
SPF Record for Yahoo Mail: Ensuring Deliverability
In today’s digital landscape, ensuring your emails reach their intended recipients is paramount. Yahoo Mail, like other major email providers, uses Sender Policy Framework (SPF) records to verify the authenticity of sending servers. This article will provide a comprehensive guide on configuring SPF records specifically for Yahoo Mail, covering essential aspects like syntax, common mistakes, and best practices to maximize your email deliverability and prevent your messages from landing in the spam folder.
Understanding SPF and Yahoo Mail’s Requirements
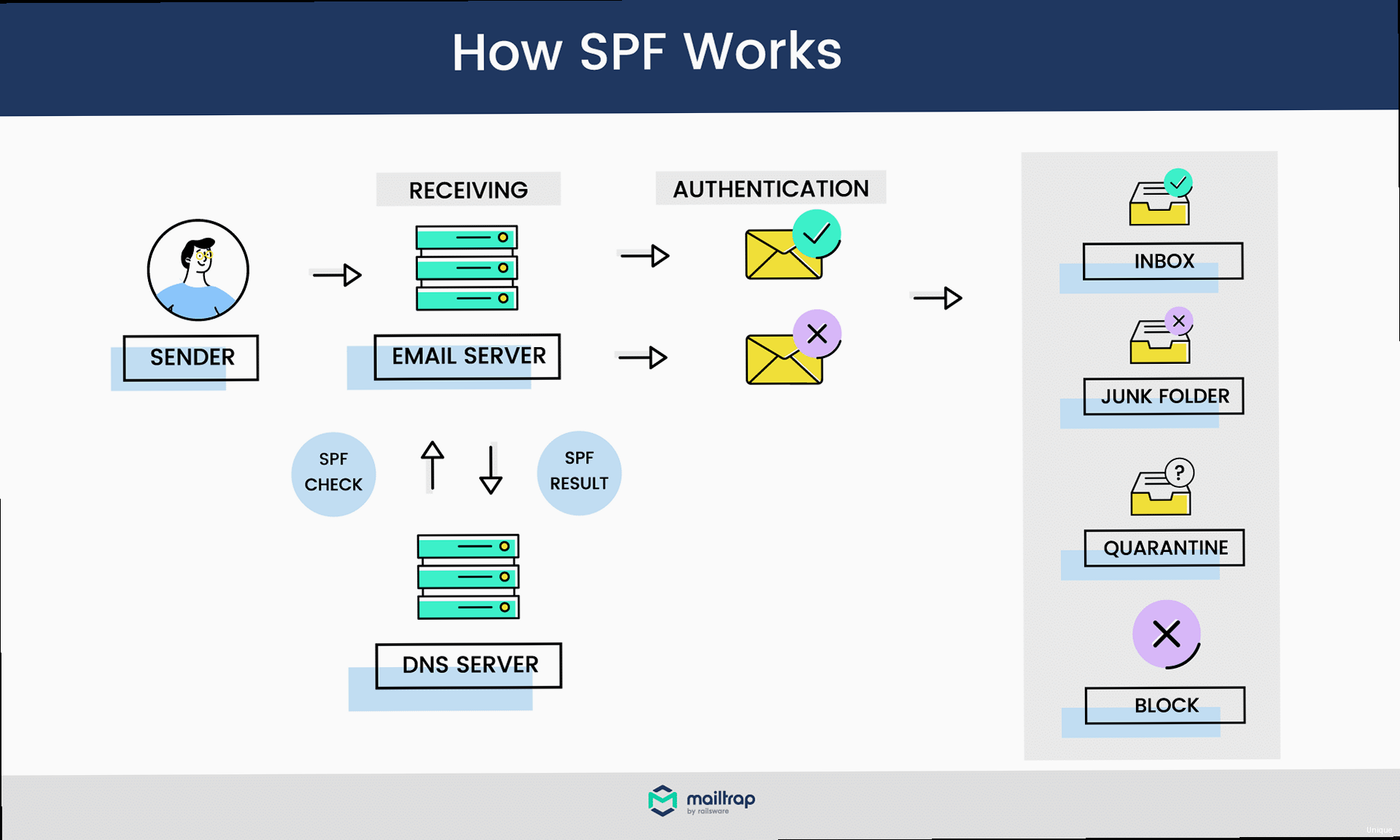
- Valid Syntax: The SPF record must adhere to the correct syntax, including using the
v=spf1version tag, authorized mechanisms (e.g.,ip4,ip6,a,mx,include), and a qualifier (e.g.,+,-,~,?). - Record Length: SPF records are limited to 255 characters. Exceeding this limit can cause the record to be ignored.
- Number of Lookups: SPF records should not exceed 10 DNS lookups, including nested
includestatements. Exceeding this limit will cause a “permerror” and the SPF check will fail. - “include” Mechanism Usage: The
includemechanism should be used carefully to avoid exceeding the lookup limit. It is best to include only necessary services in your SPF record. - “all” Mechanism: The
allmechanism should be used as the last mechanism in the record and should be used with a qualifier to indicate how to handle emails that do not match any of the preceding mechanisms. Common qualifiers are-all(fail),~all(softfail), and?all(neutral). Using-allis recommended for strict SPF enforcement, but be sure that ALL sending sources are included.
v=spf1 ip4:192.0.2.0/24 include:example.com -all-all mechanism indicates that any email not originating from these authorized sources should be rejected.
