How to Prevent Spam: Mastering Email Authentication
Email spam remains a persistent problem, clogging inboxes and posing security risks. While spam filters have become sophisticated, spammers continually adapt their tactics. This article focuses on a crucial aspect of combating spam: email authentication. We’ll delve into implementing and managing SPF, DKIM, and DMARC records – essential tools for verifying email sender identity and improving email deliverability, ensuring your legitimate emails reach their intended recipients.
This guide aims to provide a practical, hands-on approach to understanding and implementing these protocols, empowering you to take control of your email security and minimize the risk of your emails being flagged as spam.
| Section | Description |
|---|---|
| Understanding SPF (Sender Policy Framework) | Explains what SPF is and how it helps prevent email spoofing. |
| Implementing DKIM (DomainKeys Identified Mail) | Details how DKIM uses cryptographic signatures to verify email integrity. |
| Configuring DMARC (Domain-based Message Authentication, Reporting & Conformance) | Shows how DMARC builds on SPF and DKIM to define policies for handling unauthenticated emails. |
| Testing and Troubleshooting Authentication Records | Provides practical steps for verifying and resolving issues with your SPF, DKIM, and DMARC configurations. |
Understanding SPF (Sender Policy Framework)
- v=spf1: This specifies the SPF version being used (currently, only v=spf1 is used).
- ip4: Specifies individual IPv4 addresses or ranges.
- ip6: Specifies individual IPv6 addresses or ranges.
- a: Authorizes the IP address(es) of the host specified by the domain name.
- mx: Authorizes the IP address(es) of the mail exchangers (MX records) for the specified domain.
- include: Includes another domain’s SPF record. This is often used when using third-party email services.
- -all, ~all, ?all, +all: The “all” mechanism specifies what should happen if none of the preceding mechanisms match. “-all” means “fail” (emails from non-authorized sources should be rejected), “~all” means “softfail” (emails from non-authorized sources should be accepted but marked as potentially suspicious), “?all” means “neutral” (no policy), and “+all” (rarely used, essentially disables SPF).
v=spf1 ip4:192.0.2.0/24 -all-all mechanism specifies that any other source should be considered a hard fail, meaning the receiving server should reject the email.
Example 2: Including a Third-Party Email Service
v=spf1 include:servers.mailchimp.com -allv=spf1 ip4:192.0.2.0/24 ip4:203.0.113.10 include:servers.mailchimp.com -all- Limit the Number of Lookups: SPF has a limit of 10 DNS lookups. Exceeding this limit can cause SPF checks to fail. This limit is especially relevant when using multiple
includestatements. - Use Specific IP Addresses or Ranges: Avoid using overly broad IP ranges if possible. Be as specific as you can to minimize the risk of unauthorized senders being included.
- Regularly Review Your SPF Record: Ensure your SPF record remains accurate and reflects your current sending infrastructure. As your email sending practices change, update your SPF record accordingly.
- Start with ~all and Monitor: Before implementing
-all, which can potentially block legitimate emails if misconfigured, start with~all(softfail). Monitor your email deliverability and SPF reports to identify any false positives before switching to-all. - Consider Using a Dedicated Subdomain: If you send transactional emails and marketing emails from different sources, consider using a dedicated subdomain for marketing emails. This allows you to create a separate SPF record for that subdomain, isolating any potential deliverability issues.
