How to Stop Spam Bombing: Focusing on Email Server Configuration
Spam bombing, also known as email bombing, is a malicious attack where a victim is flooded with an overwhelming amount of spam emails. This can bury important emails, render email accounts unusable, and even be a precursor to other attacks. This article will focus specifically on configuring your email server to mitigate spam bombing, providing practical examples and configurations to bolster your defenses.
- Rate Limiting: A First Line of Defense
- Strengthening Authentication: SPF, DKIM, and DMARC
- Greylisting: Delaying the Inevitable (and Catching Spam)
- Advanced Filtering with SpamAssassin and ClamAV
- Monitoring and Logging for Early Detection
Rate Limiting: A First Line of Defense
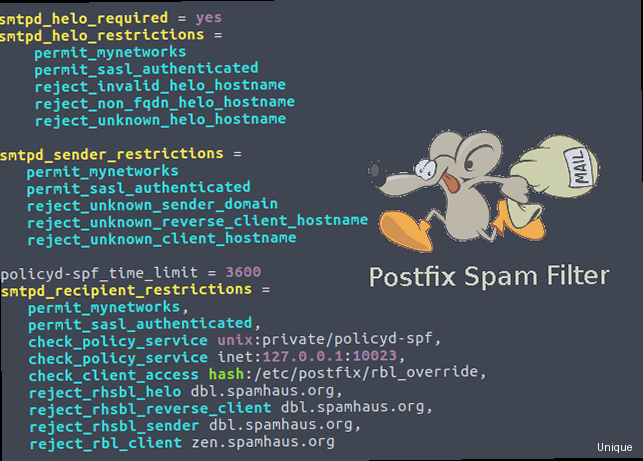
smtpd_client_connection_rate_limit = 5/etc/postfix/main.cf file limits each client IP address to a maximum of 5 simultaneous connections. After applying this change, you must restart Postfix for the changes to take effect.
sudo systemctl restart postfixsmtpd_client_message_rate_limit = 50
smtpd_client_recipient_rate_limit = 50/etc/postfix/main.cf, limit each client IP address to 50 messages per minute and 50 recipients per minute, respectively. A client exceeding these limits will be temporarily throttled. Again, restart Postfix after making these changes:
sudo systemctl restart postfixcheck_sender_access restriction.
Example: Rate limiting based on sender domain
First, create a file, for example, /etc/postfix/sender_rate_limits, with the following content:
example.com REJECT You are sending too much mail from this domain.
.example.net REJECT You are sending too much mail from this subdomain.example.com domain or any subdomain of example.net will be rejected with the specified message if they exceed the default rate limits. The dot before example.net indicates that all subdomains of example.net are affected.
Next, add the following line to your /etc/postfix/main.cf file:
smtpd_sender_restrictions =
permit_mynetworks,
reject_sender_login_mismatch,
reject_unauth_destination,
check_sender_access hash:/etc/postfix/sender_rate_limits,
permitsudo postmap hash:/etc/postfix/sender_rate_limits
sudo systemctl restart postfixStrengthening Authentication: SPF, DKIM, and DMARC
yourdomain.com. TXT "v=spf1 a mx ip4:192.0.2.0/24 include:thirdparty.com -all"v=spf1: Specifies the SPF version.a: Authorizes the IP address(es) of the hosts listed in the A record foryourdomain.com.mx: Authorizes the IP address(es) of the hosts listed in the MX record foryourdomain.com.ip4:192.0.2.0/24: Authorizes all IP addresses within the 192.0.2.0/24 CIDR block.include:thirdparty.com: Includes the SPF record ofthirdparty.com, authorizing any servers listed in their SPF record. This is useful for third-party email providers.-all: Specifies a hard fail for any emails originating from servers not listed in the SPF record. Other options include~all(soft fail) and?all(neutral). Using-allprovides the strongest protection against spoofing.
yourdomain.com. Emails originating from unauthorized servers will be flagged as potential spam or rejected outright, depending on the receiving server’s configuration.
