
How to Configure an SPF Record for Office 365
Ensuring your emails reach their intended recipients’ inboxes is crucial for effective communication. One of the fundamental steps in achieving this is properly configuring your Sender Policy Framework (SPF) record. This article provides a comprehensive guide on how to configure an SPF record specifically for Office 365, enhancing your email deliverability and protecting your domain from spoofing.
This guide will cover everything from the basics of SPF records and their importance to the specific syntax required for Office 365 and practical examples to help you implement the configuration correctly. We will also delve into troubleshooting common issues and best practices for maintaining your SPF record.
Understanding SPF Records and Their Importance
SPF, or Sender Policy Framework, is an email authentication method designed to prevent spammers from sending messages with forged ‘From’ addresses at your domain. An SPF record is a type of Domain Name System (DNS) record that identifies which mail servers are permitted to send email on behalf of your domain. When a receiving mail server receives an email claiming to be from your domain, it checks your SPF record to verify whether the sending server is authorized. If the sending server is not listed in the SPF record, the receiving server may mark the email as spam or reject it outright. Understanding the core components and syntax is crucial for crafting an effective SPF record.
Without a properly configured SPF record, your domain is vulnerable to email spoofing, where malicious actors can send emails that appear to be from your domain. This can damage your reputation, lead to phishing attacks, and decrease the deliverability of your legitimate emails. Conversely, a well-configured SPF record increases the likelihood that your emails will reach the inbox and builds trust with receiving mail servers.
Key Components of an SPF Record
An SPF record is a single line of text that consists of several mechanisms and qualifiers. These components determine how a receiving mail server should handle emails from your domain.
- Version: SPF records always start with
v=spf1, indicating the SPF version being used. - Mechanisms: These define the authorized sending sources. Common mechanisms include:
ip4: Specifies individual IPv4 addresses or ranges.ip6: Specifies individual IPv6 addresses or ranges.a: Allows email to be sent from the IP address of the domain specified.mx: Allows email to be sent from the IP addresses listed in the MX records for the domain.include: Includes the SPF record of another domain. This is commonly used to delegate SPF authorization to third-party email services.all: Matches all IP addresses. It should be used carefully and typically with a qualifier (e.g.,-allor~all).
- Qualifiers: These modify the behavior of mechanisms. Common qualifiers include:
+: Pass (default). If the mechanism matches, the email passes the SPF check.-: Fail. If the mechanism matches, the email fails the SPF check.~: Softfail. If the mechanism matches, the email is likely a forgery but is still accepted. The email is usually marked as spam.?: Neutral. The SPF record makes no assertion about the email.
The include mechanism is particularly important for Office 365, as it allows you to incorporate Microsoft’s infrastructure into your SPF record.
The Importance of SPF Records for Email Deliverability
Email deliverability is critical for any organization that relies on email communication. SPF records play a pivotal role in ensuring that your emails are delivered to the intended recipients’ inboxes, rather than being marked as spam or rejected. By verifying the sender’s authenticity, SPF records help to establish trust between your domain and receiving mail servers. This trust can improve your sender reputation, which directly impacts your email deliverability rates.
Without an SPF record, receiving mail servers have no way of knowing whether an email claiming to be from your domain is legitimate or not. This makes it easier for spammers to spoof your domain, leading to potential phishing attacks and damage to your reputation. Furthermore, many modern email providers, such as Gmail and Outlook, heavily rely on SPF records as part of their spam filtering processes. If your domain does not have a properly configured SPF record, your emails are more likely to be flagged as spam and may never reach the inbox.
Here are some examples demonstrating the impact of SPF records on email deliverability:
- Example 1: A company sends out a marketing campaign to 10,000 subscribers. Without an SPF record, 30% of the emails are marked as spam or rejected by receiving mail servers.
- Example 2: The same company implements a properly configured SPF record. The percentage of emails marked as spam or rejected drops to 5%, significantly improving the campaign’s reach and effectiveness.
- Example 3: A small business uses Office 365 for its email communication but neglects to configure an SPF record. Hackers are able to spoof the business’s domain and send phishing emails to customers, damaging the business’s reputation and resulting in financial losses.
