.”
- Scroll down to “Custom resource records.”
- Enter the following:
- Name:
@ - Type:
TXT - TTL:
3600 - Data:
v=spf1 include:_spf.google.com include:servers.mcsv.net -all
- Name:
- Click “Add.”
- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/
- SPF Record Testing Tools: Search Google for “SPF record checker” to find other options.
- Go to https://mxtoolbox.com/spf.aspx.
- Enter your domain name (e.g., example.com).
- Click “SPF Record Lookup.”
Handling Multiple Senders and Third-Party Services
In today’s digital landscape, it’s common for organizations to use multiple services for sending emails, including Google Workspace, marketing automation platforms, transactional email services, and more. Managing SPF records for these diverse senders can be complex. This section provides guidance on how to create a comprehensive SPF record that authorizes all your legitimate sending sources while maintaining optimal email deliverability. The `include:` Mechanism: Delegation is Key The `include:` mechanism is the cornerstone of managing multiple senders. It allows you to delegate the responsibility of specifying authorized sending servers to the third-party service itself. Instead of manually adding IP addresses for each service, you simply include their SPF record in your own. This makes maintenance much easier, as the service provider is responsible for keeping their SPF record up-to-date. Example:v=spf1 include:_spf.google.com include:servers.mcsv.net include:sendgrid.net -all- Mailchimp: Search their help documentation for “SPF record” or “email authentication.” The correct value is usually
include:servers.mcsv.net(but verify this for your specific account). - SendGrid: Search their help documentation for “SPF record.” The correct value is
include:sendgrid.net. - HubSpot: Search their help documentation for “SPF record.” The correct value is
include:hs-spf.hubspotemail.net. - Amazon SES: The correct value depends on the AWS region you’re using. Refer to the Amazon SES documentation for the correct
include:value for your region (e.g.,include:amazonses.comfor the default region). - Sendinblue: The correct value is
include:spf.sendinblue.com.
v=spf1 include:_spf.google.com include:servers.mcsv.net include:sendgrid.net include:hs-spf.hubspotemail.net include:spf.sendinblue.com -all- Minimize `include:` statements: Only include the SPF records for services you actively use. Remove any unused or outdated `include:` statements.
- Flatten your SPF record (Use with Caution): Instead of using `include:`, you can manually add the IP addresses of the sending servers directly to your SPF record using the `ip4:` and `ip6:` mechanisms. However, this is generally not recommended because it requires you to manually update your SPF record whenever the service provider changes their sending infrastructure. It’s also time-consuming and error-prone. This method is generally advised against unless absolutely necessary.
- Use a dedicated email sending domain or subdomain: If you are using a large number of third-party senders, consider using a separate domain or subdomain (e.g., `mail.example.com`) specifically for sending email. This allows you to create a separate SPF record for that subdomain with only the necessary `include:` statements. This isolates the impact of the 10-lookup limit to that subdomain.
- Use SPF Record Checkers: Use online SPF record checkers (like MXToolbox) to verify that your SPF record is valid and doesn’t exceed the 10-lookup limit.
- Send Test Emails: Send test emails from each of your sending sources (Google Workspace, Mailchimp, SendGrid, etc.) to an email address you control (e.g., a Gmail account). Check the email headers to confirm that the SPF check passed.
- Monitor Email Deliverability: Pay attention to your email deliverability rates. If you notice a sudden drop in deliverability, it could indicate an issue with your SPF record.
- Use DMARC Reporting: Implement DMARC (Domain-based Message Authentication, Reporting & Conformance) and enable DMARC reporting. DMARC reports provide valuable insights into how your emails are being authenticated and whether SPF and DKIM (DomainKeys Identified Mail) are passing. This allows you to identify and address any authentication issues.
Testing and Validating Your SPF Record
Once you’ve created or modified your SPF record, rigorous testing and validation are essential to ensure its effectiveness. A faulty SPF record can lead to legitimate emails being rejected or marked as spam, negating the benefits of implementing SPF in the first place. This section details various methods for testing and validating your SPF record, providing practical examples and tools to help you identify and resolve any potential issues. Using Online SPF Record Checkers Online SPF record checkers are the most convenient and readily accessible tools for validating your SPF record. These tools analyze your record for syntax errors, DNS lookup issues, and other common problems. Several reputable options are available:- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx – Provides a detailed analysis of your SPF record, including syntax validation, DNS lookup checks, and warnings for common issues like exceeding the 10-lookup limit.
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/ – Offers a comprehensive SPF record analysis and visualization, highlighting potential issues and providing recommendations for improvement.
