
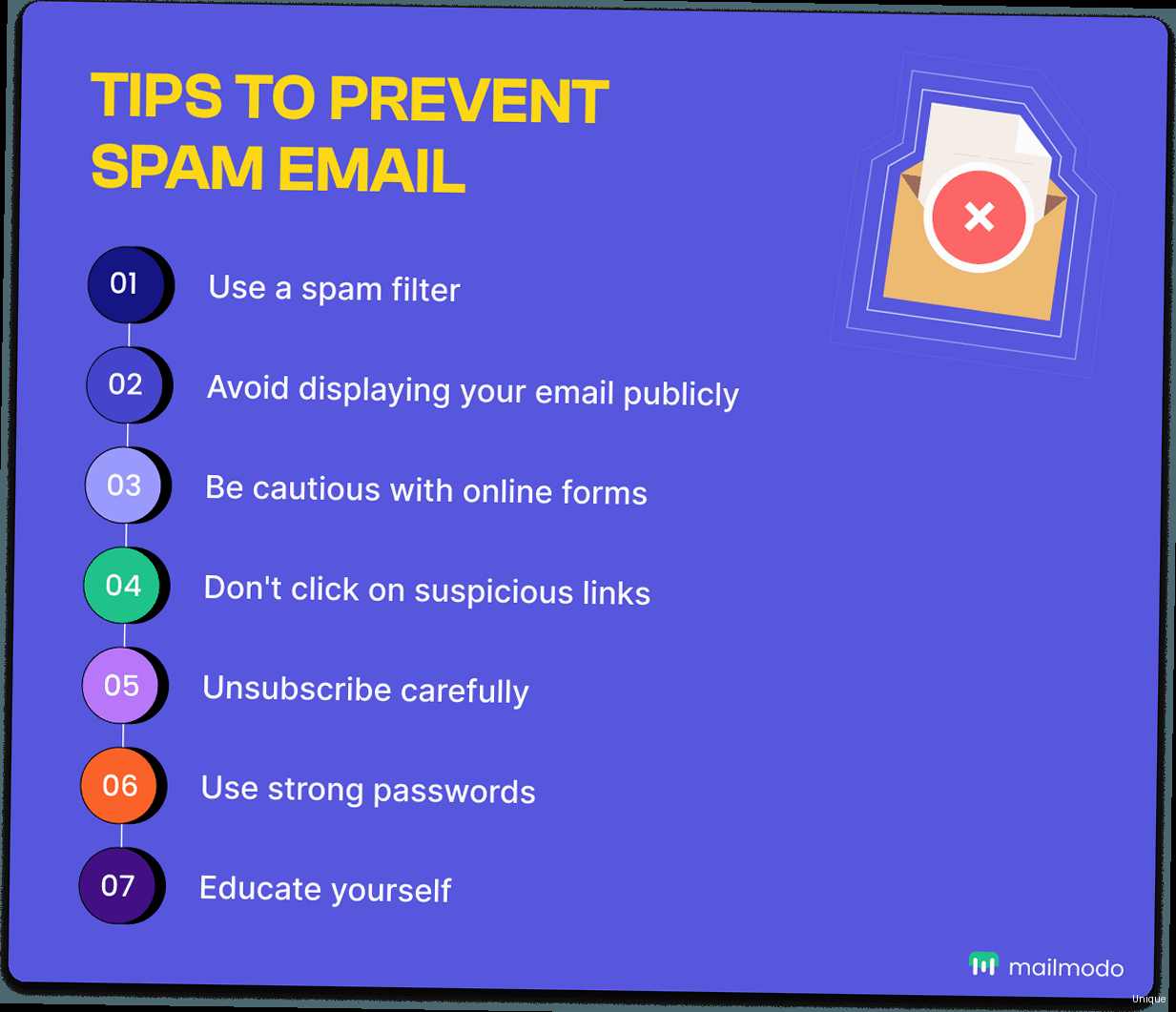
Improving Email Deliverability: Advanced Methods to Banish Spam
Email deliverability is the cornerstone of effective email marketing and communication. In this article, we’ll dive into advanced techniques that go beyond basic spam prevention, ensuring your emails reach the intended recipient’s inbox. We’ll cover topics like SPF, DKIM, and DMARC authentication, implementing feedback loops, managing IP reputation, and optimizing your email content to avoid spam filters. Get ready to take your email strategy to the next level and maximize your email deliverability rates.