DKIM: Adding a Digital Signature
DKIM adds a digital signature to your outgoing emails, allowing receiving servers to verify that the email has not been tampered with during transit and that it truly originated from your domain. This signature is generated using a private key and verified using a public key published in your DNS.
Example: Implementing DKIM with OpenDKIM (Postfix)
First, install OpenDKIM:
sudo apt update
sudo apt install opendkim opendkim-toolsopendkim-genkey -t -d yourdomain.com -s mailmail.private (the private key) and mail.txt (containing the public key). The -d option specifies your domain, and the -s option specifies the selector (mail in this case). The selector is used to distinguish between multiple DKIM keys for the same domain.
Move the private key to the OpenDKIM keys directory and set appropriate permissions:
sudo mv mail.private /etc/opendkim/keys/
sudo chown opendkim:opendkim /etc/opendkim/keys/mail.private
sudo chmod 600 /etc/opendkim/keys/mail.privatemail.txt file:
mail._domainkey.yourdomain.com. IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDmB... (rest of the public key) ...AQAB"/etc/opendkim.conf. Important settings include:
Domain yourdomain.com
KeyFile /etc/opendkim/keys/mail.private
Selector mail
Socket inet:8891@localhost
/etc/postfix/main.cf:
milter_default_action = accept
milter_protocol = 2
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = inet:127.0.0.1:8891sudo systemctl restart opendkim
sudo systemctl restart postfixyourdomain.com will now be signed with a DKIM signature. Receiving mail servers can verify this signature to ensure the email’s authenticity.
DMARC: Defining Policy for Unauthenticated Emails
DMARC builds upon SPF and DKIM by allowing you to specify how receiving mail servers should handle emails that fail SPF and/or DKIM checks. You can instruct them to reject, quarantine, or simply report such emails. DMARC also provides reporting mechanisms, allowing you to receive feedback on how your domain is being used.
Example: Creating a DMARC record
A DMARC record is a TXT record named _dmarc in your DNS zone file. Here’s an example:
_dmarc.yourdomain.com. TXT "v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:dmarc-forensic@yourdomain.com; adkim=s; aspf=s;"v=DMARC1: Specifies the DMARC version.p=reject: Instructs receiving servers to reject emails that fail SPF and DKIM checks. Other options includequarantine(move to spam folder) andnone(no action, only report). Starting withnoneis recommended to monitor the impact before enforcing stricter policies.rua=mailto:dmarc-reports@yourdomain.com: Specifies the email address to which aggregate reports should be sent. These reports provide summarized information about DMARC validation results.ruf=mailto:dmarc-forensic@yourdomain.com: Specifies the email address to which forensic reports (failure samples) should be sent. These reports provide detailed information about individual emails that failed DMARC validation.adkim=s: Specifies strict DKIM alignment. The DKIM domain must exactly match the domain in the “From:” header. “r” would specify relaxed alignment, where subdomains are allowed.aspf=s: Specifies strict SPF alignment. The SPF domain must exactly match the domain in the “From:” header. “r” would specify relaxed alignment, where subdomains are allowed.
yourdomain.com. Emails failing SPF and DKIM checks will be handled according to the specified policy (reject, quarantine, or none). You will receive aggregate and forensic reports, providing valuable insights into your email authentication performance and potential abuse.
Expert Tip: Start with a DMARC policy of p=none and monitor the reports for a few weeks to identify any legitimate email sources that are not properly authenticated. Adjust your SPF and DKIM records accordingly before moving to a stricter policy like p=quarantine or p=reject.
Greylisting: Delaying the Inevitable (and Catching Spam)
Greylisting is a spam filtering technique that temporarily rejects emails from unknown senders. The receiving server sends a temporary failure message (a 4xx SMTP error code) to the sending server. Legitimate mail servers will typically retry delivery after a short delay, while spammers, often using botnets with transient IP addresses, are less likely to retry. This delay helps to filter out a significant portion of spam. How Greylisting Works:- First Attempt: When an email arrives from a sender (identified by the sender’s IP address, sender email address, and recipient email address) that the server hasn’t seen before, the server temporarily rejects the email with a 4xx error.