- SPF Check by Agari (now Proofpoint): https://spfcheck.agari.com/ (May require account creation) – Checks the validity and structure of your SPF record.
- Navigate to https://mxtoolbox.com/spf.aspx.
- Enter your domain name (e.g., example.com) in the “Domain Name” field.
- Click the “SPF Record Lookup” button.
- Syntax Errors: The tool will highlight any syntax errors in your SPF record, such as missing spaces or incorrect qualifiers.
- Multiple SPF Records: The tool will warn you if you have multiple SPF records, which is invalid and can cause SPF checks to fail.
- DNS Lookup Issues: The tool will check if all the domains listed in your `include:` mechanisms can be resolved and if you’re exceeding the 10-lookup limit.
- Warnings: The tool may provide warnings about potential issues, such as using the `ptr` mechanism (which is generally not recommended) or not having a final `all` mechanism.
- Open the email you want to analyze.
- Click the three dots in the upper right corner of the email.
- Select “Show original.”
- Pass: The SPF check passed. The sending server is authorized to send email on behalf of the domain.
- Fail: The SPF check failed. The sending server is not authorized to send email on behalf of the domain.
- SoftFail: The SPF check resulted in a soft fail. The sending server is not explicitly authorized, but the email is not necessarily rejected. The recipient server might mark the email as spam.
- Neutral: The SPF record is neutral (e.g., `?all`). The SPF check doesn’t provide any information about whether the sending server is authorized.
- None: No SPF record was found for the domain.
- Error: An error occurred during the SPF check.
Received-SPF: pass (google.com: domain of test@example.com designates 203.0.113.123 as permitted sender) client-ip=203.0.113.123; envelope-from=test@example.com;dig txt example.comnslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
nslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
dig txt example.comnslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
SPF Record Configuration for Google Hosted Email
Ensuring proper email deliverability is crucial for any organization relying on Google Workspace (formerly G Suite). A Sender Policy Framework (SPF) record is a vital DNS record that helps prevent spammers from forging your domain in the “From” address. This article provides a comprehensive guide to configuring an SPF record specifically for Google-hosted email, covering common scenarios, troubleshooting tips, and best practices to maximize email delivery rates and minimize the risk of your emails being marked as spam. We’ll delve into practical examples and provide step-by-step instructions to ensure your SPF record is correctly configured and effective.
Table of Contents:
- Understanding SPF and Its Importance
- Creating Your SPF Record for Google Workspace
- Handling Multiple Senders and Third-Party Services
- Testing and Validating Your SPF Record
- Troubleshooting Common SPF Issues
Understanding SPF and Its Importance

- Email Deliverability: ISPs and email providers use SPF as one factor in determining whether to deliver emails to the inbox or mark them as spam.
- Domain Reputation: Protecting your domain from being used in spam campaigns maintains a positive reputation, leading to better deliverability across all email services.
- Brand Protection: Preventing phishing attacks that impersonate your brand helps maintain customer trust and avoids potential financial or reputational damage.
- Compliance: Some regulations and industry standards require email authentication measures like SPF.
v=spf1 [mechanisms] [modifiers]- v=spf1: This is the version of SPF being used. It’s mandatory and must be the first element in the record.
- Mechanisms: These define the authorized sending sources. Common mechanisms include:
ip4:Specifies an IPv4 address or range. Example:ip4:192.0.2.0/24ip6:Specifies an IPv6 address or range. Example:ip6:2001:db8::/32a:Specifies the IP address(es) of the domain’s A record. Example:a:example.commx:Specifies the IP address(es) of the domain’s MX record(s). Example:mx:example.cominclude:Includes another domain’s SPF record. This is crucial for Google Workspace. Example:include:_spf.google.comexists:Checks if a given domain name resolves. Rarely used directly. Example:exists:%{s}.example.com
- Qualifiers: Precede each mechanism and determine how the check is handled:
+(Pass): Explicitly allows the sending server (default if no qualifier is specified).-(Fail): Explicitly denies the sending server. Recipient servers should reject the email.~(SoftFail): Indicates the email might be from an unauthorized source, but the recipient server should accept it with a warning (e.g., mark it as spam).?(Neutral): Indicates the domain owner makes no assertion about whether the sending server is authorized. Effectively disables SPF checking.
- Modifiers: Provide additional instructions or information.
redirect=:Redirects the SPF check to another domain’s SPF record. Example:redirect=example.netexp=:Provides an explanation string for why an email failed the SPF check (rarely used). Example:exp=email.example.com
- all: Matches all IP addresses. It’s usually placed at the end of the record and used with a qualifier to define the default behavior for addresses not matched by other mechanisms. Common uses:
-all: Fail all unmatched addresses (strict policy).~all: SoftFail all unmatched addresses (more lenient).?all: Neutral for all unmatched addresses (effectively disables SPF).
v=spf1 include:_spf.google.com -all- Only one SPF record per domain: Having multiple SPF records can cause issues with SPF evaluation. If you need to include multiple sources, combine them into a single record.
