How to Set Up an SPF Record for Optimal Email Delivery
Sender Policy Framework (SPF) records are essential for improving email deliverability and preventing spoofing. By defining which mail servers are authorized to send emails on behalf of your domain, you significantly reduce the chances of your emails being marked as spam. This article provides a comprehensive guide on how to create and configure SPF records, ensuring your emails reach their intended recipients and enhancing your domain’s reputation.
This guide will walk you through the key concepts, practical examples, and common pitfalls of SPF record setup, enabling you to implement a robust email authentication strategy. We’ll cover creating the record, understanding its syntax, testing its validity, and troubleshooting common issues, all with the goal of getting your emails delivered successfully.
Understanding SPF Records: Purpose, Syntax, and Benefits
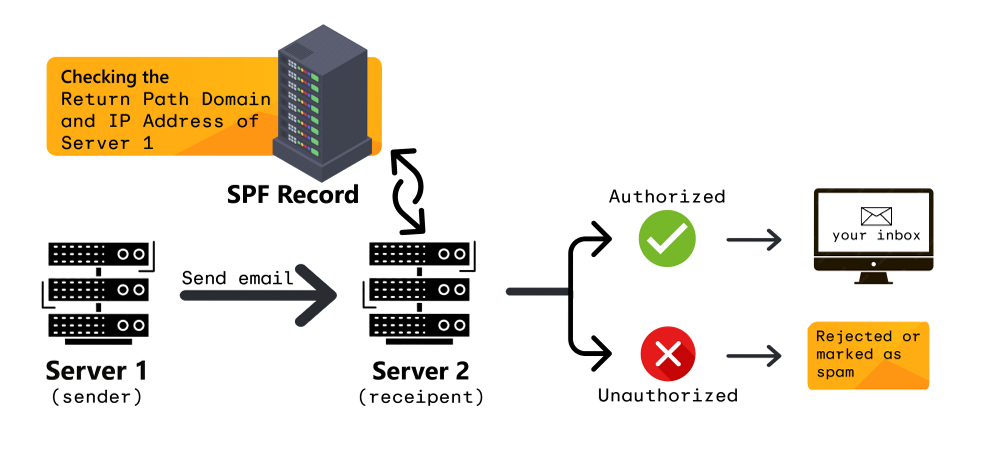
- Version: The SPF record must start with
v=spf1. This indicates that the record is an SPF version 1 record. - Mechanisms: Mechanisms define which mail servers are authorized to send emails. Common mechanisms include:
ip4:: Specifies an IPv4 address or range of addresses. For example,ip4:192.0.2.0authorizes emails from that specific IP address.ip4:192.0.2.0/24authorizes emails from the range 192.0.2.0 to 192.0.2.255.ip6:: Specifies an IPv6 address or range of addresses. For example,ip6:2001:db8::1authorizes emails from that specific IPv6 address.a:: Authorizes emails from the A record of the specified domain. For example,a:example.comauthorizes emails from the IP address(es) to which example.com resolves.mx:: Authorizes emails from the mail exchangers (MX records) of the specified domain. For example,mx:example.comauthorizes emails from the servers listed in the MX records for example.com.include:: Includes the SPF record of another domain. This is commonly used when outsourcing email sending to a third-party provider. For example,include:_spf.google.comincludes Google’s SPF record, authorizing Google’s mail servers.exists:: Checks if a specified domain name exists. This is less common but can be used for more complex authorization scenarios.
- Qualifiers: Qualifiers modify the behavior of the mechanisms. Common qualifiers include:
+:(Pass): This is the default qualifier. If a mechanism matches, the email passes the SPF check.-:(Fail): If a mechanism matches, the email fails the SPF check.~:(Softfail): If a mechanism matches, the email is marked as a softfail. This suggests the email might be suspicious but doesn’t necessarily mean it’s spam. Receiving servers might still accept the email but may mark it as spam or place it in the recipient’s junk folder.?:(Neutral): Specifies that the SPF record makes no assertion about whether the email is authorized.
- The
allmechanism: Theallmechanism always matches. It’s typically used at the end of the SPF record to specify what should happen if none of the other mechanisms match. Common uses include:-all: Indicates that any email not matching the previous mechanisms should fail the SPF check. This is the strictest and recommended approach.~all: Indicates that any email not matching the previous mechanisms should be marked as a softfail.?all: Indicates that the SPF record makes no assertion about emails not matching the previous mechanisms.
- Improved Email Deliverability: ISPs and email providers are more likely to deliver emails from domains with valid SPF records to the inbox rather than the spam folder.