Email Authentication: SPF, DKIM, and DMARC
Understanding SPF (Sender Policy Framework)
SPF is an email authentication protocol that allows you to specify which mail servers are authorized to send emails on behalf of your domain. It works by creating a DNS record that lists all the IP addresses or domains that are permitted to send emails from your domain. When a receiving mail server receives an email, it checks the SPF record to verify that the sending server is authorized. Example 1: Setting up an SPF record To set up an SPF record, you need to create a TXT record in your domain’s DNS settings. Here’s an example:v=spf1 ip4:192.0.2.0/24 ip4:198.51.100.123 include:_spf.example.com -allv=spf1: Specifies the SPF version.ip4:192.0.2.0/24: Allows emails from IP addresses within the 192.0.2.0/24 range.ip4:198.51.100.123: Allows emails from the IP address 198.51.100.123.include:_spf.example.com: Includes the SPF record of _spf.example.com, which is often used for third-party email services.-all: Specifies that any email not matching the above rules should be rejected. A softer fail would be represented by `~all` which means “softfail” and indicates the email should be accepted but marked.
- Exceeding the 10 DNS lookup limit: SPF records are limited to 10 DNS lookups. If you exceed this limit, your SPF record may be ignored. To avoid this, consolidate your SPF record and use
includestatements sparingly. Consider using mechanisms like `ip4` or `ip6` instead of multiple includes if possible. - Using multiple SPF records: You should only have one SPF record per domain. Multiple SPF records will cause confusion and can lead to authentication failures. Merge your existing SPF records into a single record.
Understanding DKIM (DomainKeys Identified Mail)
DKIM adds a digital signature to your emails, verifying that the email was sent from your domain and that the content has not been altered in transit. The signature is generated using a private key and verified by the receiving mail server using a public key published in your domain’s DNS records. Example 1: Setting up a DKIM record Setting up DKIM involves generating a public/private key pair. The private key is used to sign your emails, while the public key is added to your DNS record. Here’s how a DKIM record might look:default._domainkey.example.com. IN TXT "v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwL1..."default._domainkey.example.com: This is the selector and domain. The “default” selector can be changed based on your needs.v=DKIM1: Specifies the DKIM version.k=rsa: Specifies the key type (RSA).p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwL1...: This is the public key. It’s a long string of characters that corresponds to the private key used to sign your emails.
Understanding DMARC (Domain-based Message Authentication, Reporting & Conformance)
DMARC builds upon SPF and DKIM, providing instructions to receiving mail servers on how to handle emails that fail SPF and DKIM checks. It also allows you to receive reports about email authentication failures, helping you identify and address potential issues. DMARC is crucial for preventing email spoofing and phishing attacks. Example 1: Setting up a DMARC record A DMARC record specifies the policy for handling emails that fail SPF and DKIM checks. Here’s an example:_dmarc.example.com. IN TXT "v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; adkim=r; aspf=r;"v=DMARC1: Specifies the DMARC version.p=quarantine: Specifies the policy for handling failing emails. Options arenone(no action),quarantine(mark as spam), andreject(reject the email). Starting with `p=none` is highly recommended to monitor the effect of the DMARC policy before enforcing a stricter policy.rua=mailto:dmarc-reports@example.com: Specifies the email address to which aggregate reports should be sent.ruf=mailto:dmarc-forensic@example.com: Specifies the email address to which forensic reports (detailed failure reports) should be sent.- `adkim=r`: DKIM alignment mode. `r` is relaxed, `s` is strict.
- `aspf=r`: SPF alignment mode. `r` is relaxed, `s` is strict.
p=none to monitor your email authentication results before enforcing a stricter policy like p=quarantine or p=reject. This allows you to identify and fix any issues without disrupting legitimate email delivery. Gradually move towards stricter policies as you gain confidence in your authentication setup.
Expected Output/Result: Implementing DMARC helps protect your domain from email spoofing and phishing attacks, improves email deliverability, and provides valuable insights into your email authentication performance through DMARC reports.
Leveraging Feedback Loops (FBLs)
Understanding the Feedback Loop Process
The FBL process works as follows:- A subscriber marks an email as spam within their email client (e.g., Gmail, Outlook).
- The ISP generates a report containing information about the email, including the sender’s IP address and message ID.
- The ISP sends this report to the email sender’s designated FBL address.
- The email sender analyzes the report and removes the subscriber from their email list.