“A properly configured SPF record is the first line of defense against email spoofing and a critical component of any email deliverability strategy.” Email Security Expert
Creating Your SPF Record for Office 365
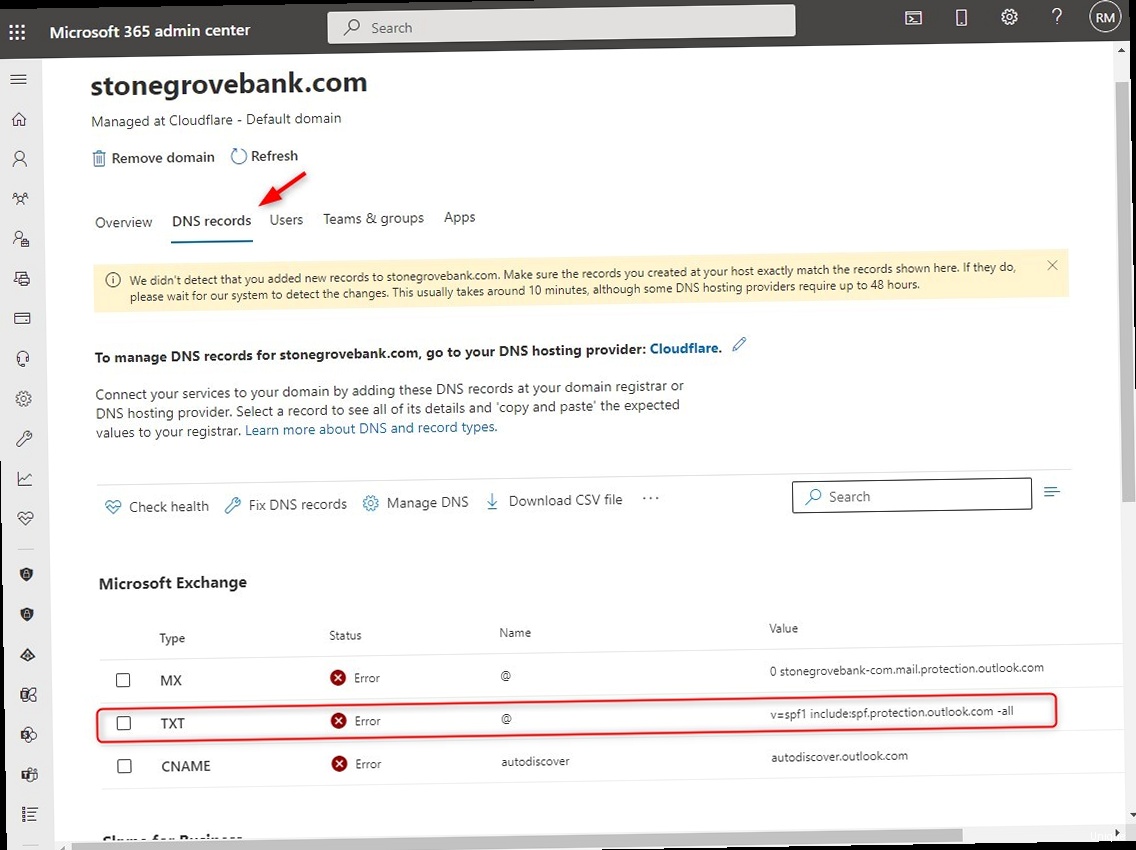
Creating an SPF record for Office 365 involves understanding the specific requirements and syntax needed for Microsoft’s infrastructure. The core element is the include mechanism, which delegates SPF authorization to Office 365’s mail servers. It’s also important to consider any other email services you might be using, as you’ll need to include them in your SPF record as well.
The Basic SPF Record for Office 365
The fundamental SPF record for Office 365 includes the following:
v=spf1 include:spf.protection.outlook.com -allLet’s break down this record:
v=spf1: Specifies the SPF version 1.include:spf.protection.outlook.com: This is the key part. It tells receiving mail servers to consult the SPF record forspf.protection.outlook.com, which lists all the authorized sending IP addresses for Office 365.-all: This signifies that any server not explicitly authorized by the SPF record should be considered unauthorized. The hyphen indicates a “fail” result, meaning the email should be rejected.
This basic record covers the majority of Office 365 scenarios. However, if you use other services to send email on behalf of your domain, you’ll need to add them to your SPF record.
Adding Additional Email Services to Your SPF Record
If you use other email services besides Office 365, such as a marketing automation platform or a transactional email service, you need to include their SPF records in your SPF record. Failing to do so can result in those emails being marked as spam or rejected.
Here’s how you can add other email services:
- Identify the SPF record for the other service: Most email service providers (ESPs) will provide you with the correct
includestatement or IP addresses to use in your SPF record. For example, Mailchimp’s SPF record isinclude:servers.mcsv.net. - Combine the SPF records: Add the
includestatement for the other service to your existing SPF record. It’s crucial to keep the total number of DNS lookups under 10.