- The 10-lookup limit: SPF records can include nested `include:` mechanisms. However, the total number of DNS lookups performed during an SPF evaluation is limited to 10. Exceeding this limit can cause SPF checks to fail. Try to consolidate your SPF record to minimize lookups.
- Prioritize security: Use the `-all` mechanism at the end of your record to enforce a strict policy and reject unauthorized emails. If you’re unsure, `~all` (SoftFail) is a safer initial option.
Creating Your SPF Record for Google Workspace

- Google Workspace Servers: This is the primary source when using Google Workspace for email. You’ll use the
include:_spf.google.commechanism to authorize these servers. - Web Servers: If your website sends emails (e.g., contact form submissions, password reset emails), you need to include the IP address of your web server or use the
aormxmechanisms if the server is associated with your domain. - Marketing Automation Platforms: If you use services like Mailchimp, SendGrid, or HubSpot, you’ll need to include their SPF records using the
include:mechanism they provide. - Transactional Email Services: Services like Sendinblue or Amazon SES also require including their SPF records.
- On-Premise Email Servers: If you have any on-premise email servers that send email for your domain, you need to include their IP addresses or hostnames.
v=spf1 include:_spf.google.com- Adding a web server with IP address 192.0.2.10:
v=spf1 include:_spf.google.com ip4:192.0.2.10 -all- Adding Mailchimp: (Replace `servers.mcsv.net` with the correct value for your Mailchimp account if different).
v=spf1 include:_spf.google.com include:servers.mcsv.net -all- Adding SendGrid:
v=spf1 include:_spf.google.com include:sendgrid.net -allv=spf1 include:_spf.google.com include:servers.mcsv.net -all- Log in to your domain registrar or hosting provider’s control panel.
- Navigate to the DNS management section. This might be called “DNS Zone Editor,” “DNS Records,” or something similar.
- Create a new TXT record.
- Enter the following values:
- Host/Name: Enter
@or leave it blank to apply the record to the root domain (e.g., example.com). If you’re creating the record for a subdomain (e.g., mail.example.com), enter the subdomain. - Type: Select
TXT. - Value/Text: Enter the SPF record you constructed in Step 2 (e.g.,
v=spf1 include:_spf.google.com include:servers.mcsv.net -all). - TTL (Time to Live): This determines how long DNS servers cache the record. The default TTL is usually fine (e.g., 3600 seconds or 1 hour).
- Host/Name: Enter
- Save the record.
- Log in to Google Domains.
- Select your domain.
- Click on “DNS.”
- Scroll down to “Custom resource records.”
- Enter the following:
- Name:
@ - Type:
TXT - TTL:
3600 - Data:
v=spf1 include:_spf.google.com include:servers.mcsv.net -all
- Name:
- Click “Add.”
- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/
- SPF Record Testing Tools: Search Google for “SPF record checker” to find other options.
- Go to https://mxtoolbox.com/spf.aspx.
- Enter your domain name (e.g., example.com).
- Click “SPF Record Lookup.”
Handling Multiple Senders and Third-Party Services
In today’s digital landscape, it’s common for organizations to use multiple services for sending emails, including Google Workspace, marketing automation platforms, transactional email services, and more. Managing SPF records for these diverse senders can be complex. This section provides guidance on how to create a comprehensive SPF record that authorizes all your legitimate sending sources while maintaining optimal email deliverability. The `include:` Mechanism: Delegation is Key The `include:` mechanism is the cornerstone of managing multiple senders. It allows you to delegate the responsibility of specifying authorized sending servers to the third-party service itself. Instead of manually adding IP addresses for each service, you simply include their SPF record in your own. This makes maintenance much easier, as the service provider is responsible for keeping their SPF record up-to-date. Example:v=spf1 include:_spf.google.com include:servers.mcsv.net include:sendgrid.net -all- Mailchimp: Search their help documentation for “SPF record” or “email authentication.” The correct value is usually
include:servers.mcsv.net(but verify this for your specific account). - SendGrid: Search their help documentation for “SPF record.” The correct value is
include:sendgrid.net. - HubSpot: Search their help documentation for “SPF record.” The correct value is
include:hs-spf.hubspotemail.net. - Amazon SES: The correct value depends on the AWS region you’re using. Refer to the Amazon SES documentation for the correct
include:value for your region (e.g.,include:amazonses.comfor the default region). - Sendinblue: The correct value is
include:spf.sendinblue.com.
v=spf1 include:_spf.google.com include:servers.mcsv.net include:sendgrid.net include:hs-spf.hubspotemail.net include:spf.sendinblue.com -all- Minimize `include:` statements: Only include the SPF records for services you actively use. Remove any unused or outdated `include:` statements.