- Enhanced Domain Reputation: By preventing spoofing, you protect your domain’s reputation, making it less likely to be blacklisted by email providers.
- Reduced Spam: SPF helps prevent spammers from using your domain to send unauthorized emails, which protects your recipients and your brand.
- Compliance with Email Standards: Many email providers require SPF records for bulk email sending and other services.
v=spf1 ip4:192.0.2.10 -allv=spf1 include:_spf.google.com -allv=spf1 ip4:192.0.2.10 ip4:192.0.2.11 include:servers.mcsv.net -allCreating an SPF Record: Step-by-Step Guide
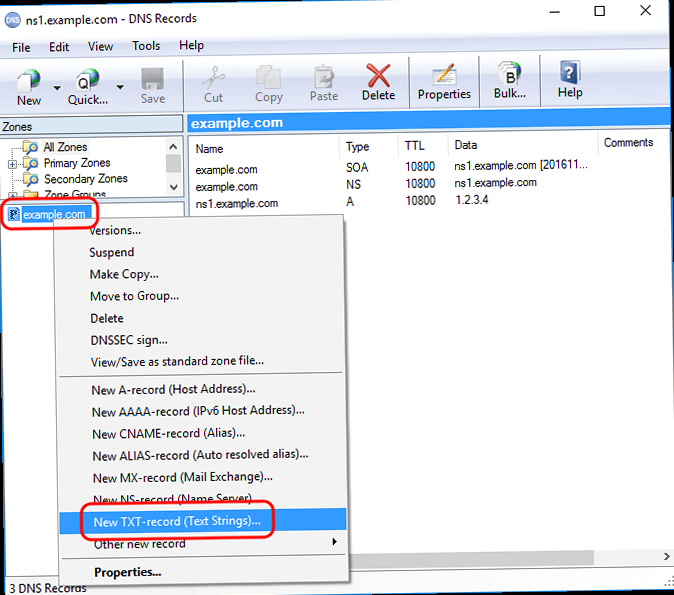
- Step 1: Identify All Authorized Mail Servers:
Compile a comprehensive list of all mail servers that send emails on behalf of your domain. This includes:- Your own mail servers (if you host your own email).
- Third-party email providers (e.g., Google Workspace, Microsoft 365, Mailchimp, SendGrid).
- Any other services that send emails using your domain (e.g., transactional email services, marketing automation platforms).
- Step 2: Construct the SPF Record:
Based on the identified mail servers, construct the SPF record using the correct syntax and mechanisms. Start with `v=spf1` and add mechanisms for each authorized mail server. Remember to end the record with the `all` mechanism (e.g., `-all` or `~all`). - Step 3: Access Your DNS Management Interface:
Log in to the DNS management interface for your domain. This is typically provided by your domain registrar or DNS hosting provider. Common providers include GoDaddy, Namecheap, Cloudflare, and AWS Route 53. - Step 4: Add a TXT Record:
Navigate to the section for adding or editing DNS records. Create a new TXT record with the following settings:- Host/Name: Enter `@` or leave it blank. This indicates that the record applies to the root domain (e.g., `example.com`). Some DNS providers may require you to enter the domain name itself (e.g., `example.com`). Check your DNS provider’s documentation for the correct syntax.
- Value/Content: Enter the SPF record string you constructed in Step 2 (e.g., `v=spf1 ip4:192.0.2.10 include:_spf.google.com -all`).
- TTL (Time To Live): Set the TTL to a reasonable value, such as 3600 seconds (1 hour). This determines how long DNS resolvers cache the record before querying for updates. A shorter TTL allows for faster propagation of changes, but a longer TTL reduces the load on your DNS servers.
- Step 5: Save the Record:
Save the new TXT record. The changes may take some time to propagate across the internet. The time it takes for the DNS record to propagate depends on the TTL and the caching policies of DNS resolvers. - Step 6: Test the SPF Record:
Use online SPF record testing tools (mentioned in a later section) to verify that your SPF record is valid and configured correctly.
- Log in to your GoDaddy account and navigate to your domain’s DNS management page.
- Click “Add” to add a new DNS record.
- Select “TXT” as the record type.
- In the “Host” field, enter `@`.
- In the “TXT Value” field, enter your SPF record string (e.g., `v=spf1 ip4:192.0.2.10 -all`).
- Set the TTL to 3600.
- Click “Save”.
- Log in to your Cloudflare account and select your domain.
- Navigate to the “DNS” section.
- Click “Add record”.
- Select “TXT” as the record type.
- In the “Name” field, enter `@`.
- In the “Content” field, enter your SPF record string (e.g., `v=spf1 ip4:192.0.2.10 -all`).