Here’s an example of an SPF record that includes both Office 365 and Mailchimp:
v=spf1 include:spf.protection.outlook.com include:servers.mcsv.net -allSimilarly, if you use SendGrid, you would add include:sendgrid.net:
v=spf1 include:spf.protection.outlook.com include:sendgrid.net -allIf you have dedicated servers sending email, you can include them via their IP address. Make sure to use ip4 for IPv4 addresses and ip6 for IPv6 addresses. For example:
v=spf1 include:spf.protection.outlook.com ip4:192.0.2.0/24 ip6:2001:db8::/32 -allIn this example, ip4:192.0.2.0/24 allows email from any IP address within the 192.0.2.0/24 range, and ip6:2001:db8::/32 allows email from any IP address within the 2001:db8::/32 range.
Important Note: You should only have one SPF record per domain. Multiple SPF records can cause authentication failures.
Avoiding Common SPF Record Mistakes
Creating an effective SPF record involves avoiding several common pitfalls that can hinder its effectiveness.
- Exceeding the DNS Lookup Limit: SPF records are limited to 10 DNS lookups. The
includemechanism counts as one lookup, and nestedincludestatements can quickly increase the lookup count. If you exceed the limit, your SPF record may not be fully evaluated, leading to authentication failures. To avoid this, try to flatten your SPF record by replacingincludestatements with IP addresses where possible. - Using the
aandmxMechanisms Inappropriately: Theaandmxmechanisms allow email to be sent from the IP addresses associated with your domain’s A and MX records, respectively. However, using these mechanisms without careful consideration can create security vulnerabilities. Ensure that only authorized mail servers are listed in your A and MX records. - Misusing the
allMechanism: Theallmechanism matches all IP addresses, which can be problematic if not used correctly. Using+alleffectively disables SPF protection. It’s generally recommended to use-all(fail) or~all(softfail) to indicate how unauthorized emails should be handled. - Forgetting to Update Your SPF Record: As your email infrastructure evolves, it’s crucial to update your SPF record accordingly. If you add or remove email services, change IP addresses, or modify your domain’s DNS settings, make sure to update your SPF record to reflect these changes.
By understanding and avoiding these common mistakes, you can create a robust and effective SPF record that enhances your email deliverability and protects your domain from spoofing.
Expert Tip: Regularly review your SPF record to ensure it accurately reflects your current email sending practices. Schedule a quarterly review to catch any potential issues early.
Implementing Your SPF Record in Your DNS Settings
Once you’ve created your SPF record, you need to add it to your domain’s DNS settings. This involves accessing your DNS management interface, typically provided by your domain registrar or hosting provider, and creating a TXT record with your SPF record’s value.
Accessing Your DNS Management Interface
The process for accessing your DNS management interface varies depending on your domain registrar or hosting provider. Here are some common scenarios:
- Domain Registrar: If you purchased your domain from a registrar like GoDaddy, Namecheap, or Google Domains, you’ll typically manage your DNS settings through their web interface. Log in to your account, navigate to the domain management section, and look for DNS settings or DNS records.
- Hosting Provider: If your domain is hosted with a provider like SiteGround, Bluehost, or AWS, you’ll manage your DNS settings through their hosting control panel. Log in to your hosting account, navigate to the domain management section, and look for DNS settings or a DNS zone editor.
- Cloud DNS Service: If you use a cloud DNS service like Cloudflare or Amazon Route 53, you’ll manage your DNS settings through their web interface. Log in to your account and navigate to the DNS management section.
Once you’ve accessed your DNS management interface, you’re ready to add your SPF record.
Adding the SPF Record as a TXT Record
SPF records are implemented as TXT (Text) records in your DNS zone file. Here’s how to add a TXT record for your SPF record:
- Record Type: Select “TXT” as the record type.
- Host/Name: In most cases, you’ll enter “@” to indicate the root domain, or leave it blank. Some DNS providers may require your domain name.
- Value/Content: Enter your SPF record string. For example:
v=spf1 include:spf.protection.outlook.com -all - TTL (Time to Live): This specifies how long DNS servers should cache the record. A typical TTL is 3600 seconds (1 hour), but you can adjust it based on your needs. Lower TTLs allow for faster propagation of changes, while higher TTLs reduce DNS server load.
Here’s an example of how the SPF record might look in a DNS management interface:
| Record Type | Host/Name | Value/Content | TTL |
|---|---|---|---|
| TXT | @ | v=spf1 include:spf.protection.outlook.com -all | 3600 |
After entering the information, save the record. It may take some time for the DNS changes to propagate across the internet, so be patient.
Example Scenarios for Different DNS Providers
Let’s look at some specific examples for popular DNS providers:
- GoDaddy:
- Log in to your GoDaddy account.