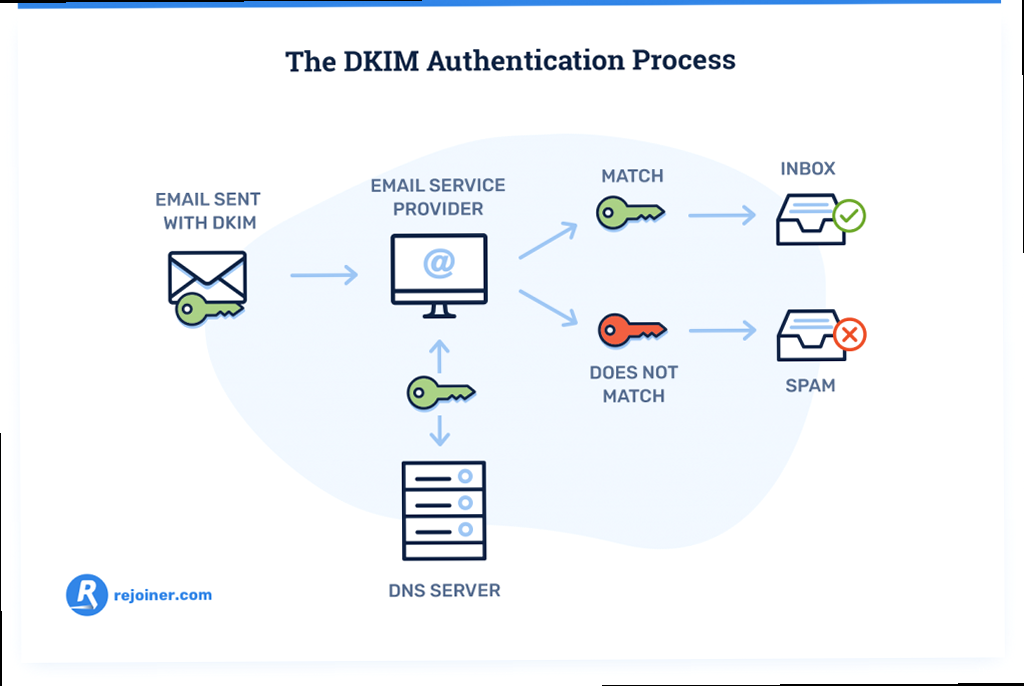
Implementing DKIM (DomainKeys Identified Mail)
openssl genrsa -out private.key 2048
openssl rsa -in private.key -pubout -out public.keyprivate.key (containing the private key) and public.key (containing the public key). Keep the private key secure. It should only be accessible to your email server.
Adding the DKIM Record to DNS
The public key needs to be added to your domain’s DNS as a TXT record. The record name typically follows the format selector._domainkey.yourdomain.com, where “selector” is an arbitrary string you choose to identify the key. Common selectors are “default” or “mail”.
Example: DKIM DNS Record
Selector: default
Record Name: default._domainkey.example.com
Record Type: TXT
Record Value: v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwWfW7wW9r99... (rest of the public key) ...AQAB;- v=DKIM1: Specifies the DKIM version.
- k=rsa: Specifies the key type (RSA).
- p=: Contains the public key. This is the long string generated earlier. Remove any line breaks from the public key before adding it to the DNS record.
- Key Length: Use a key length of at least 2048 bits for strong security.
- Selector Uniqueness: If you have multiple email sending services, use different selectors for each to avoid conflicts.
- Record Length Limits: Some DNS providers have length limits for TXT records. If your public key is too long, you may need to split it into multiple strings.