- Flatten your SPF record (Use with Caution): Instead of using `include:`, you can manually add the IP addresses of the sending servers directly to your SPF record using the `ip4:` and `ip6:` mechanisms. However, this is generally not recommended because it requires you to manually update your SPF record whenever the service provider changes their sending infrastructure. It’s also time-consuming and error-prone. This method is generally advised against unless absolutely necessary.
- Use a dedicated email sending domain or subdomain: If you are using a large number of third-party senders, consider using a separate domain or subdomain (e.g., `mail.example.com`) specifically for sending email. This allows you to create a separate SPF record for that subdomain with only the necessary `include:` statements. This isolates the impact of the 10-lookup limit to that subdomain.
- Use SPF Record Checkers: Use online SPF record checkers (like MXToolbox) to verify that your SPF record is valid and doesn’t exceed the 10-lookup limit.
- Send Test Emails: Send test emails from each of your sending sources (Google Workspace, Mailchimp, SendGrid, etc.) to an email address you control (e.g., a Gmail account). Check the email headers to confirm that the SPF check passed.
- Monitor Email Deliverability: Pay attention to your email deliverability rates. If you notice a sudden drop in deliverability, it could indicate an issue with your SPF record.
- Use DMARC Reporting: Implement DMARC (Domain-based Message Authentication, Reporting & Conformance) and enable DMARC reporting. DMARC reports provide valuable insights into how your emails are being authenticated and whether SPF and DKIM (DomainKeys Identified Mail) are passing. This allows you to identify and address any authentication issues.
Testing and Validating Your SPF Record
Once you’ve created or modified your SPF record, rigorous testing and validation are essential to ensure its effectiveness. A faulty SPF record can lead to legitimate emails being rejected or marked as spam, negating the benefits of implementing SPF in the first place. This section details various methods for testing and validating your SPF record, providing practical examples and tools to help you identify and resolve any potential issues. Using Online SPF Record Checkers Online SPF record checkers are the most convenient and readily accessible tools for validating your SPF record. These tools analyze your record for syntax errors, DNS lookup issues, and other common problems. Several reputable options are available:- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx – Provides a detailed analysis of your SPF record, including syntax validation, DNS lookup checks, and warnings for common issues like exceeding the 10-lookup limit.
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/ – Offers a comprehensive SPF record analysis and visualization, highlighting potential issues and providing recommendations for improvement.
- SPF Check by Agari (now Proofpoint): https://spfcheck.agari.com/ (May require account creation) – Checks the validity and structure of your SPF record.
- Navigate to https://mxtoolbox.com/spf.aspx.
- Enter your domain name (e.g., example.com) in the “Domain Name” field.
- Click the “SPF Record Lookup” button.
- Syntax Errors: The tool will highlight any syntax errors in your SPF record, such as missing spaces or incorrect qualifiers.
- Multiple SPF Records: The tool will warn you if you have multiple SPF records, which is invalid and can cause SPF checks to fail.
- DNS Lookup Issues: The tool will check if all the domains listed in your `include:` mechanisms can be resolved and if you’re exceeding the 10-lookup limit.
- Warnings: The tool may provide warnings about potential issues, such as using the `ptr` mechanism (which is generally not recommended) or not having a final `all` mechanism.
- Open the email you want to analyze.
- Click the three dots in the upper right corner of the email.
- Select “Show original.”
- Pass: The SPF check passed. The sending server is authorized to send email on behalf of the domain.
- Fail: The SPF check failed. The sending server is not authorized to send email on behalf of the domain.
- SoftFail: The SPF check resulted in a soft fail. The sending server is not explicitly authorized, but the email is not necessarily rejected. The recipient server might mark the email as spam.
- Neutral: The SPF record is neutral (e.g., `?all`). The SPF check doesn’t provide any information about whether the sending server is authorized.
- None: No SPF record was found for the domain.
- Error: An error occurred during the SPF check.
Received-SPF: pass (google.com: domain of test@example.com designates 203.0.113.123 as permitted sender) client-ip=203.0.113.123; envelope-from=test@example.com;dig txt example.comnslookup -type=txt example.com- Which sending sources are passing or failing SPF and DKIM checks.
- The volume of email being sent from each source.
- Any potential authentication issues.