- Gmail: https://support.google.com/mail/answer/6227052?hl=en (via Google Postmaster Tools)
- Microsoft (Outlook, Hotmail): https://sendersupport.olc.protection.outlook.com/pm/services.aspx
- Yahoo: (Yahoo no longer offers a direct FBL. Use their Complaint Feedback Loop program via their postmaster site for similar data)
<?xml version="1.0" encoding="UTF-8"?>
<feedback>
<report_id>1234567890</report_id>
<feedback_type>abuse</feedback_type>
<user_agent>Gmail</user_agent>
<date>2024-10-27T10:00:00Z</date>
<source_ip>203.0.113.1</source_ip>
<authentication_results>
<dkim>pass</dkim>
<spf>pass</spf>
</authentication_results>
<reported_domain>example.com</reported_domain>
<message>
<id> </id>
<headers>
<from>sender@example.com</from>
<to>recipient@example.net</to>
<subject>Your Newsletter</subject>
</headers>
</message>
<removal_request>
<email>recipient@example.net</email>
</removal_request>
</feedback>
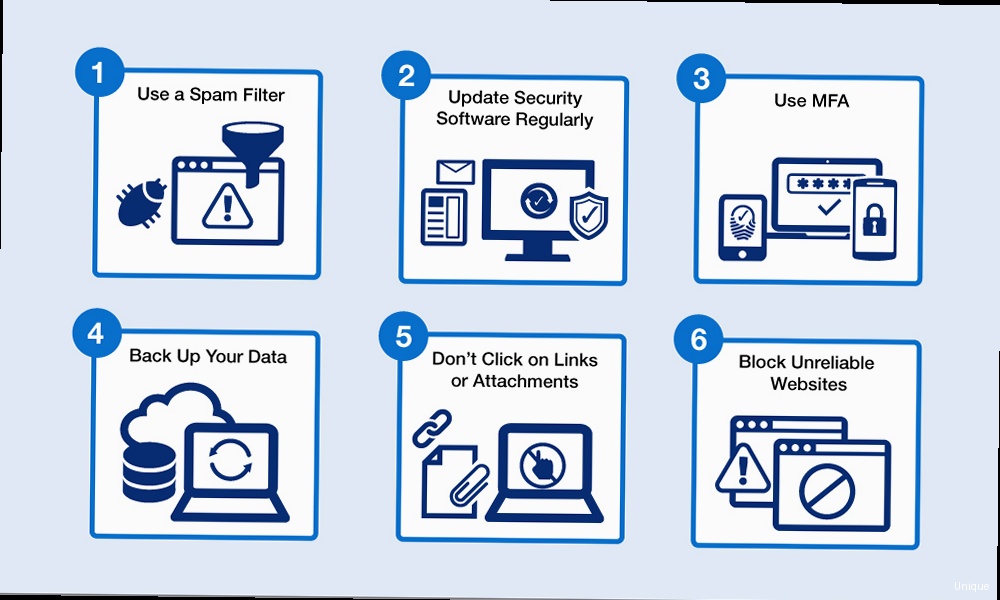
Monitoring and Maintaining IP Reputation
Your IP address’s reputation is a critical factor in determining whether your emails reach the inbox or end up in the spam folder. ISPs use various metrics to assess your IP’s reputation, including spam complaints, bounce rates, and engagement rates. Monitoring and actively managing your IP reputation is essential for maintaining high deliverability rates. This section will explore the tools and techniques you can use to monitor your IP reputation and the steps you can take to improve it if necessary.Understanding IP Reputation Metrics
Several key metrics contribute to your IP reputation:- Spam Complaints: The number of recipients who mark your emails as spam. A high spam complaint rate is a major red flag for ISPs.
- Bounce Rate: The percentage of emails that are returned as undeliverable. High bounce rates can indicate that you are sending emails to invalid or inactive email addresses. Soft bounces (temporary delivery issues) are less impactful than hard bounces (permanent failures).
- Engagement Rate: The percentage of recipients who open, click, or interact with your emails. High engagement rates signal to ISPs that your emails are valuable and relevant to recipients.
- Blocklist Status: Whether your IP address is listed on any public or private blocklists. Being blocklisted can severely impact your deliverability.
- Volume and Consistency: Sudden spikes in email volume or inconsistent sending patterns can trigger spam filters.
- MXToolbox: https://mxtoolbox.com/blacklists.aspx
- WhatIsMyIPAddress: https://whatismyipaddress.com/blacklist-check
- MultiRBL: https://multirbl.valli.org/
| Factor | Impact on Reputation | Mitigation Strategy |
|---|---|---|
| Spam Complaints | Negative | Implement FBLs, improve email content, segment your list. |
| Bounce Rate | Negative | Clean your list regularly, use double opt-in. |
| Engagement Rate | Positive | Send relevant content, personalize your emails, segment your list. |
| Blocklist Status | Very Negative | Identify the cause, take steps to get removed from the blocklist. |
| Sending Volume | Potentially Negative (if sudden spikes) | Warm up new IPs gradually, maintain consistent sending patterns. |
Content Optimization for Inbox Placement
The content of your emails plays a significant role in determining whether they reach the inbox or end up in the spam folder. Spam filters are sophisticated and can analyze various aspects of your email content, including the subject line, body text, images, and links. Optimizing your email content to avoid triggering spam filters is crucial for improving your deliverability. This section will explore the best practices for content optimization, including avoiding spam trigger words, using proper formatting, and testing your emails before sending them.Avoiding Spam Trigger Words and Phrases
Certain words and phrases are commonly associated with spam and can trigger spam filters. Avoiding these “spam trigger words” can significantly improve your chances of reaching the inbox. Examples include:- “Free” (especially when overused)
- “Guarantee”
- “Limited time offer”
- “Act now!”