- Temporary Failure: The sending server receives the temporary failure message and, if it’s a legitimate server, queues the email for retry.
- Retry: After a delay (typically a few minutes to a few hours), the sending server retries sending the email.
- Acceptance: The receiving server now recognizes the sender and accepts the email.
sudo apt update
sudo apt install postgrey/etc/postfix/main.cf:
smtpd_recipient_restrictions =
permit_mynetworks,
reject_unauth_destination,
check_policy_service inet:127.0.0.1:10023,
permit/etc/postgrey/postgrey_whitelist_clients and /etc/postgrey/postgrey_whitelist_recipients files.
For example, to whitelist a specific IP address, add it to /etc/postgrey/postgrey_whitelist_clients:
192.0.2.10 OK/etc/postgrey/postgrey_whitelist_recipients:
user@yourdomain.com OKsudo systemctl restart postgrey
sudo systemctl restart postfix- Delay: Greylisting introduces a delay in email delivery, typically between a few minutes and a few hours. This delay can be frustrating for users expecting immediate delivery.
- Legitimate Senders: Some legitimate senders might not retry after a temporary failure, resulting in lost emails. Whitelisting these senders is crucial.
- Configuration: Proper configuration of greylisting parameters (retry intervals, whitelist entries) is essential to balance spam reduction with email delivery speed.
Advanced Filtering with SpamAssassin and ClamAV
While rate limiting and authentication protocols provide a strong foundation for spam prevention, advanced filtering tools like SpamAssassin and ClamAV offer more sophisticated analysis of email content and attachments to identify and block spam and malware. SpamAssassin: Content Analysis and Heuristic Scoring SpamAssassin is a powerful spam filter that uses a variety of techniques, including header analysis, body content analysis, URIBL (Uniform Resource Identifier Blacklist) checks, and Bayesian filtering, to assign a spam score to each email. Emails exceeding a certain threshold are classified as spam and can be rejected, quarantined, or tagged. Example: Implementing SpamAssassin with Postfix First, install SpamAssassin:sudo apt update
sudo apt install spamassassinsudo systemctl start spamassassin/etc/postfix/master.cf:
spamassassin unix - n n - - pipe
flags=Rq user=debian-spamd argv=/usr/bin/spamc -e /usr/sbin/sendmail -oi -f $sender $recipient/etc/postfix/main.cf file:
content_filter = spamassassin:smtpd_recipient_restrictions in /etc/postfix/main.cf:
smtpd_recipient_restrictions =
permit_mynetworks,
reject_unauth_destination,
reject_rbl_client zen.spamhaus.org,
reject_rbl_client bl.spamcop.net,
permitsudo systemctl restart postfix- Configuration Files: SpamAssassin’s configuration files are located in
/etc/spamassassin. The main configuration file is/etc/spamassassin/local.cf. - Score Threshold: You can adjust the spam score threshold by setting the
required_scoreoption inlocal.cf. For example,required_score 4.0sets the threshold to 4.0. - Bayesian Filtering: SpamAssassin uses Bayesian filtering to learn from spam and ham (non-spam) emails. You can train the Bayesian filter by feeding it examples of spam and ham using the
sa-learncommand. - Rules: SpamAssassin uses a set of rules to identify spam. You can add custom rules to
local.cfto target specific types of spam.