- Install OpenDKIM:
sudo apt-get install opendkim opendkim-tools - Configure OpenDKIM in
/etc/opendkim.conf:
Syslog yes
SyslogSuccess yes
LogWhy yes
UserID opendkim:opendkim
Socket inet:8891@localhost
KeyTable refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
TrustedHosts refile:/etc/opendkim/TrustedHosts- Create the KeyTable file (
/etc/opendkim/KeyTable):
default._domainkey.example.com example.com:default:/etc/opendkim/keys/example.com/default.private- Create the SigningTable file (
/etc/opendkim/SigningTable):
*@example.com default._domainkey.example.com- Create the TrustedHosts file (
/etc/opendkim/TrustedHosts):
127.0.0.1
localhost
::1
example.com- Create the directory for the keys and copy the private key:
sudo mkdir -p /etc/opendkim/keys/example.com; sudo cp private.key /etc/opendkim/keys/example.com/default.private; sudo chown opendkim:opendkim /etc/opendkim/keys/example.com/default.private; sudo chmod 600 /etc/opendkim/keys/example.com/default.private - Configure Postfix to use OpenDKIM in
/etc/postfix/main.cf:
milter_default_action = accept
milter_protocol = 2
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = inet:127.0.0.1:8891- Restart OpenDKIM and Postfix:
sudo systemctl restart opendkim; sudo systemctl restart postfix
Configuring DMARC (Domain-based Message Authentication, Reporting & Conformance)
Domain-based Message Authentication, Reporting & Conformance (DMARC) builds upon SPF and DKIM to provide a comprehensive email authentication framework. DMARC allows you to define a policy for how receiving mail servers should handle emails that fail SPF and/or DKIM checks. It also provides a mechanism for receiving reports about email authentication results, allowing you to monitor your email sending sources and identify potential spoofing attempts. DMARC essentially tells receiving mail servers what to do with emails that fail authentication:- none: The receiving server should take no specific action. This is typically used for initial monitoring.
- quarantine: The receiving server should mark the email as spam or move it to the spam folder.
- reject: The receiving server should reject the email entirely.
_dmarc.yourdomain.com.
Example: DMARC DNS Record
Record Name: _dmarc.example.com
Record Type: TXT
Record Value: v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; adkim=r; aspf=r;- v=DMARC1: Specifies the DMARC version.
- p=: Specifies the policy to be applied to emails that fail authentication (
none,quarantine, orreject). - rua=: Specifies the email address to which aggregate reports should be sent. These reports provide a summary of email authentication results.
- ruf=: Specifies the email address to which forensic reports should be sent. These reports provide detailed information about individual emails that failed authentication.
- adkim=: Specifies the DKIM alignment mode. ‘r’ for relaxed, ‘s’ for strict. Relaxed allows for subdomain matching.
- aspf=: Specifies the SPF alignment mode. ‘r’ for relaxed, ‘s’ for strict. Relaxed allows for subdomain matching.
- Start with p=none: It’s crucial to start with
p=noneto monitor your email traffic and identify any legitimate emails that might be failing authentication. Analyze the DMARC reports to understand the sources of your email and identify any misconfigurations or unauthorized sending sources. - Monitor DMARC Reports: Regularly review the aggregate reports (
rua) to identify any issues with your SPF and DKIM configurations. Look for unauthorized sending sources and investigate any emails that are failing authentication. - Gradually Increase the Policy: Once you’re confident that your SPF and DKIM configurations are correct and that you’re not inadvertently blocking legitimate emails, you can gradually increase the policy to
p=quarantineand thenp=reject. - Forensic Reports (ruf): Forensic reports can provide valuable insights into specific emails that are failing authentication. However, be aware that these reports may contain sensitive information, so handle them with care. Also, not all mail providers support sending forensic reports.
- Alignment Modes (adkim, aspf): Understanding alignment is critical. Strict alignment requires an exact match between the domain in the From header and the domain used for SPF/DKIM. Relaxed alignment allows for subdomain matching, which is often necessary when using services that send emails on behalf of your domain.
- Phase 1: Monitoring (p=none): Start with
v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com;. Monitor the reports for a few weeks or months to get a clear understanding of your email traffic. - Phase 2: Quarantine (p=quarantine): Once you’re confident, change the policy to
v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com;. This will cause emails that fail authentication to be moved to the spam folder. Continue monitoring the reports. - Phase 3: Reject (p=reject): Finally, change the policy to
v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com;. This will cause emails that fail authentication to be rejected entirely. Continue monitoring the reports.
Testing and Troubleshooting Authentication Records
After implementing SPF, DKIM, and DMARC, it’s essential to test your configuration to ensure it’s working correctly. This involves verifying that your DNS records are properly configured and that emails are being authenticated as expected. Troubleshooting issues can be challenging, but several tools and techniques can help. Tools for Testing Authentication Records Several online tools can help you verify your SPF, DKIM, and DMARC records:- MXToolbox: Provides a suite of tools for checking DNS records, including SPF, DKIM, and DMARC.