- “Click here!”
- “Dear friend” (generic salutations)
- Excessive use of exclamation points (!!!!!)
- ALL CAPS
Using Proper Formatting and Design
Proper formatting and design are essential for creating emails that are both visually appealing and deliverable. Here are some key best practices:- Use a balanced text-to-image ratio: Avoid using too many images and not enough text. A good rule of thumb is to maintain a ratio of at least 60% text to 40% images.
- Use alt text for images: Always include alt text for your images. This helps ensure that your message is still conveyed even if the images are blocked.
- Keep your HTML code clean: Avoid using unnecessary or outdated HTML code. Invalid HTML can trigger spam filters.
- Use responsive design: Ensure that your emails are mobile-friendly and display correctly on all devices.
- Avoid using excessive colors and fonts: Stick to a limited color palette and font selection to create a professional and readable email.
Testing Your Emails Before Sending
Before sending your emails to your entire list, it’s crucial to test them to ensure that they’re not triggering spam filters and that they display correctly on different email clients. Here are some testing tools you can use:- Mail-Tester: https://www.mail-tester.com/ This tool provides a detailed analysis of your email’s content, authentication, and formatting, giving you a spam score and recommendations for improvement.
- Litmus: https://www.litmus.com/ Litmus allows you to preview your emails on different email clients and devices, ensuring that they display correctly for all recipients.
- Email on Acid: https://www.emailonacid.com/ Similar to Litmus, Email on Acid provides email previews and testing tools to help you optimize your emails for deliverability.
Advanced List Hygiene and Management
Even with the best authentication and content optimization practices, poor list management can severely impact your email deliverability. Sending emails to inactive subscribers, invalid email addresses, or subscribers who have unsubscribed can damage your sender reputation and lead to higher spam complaint rates. This section delves into advanced list hygiene and management techniques to keep your email list healthy and engaged.Implementing Double Opt-In
Double opt-in is the process of requiring subscribers to confirm their email address before being added to your email list. This helps ensure that you are only sending emails to subscribers who genuinely want to receive them. Double opt-in significantly reduces the risk of adding invalid or misspelled email addresses to your list and can improve your overall engagement rates. Example 1: Setting up Double Opt-In After a user submits their email address through your signup form, send them a confirmation email with a unique link. The user must click this link to confirm their subscription. Only after they click the link should you add them to your active mailing list. The confirmation email should clearly state the purpose of the email and instruct the user to click the link to confirm their subscription. Here’s an example confirmation email:Subject: Confirm Your Subscription to [Your Company Name]
Dear [Subscriber Name],
Thank you for subscribing to our newsletter!
Please click the link below to confirm your subscription:
[Confirmation Link]
If you did not subscribe to our newsletter, please ignore this email.
Sincerely,
The [Your Company Name] Team
Regularly Cleaning Your Email List
Even with double opt-in, your email list can still accumulate inactive subscribers and invalid email addresses over time. Regularly cleaning your email list is essential for maintaining high deliverability rates. Here are some techniques for cleaning your email list:- Remove hard bounces: Hard bounces indicate that the email address is invalid and will never be deliverable. Immediately remove these email addresses from your list.
- Remove unsubscribes: Respect all unsubscribe requests and promptly remove subscribers who have opted out of your emails.
- Identify and remove inactive subscribers: Subscribers who haven’t opened or clicked your emails in a certain period (e.g., 6-12 months) are considered inactive. Try sending a re-engagement campaign to these subscribers to see if you can win them back. If they still don’t engage, remove them from your list.
- Correct typos and errors: Look for common typos in email addresses (e.g., “gmai.com” instead of “gmail.com”) and correct them.
- A personalized email asking them if they still want to receive your emails.
- An offer or incentive to re-engage with your brand.
- A clear unsubscribe link.
Subject: Are We Still Friends?
Dear [Subscriber Name],
We've noticed that you haven't opened our emails in a while. We miss you!
Are you still interested in receiving our newsletter and exclusive offers?
If so, click the link below to stay subscribed:
[Confirmation Link]
If you're no longer interested, you can unsubscribe here:
[Unsubscribe Link]
We value your privacy and only want to send emails to people who want to receive them.
Sincerely,
The [Your Company Name] Team
sell Tags
Article Monster
Email marketing expert sharing insights about cold outreach, deliverability, and sales growth strategies.