- Set the TTL to “Auto” or a specific value (e.g., 3600).
- Click “Save”.
- Open the Route 53 console.
- Choose “Hosted zones”.
- Select the hosted zone for your domain.
- Click “Create record”.
- Choose “TXT” as the record type.
- Leave the “Record name” field blank (for the root domain) or enter your subdomain.
- In the “Value” field, enter your SPF record string, enclosed in quotes (e.g., `”v=spf1 ip4:192.0.2.10 -all”`). The quotes are important.
- Set the TTL (e.g., 3600).
- Click “Create record”.
Testing and Validating Your SPF Record
Once you’ve created your SPF record, it’s crucial to test and validate it to ensure it’s configured correctly. This helps prevent deliverability issues and ensures that your emails are properly authenticated. There are several methods you can use to test your SPF record:- Using Online SPF Record Testing Tools:
Numerous online tools are available that can check the syntax and validity of your SPF record. These tools typically perform DNS lookups and analyze the SPF record to identify any errors or potential issues. Some popular tools include:- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/
- SPF Record Checker: https://www.spfwizard.net/spfrecordcheck/
- Using Command-Line Tools:
You can also use command-line tools like `dig` or `nslookup` to query the DNS records for your domain and manually verify the SPF record.- Using
dig(Linux/macOS):
Open a terminal and run the following command:
Replace `example.com` with your domain name. The output will include the TXT records for your domain, including the SPF record. Verify that the SPF record is present and that the syntax is correct.dig txt example.com - Using
nslookup(Windows):
Open a command prompt and run the following command:
Replace `example.com` with your domain name. The output will include the TXT records for your domain, including the SPF record. Verify that the SPF record is present and that the syntax is correct.nslookup -type=txt example.com
- Using
- Checking Email Headers:
After sending an email from your domain, you can examine the email headers to see the results of the SPF check. The headers will typically include an “Authentication-Results” header that contains information about the SPF check. The exact format of the header may vary depending on the receiving mail server, but it will generally indicate whether the SPF check passed, failed, or resulted in a softfail. To view email headers, you’ll need to access the raw source of the email. The method for doing this varies depending on your email client. In Gmail, for example, you can click the three dots in the upper-right corner of the email and select “Show original”.
dig on Linux
Open a terminal and run the following command:
dig txt example.com; <<>> DiG 9.18.12-0ubuntu0.22.04.3-Ubuntu <<>> txt example.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43809
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65535
;; QUESTION SECTION:
;example.com. IN TXT
;; ANSWER SECTION:
example.com. 3600 IN TXT "v=spf1 ip4:192.0.2.10 -all"
;; Query time: 0 msec
;; SERVER: 127.0.0.53#53(127.0.0.53)
;; WHEN: Tue Oct 24 10:30:00 UTC 2023
;; MSG SIZE rcvd: 80
Authentication-Results: mx.google.com;
spf=pass (google.com: domain of sender@example.com designates 192.0.2.10 as permitted sender) smtp.mailfrom=sender@example.com
- Syntax errors: Ensure that the SPF record is correctly formatted and that all mechanisms are properly specified.
- Missing authorized mail servers: Verify that you have included all mail servers that send emails on behalf of your domain.
- DNS lookup limit: Ensure that your SPF record does not exceed the 10 DNS lookup limit.
- Record propagation: Wait for the DNS changes to propagate across the internet before testing the record.
Common SPF Issues and Troubleshooting
Setting up SPF records can sometimes be tricky, and various issues can arise that impact email deliverability. Understanding these common problems and how to troubleshoot them is crucial for maintaining a healthy email sending reputation.- SPF Record Syntax Errors:
One of the most common issues is incorrect syntax in the SPF record. Even a small typo can cause the entire record to fail.- Problem: Incorrectly formatted IP addresses, missing spaces, or invalid mechanisms.
- Solution: Carefully review the SPF record for any typos or syntax errors. Use online SPF record testing tools to identify specific issues.
- Exceeding the 10 DNS Lookup Limit:
SPF records have a limit of 10 DNS lookups, including nested `include` statements. Exceeding this limit will cause the SPF check to fail.- Problem: Too many `include` mechanisms or nested lookups.
- Solution: Optimize your SPF record by reducing the number of `include` statements. Consider using `ip4` or `ip6` mechanisms instead of `include` whenever possible. Flatten your SPF record by manually including the IP addresses from the included domains, but be prepared to update them when those services change IPs.
- Multiple SPF Records:
A domain should only have one SPF record. Having multiple SPF records can cause unpredictable results.- Problem: Multiple TXT records starting with `v=spf1`.