sudo apt update
sudo apt install clamav clamav-daemonsudo systemctl start clamav-freshclam
sudo systemctl enable clamav-freshclam
sudo systemctl start clamav-daemon
sudo systemctl enable clamav-daemonclamav-milter:
sudo apt install clamav-milter/etc/clamav/clamav-milter.conf and ensure the following settings are correct:
# Run as user clamav
User clamav
# Allow e-mails to pass if clamd is down
# or returns an error
# ( Turned off by default. See man clamav-milter.conf )
# ExitOnClamdError Yes
# Always block the e-mail if an error occurs.
ExitOnClamdError Yes
# Do not log clean files
LogClean No
# Define the relay domain
RelayLocalDomain yourdomain.com
# Define the internal network
RelayLocalNet 127.0.0.1
# Run in background?
# (default: no)
Foreground nosmtpd_milters = inet:127.0.0.1:10025
non_smtpd_milters = inet:127.0.0.1:10025
milter_default_action = acceptsudo systemctl restart clamav-milter
sudo systemctl restart postfix- Resource Usage: SpamAssassin and ClamAV can be resource-intensive, especially when processing large emails or attachments. Ensure your server has sufficient resources to handle the load.
- False Positives: Advanced filtering tools can sometimes generate false positives, incorrectly identifying legitimate emails as spam or malware. Regularly monitor your spam and quarantine folders to identify and release any false positives.
- Regular Updates: Keep SpamAssassin’s rules and ClamAV’s virus signatures up-to-date to ensure they can effectively detect the latest threats. ClamAV’s
freshclamtool automatically downloads signature updates.
Monitoring and Logging for Early Detection
Effective monitoring and logging are crucial for detecting and responding to spam bombing attacks. By continuously monitoring your email server logs, you can identify suspicious activity, such as sudden spikes in email volume, unusual sender patterns, and increased bounce rates. Analyzing Email Server Logs Email server logs contain valuable information about email activity, including sender IP addresses, recipient addresses, timestamps, and delivery status. Analyzing these logs can help you identify the source and characteristics of a spam bombing attack. Example: Analyzing Postfix logs Postfix logs its activity to the system log, typically/var/log/mail.log or /var/log/maillog. You can use command-line tools like grep, awk, and sed to extract specific information from these logs.
To find all emails rejected due to rate limiting, you can use the following command:
grep "rate limit" /var/log/mail.log/var/log/mail.log file for lines containing the phrase “rate limit.” The output will show you the IP addresses and timestamps of the senders who exceeded the rate limits.
To find all emails that were rejected by SpamAssassin, you can use the following command:
grep "SpamAssassin" /var/log/mail.log | grep "reject"/var/log/mail.log file for lines containing “SpamAssassin” and “reject,” indicating that SpamAssassin rejected the email.
To count the number of emails received from a specific IP address, you can use the following command:
grep "from=user@example.com" /var/log/mail.log | wc -luser@example.com with the email address you want to investigate. The wc -l command counts the number of lines matching the search criteria, giving you the total number of emails received from that sender.
Setting Up Monitoring Alerts
Manually analyzing logs can be time-consuming and inefficient. Setting up automated monitoring alerts allows you to be notified immediately when suspicious activity is detected. Several tools can be used for monitoring and alerting, including:
- Fail2Ban: Fail2Ban monitors log files for failed login attempts and other suspicious activity and automatically blocks the offending IP addresses using firewall rules. While primarily used for SSH brute-force attacks, it can also be configured to monitor email server logs for spam-related patterns.
- Logwatch: Logwatch is a log analysis tool that summarizes log activity and sends reports via email. You can configure Logwatch to monitor your email server logs and alert you to any unusual activity, such as a sudden increase in spam volume or a high number of rejected emails.
- Nagios/Icinga: Nagios and Icinga are comprehensive monitoring systems that can monitor a wide range of server metrics, including email server performance, queue length, and spam volume. You can configure Nagios/Icinga to send alerts when any of these metrics exceed predefined thresholds.
/etc/fail2ban/filter.d/postfix-spam.conf) with the following content:
[Definition]
failregex = reject: RCPT from .*\[\]: 554 5.7.1 .* Access denied - Invalid HELO name \
Client host rejected: cannot find your hostname
ignoreregex = 