- DMARC Analyzer: Offers a DMARC record checker and reporting tools.
- EasyDMARC: Provides a user-friendly interface for managing and monitoring DMARC.
- Kitterman’s SPF Record Testing Tool: A simple tool for validating SPF records. http://www.kitterman.com/spf/validate.html
- Received-SPF: This header indicates the result of the SPF check. It should show “pass” if the email passed the SPF check.
- Authentication-Results: This header contains the results of both SPF and DKIM checks. Look for entries indicating “spf=pass” and “dkim=pass”.
- DMARC: This header may be present if the receiving server performed a DMARC check. It will indicate the DMARC policy that was applied.
Received-SPF: pass (google.com: domain of sender@example.com designates 203.0.113.10 as permitted sender) client-ip=203.0.113.10;
Authentication-Results: mx.google.com;
dkim=pass header.i=@example.com header.s=default header.b=abcdefg;
spf=pass (google.com: domain of sender@example.com designates 203.0.113.10 as permitted sender) smtp.mailfrom=sender@example.com;
dmarc=pass (p=none sp=none dis=none) header.from=example.com- SPF Fails:
- Problem: SPF record is missing or incorrect.
- Solution: Double-check the syntax of your SPF record. Ensure that all authorized sending sources are included. Use an SPF record checker to identify any errors. Pay attention to the 10 DNS lookup limit.
- DKIM Fails:
- Problem: DKIM signature is invalid or missing.
- Solution: Verify that your email server is properly configured to sign outgoing emails. Ensure that the public key in your DNS record matches the private key used by your email server. Check the selector in the DKIM-Signature header matches the selector used in your DNS record. Check time synchronization on your mail server, as DKIM signatures are time sensitive.
- DMARC Fails:
- Problem: Emails fail SPF and/or DKIM checks, and the DMARC policy is set to quarantine or reject.
- Solution: Investigate why the emails are failing SPF and/or DKIM checks. Check your SPF and DKIM configurations. Ensure that the From header domain aligns with the domain used for SPF and DKIM.
- DMARC Reports Not Received:
- Problem: You are not receiving DMARC reports at the specified email address.
- Solution: Ensure that the email address in the
ruatag is correct and can receive emails. Check your spam filter to ensure that DMARC reports are not being blocked. Some mail providers may not send DMARC reports, so test with multiple providers if possible.
- DNS Propagation Issues:
- Problem: Changes to your DNS records are not being reflected immediately.
- Solution: DNS changes can take up to 48 hours to propagate fully. Use online DNS propagation checkers to verify that your new records are visible from different locations.
include statements, you might exceed the 10 DNS lookup limit. This can cause SPF checks to fail. To resolve this, you can try:
- Consolidating Includes: If possible, combine multiple
includestatements into a singleincludestatement. - Using IP Addresses Directly: Replace
includestatements with direct IP addresses or ranges (ip4,ip6) if possible. - Flattening the SPF Record: Some tools can “flatten” your SPF record by resolving all
includestatements and replacing them with the corresponding IP addresses. Be careful with this approach, as it can make your SPF record very long and difficult to manage.
; Example of an SPF record exceeding the lookup limit
v=spf1 include:spf1.example.com include:spf2.example.com include:spf3.example.com include:spf4.example.com include:spf5.example.com include:spf6.example.com include:spf7.example.com include:spf8.example.com include:spf9.example.com -all
; Potential solution: Flattening the record (replace with actual IP addresses)
v=spf1 ip4:192.0.2.1 ip4:192.0.2.2 ip4:192.0.2.3 ip4:192.0.2.4 ip4:192.0.2.5 ip4:192.0.2.6 ip4:192.0.2.7 ip4:192.0.2.8 ip4:192.0.2.9 -all