- Solution: Remove all but one SPF record and merge the information from the other records into the remaining record.
- Incorrect
includeStatements:
Using the wrong `include` statement for a third-party email provider can lead to SPF failures.- Problem: Using an outdated or incorrect `include` statement.
- Solution: Always refer to the documentation of the third-party email provider for the correct `include` statement. Make sure to use the correct subdomain or domain name.
- Missing Authorized Mail Servers:
If you forget to include all authorized mail servers in your SPF record, legitimate emails may fail the SPF check.- Problem: Emails from authorized servers are being marked as spam.
- Solution: Review your list of authorized mail servers and add any missing servers to your SPF record.
- DNS Propagation Issues:
After making changes to your SPF record, it can take some time for the changes to propagate across the internet.- Problem: SPF checks are failing even after updating the SPF record.
- Solution: Wait for the DNS changes to propagate. You can use online DNS propagation checkers to monitor the progress.
- Using
ptrMechanism:
The `ptr` mechanism is not recommended because it relies on reverse DNS lookups, which are often unreliable.- Problem: Deliverability issues due to unreliable reverse DNS lookups.
- Solution: Avoid using the `ptr` mechanism. Use `ip4`, `ip6`, `a`, or `mx` mechanisms instead.
v=spf1 include:_spf.google.com include:servers.mcsv.net include:spf.sendgrid.net include:spf.example.com -allv=spf1 ip4:192.0.2.10 -all
v=spf1 include:_spf.google.com -allv=spf1 ip4:192.0.2.10 include:_spf.google.com -allv=spf1 include:mailchimp.com -allv=spf1 include:servers.mcsv.net -allIntegrating SPF with DMARC for Enhanced Email Security
While SPF helps verify the sender’s mail server, it’s often used in conjunction with DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting & Conformance (DMARC) to provide a comprehensive email authentication strategy. DMARC builds upon SPF and DKIM, providing instructions to receiving mail servers on how to handle emails that fail authentication checks. It also enables reporting, allowing you to monitor email sending activity and identify potential spoofing attempts. Here’s how SPF, DKIM, and DMARC work together:- SPF (Sender Policy Framework): Verifies that the mail server sending the email is authorized to send emails on behalf of the domain.
- DKIM (DomainKeys Identified Mail): Adds a digital signature to the email, which can be verified by the receiving mail server. This signature confirms that the email has not been altered during transit.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): Defines a policy for how receiving mail servers should handle emails that fail SPF and DKIM checks. It also provides reporting mechanisms to monitor email sending activity and identify potential authentication issues.
- Step 1: Implement SPF and DKIM:
Ensure that both SPF and DKIM are properly configured for your domain. This provides the foundation for DMARC to function effectively. - Step 2: Create a DMARC Record:
Create a DMARC record and add it to your DNS zone file. The DMARC record specifies the policy for handling emails that fail SPF and DKIM checks. A DMARC record is also a TXT record. The DMARC record typically includes the following tags:v: Specifies the DMARC version (e.g., `DMARC1`).p: Specifies the policy for handling emails that fail SPF and DKIM checks (e.g., `none`, `quarantine`, `reject`).none: The receiving mail server should take no specific action. This is typically used for initial monitoring.quarantine: The receiving mail server should place the email in the recipient’s spam folder.reject: The receiving mail server should reject the email.
rua: Specifies the email address(es) to which aggregate reports should be sent. These reports provide summarized information about email sending activity and authentication results.ruf: Specifies the email address(es) to which forensic reports (also known as failure reports) should be sent. These reports provide detailed information about individual emails that failed authentication checks. Be cautious about enabling forensic reports, as they can contain sensitive information.adkim: Alignment mode for DKIM identifiers. Can be `r` (relaxed) or `s` (strict).aspf: Alignment mode for SPF identifiers. Can be `r` (relaxed) or `s` (strict).sp: Policy to apply to subdomains.pct: Percentage of messages to which the DMARC policy is applied.
- Step 3: Monitor DMARC Reports:
Analyze the DMARC reports to identify any authentication issues or potential spoofing attempts. Use this information to refine your SPF and DKIM configurations and adjust your DMARC policy as needed. - Step 4: Enforce DMARC Policy:
Once you are confident that your SPF and DKIM configurations are correct and that you are not inadvertently blocking legitimate emails, you can gradually increase the enforcement of your DMARC policy. Start with `p=none` for monitoring, then move to `p=quarantine` to place failing emails in spam, and finally to `p=reject` to reject failing emails.
v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com; adkim=r; aspf=r;v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com; ruf=mailto:forensic-reports@example.com; adkim=s; aspf=s;