- Go to your Domain Control Center.
- Select your domain and click “DNS.”
- Click “Add” under the Records section.
- Choose “TXT” from the Type menu.
- Enter “@” in the Host field.
- Enter your SPF record string in the TXT Value field.
- Choose a TTL value.
- Click “Save.”
- Cloudflare:
- Log in to your Cloudflare account.
- Select your domain.
- Click the “DNS” icon.
- Under DNS records, click “Add record.”
- Choose “TXT” from the Type menu.
- Enter “@” in the Name field.
- Enter your SPF record string in the Content field.
- Choose a TTL value.
- Click “Save.”
- AWS Route 53:
- Open the Route 53 console.
- In the navigation pane, choose “Hosted zones.”
- Choose the hosted zone that matches your domain name.
- Choose “Create record.”
- Choose “TXT” for the record type.
- Leave the “Record name” field blank to create a record for the domain.
- Enter your SPF record string in the “Value” field.
- Choose a TTL value.
- Choose “Create records.”
These examples provide a general overview of the process. Consult your DNS provider’s documentation for specific instructions.
After adding your SPF record, it’s important to test it to ensure it’s working correctly.
Testing and Troubleshooting Your SPF Record
After implementing your SPF record, it’s crucial to test its configuration and troubleshoot any potential issues. This ensures that your email authentication is working correctly and that your emails are being delivered as expected.
Using Online SPF Record Checkers
Several online tools can help you verify the syntax and functionality of your SPF record. These tools query your domain’s DNS records and provide feedback on whether your SPF record is valid and correctly configured.
Here are a few popular online SPF record checkers:
- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx – This tool provides a comprehensive analysis of your SPF record, including syntax validation and DNS lookup checks.
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/ – Dmarcian’s tool not only checks your SPF record but also provides insights into your overall email authentication setup.
- SPF Record Testing Tools: Many other free online tools are available by searching “SPF record checker” on your preferred search engine.
To use these tools, simply enter your domain name and click “Check” or “Lookup.” The tool will then display your SPF record and any potential issues.
Here’s an example of what you might see in MXToolbox:
If your SPF record is valid, the tool will display a message like “SPF record found and is valid.” If there are any errors, the tool will provide detailed information about the issue, such as syntax errors, DNS lookup limits, or invalid mechanisms.
Common SPF Record Issues and Troubleshooting Steps
Even with careful planning, SPF records can sometimes encounter issues. Here are some common problems and how to troubleshoot them:
- Syntax Errors: SPF records are sensitive to syntax errors. Double-check your SPF record for typos, missing spaces, or incorrect delimiters. Even a small error can cause the entire record to be invalid.
- DNS Lookup Limit Exceeded: As mentioned earlier, SPF records are limited to 10 DNS lookups. If your record exceeds this limit, it may not be fully evaluated. Use the online SPF record checkers to identify the number of lookups and try to reduce them by flattening your SPF record.
- Multiple SPF Records: You should only have one SPF record per domain. If you have multiple SPF records, receiving mail servers may not know which one to use, leading to authentication failures. Remove any duplicate SPF records and consolidate them into a single record.
- Incorrect
includeStatements: Make sure that yourincludestatements are correct and point to valid SPF records. Verify that the domain names in theincludestatements are spelled correctly and that the corresponding SPF records exist. - Propagation Delays: After making changes to your SPF record, it may take some time for the changes to propagate across the internet. This delay can vary depending on your TTL settings and the DNS servers being used. Be patient and allow sufficient time for the changes to propagate before testing your SPF record.
Here are a few troubleshooting scenarios:
- Scenario 1: You receive reports that your emails are being marked as spam. Use an SPF record checker to verify your SPF record. If the tool reports a syntax error, correct the error and save the changes. Wait for the changes to propagate and test again.
- Scenario 2: You add a new email service to your domain but forget to update your SPF record. Emails sent from the new service are being rejected. Add the appropriate
includestatement to your SPF record and save the changes. Wait for the changes to propagate and test again. - Scenario 3: You change your domain’s IP address but forget to update your SPF record. Emails sent from the old IP address are being rejected. Update your SPF record with the new IP address and remove the old IP address. Save the changes and wait for the changes to propagate.
By following these troubleshooting steps, you can quickly identify and resolve common SPF record issues and ensure that your email authentication is working correctly.
In conclusion, implementing and maintaining a correct SPF record is vital for protecting your domain’s reputation and ensuring emails reach inboxes. Regularly test the SPF record to mitigate deliverability issues and safeguard against potential spoofing.
Article Monster
Email marketing expert sharing insights about cold outreach, deliverability, and sales growth strategies.