Example 2: SPF Record Without “all” Mechanism (Incorrect)
v=spf1 ip4:192.0.2.0/24 include:example.comall mechanism, the receiving server (like Yahoo) might default to a more lenient stance, but it’s better to be explicit. It’s highly recommended to end with an all mechanism for clarity.
Example 3: Exceeding Lookup Limits
v=spf1 include:example1.com include:example2.com include:example3.com include:example4.com include:example5.com include:example6.com include:example7.com include:example8.com include:example9.com include:example10.com -allinclude mechanisms. If any of the included domains *also* use include, it’s very easy to exceed the 10-lookup limit. This can lead to SPF failures. Consolidate where possible and be aware of the nested lookup depth.
Expert Tip: Regularly review your SPF record and the SPF records of included services. Services change, and their sending IP addresses may change as well. Keeping your SPF record up-to-date is crucial for maintaining email deliverability with Yahoo Mail.
Creating a Valid SPF Record for Yahoo Mail
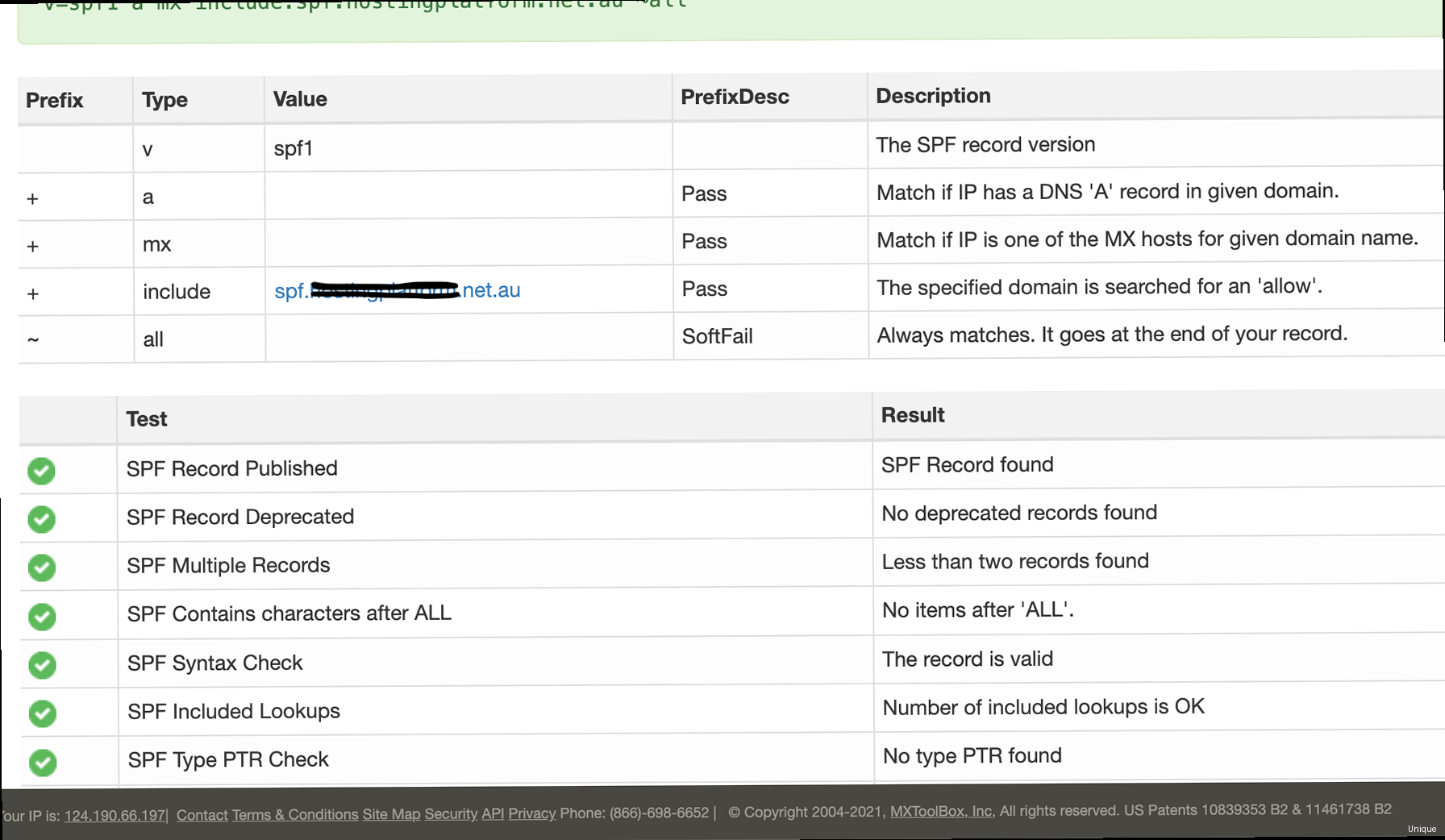
- Identify all sending sources: Determine all servers and services that send emails on behalf of your domain. This includes your mail servers, third-party email marketing platforms (e.g., Mailchimp, SendGrid), and any other services that send emails using your domain.
- Construct the SPF record: Create the SPF record using the
v=spf1version tag and appropriate mechanisms for each sending source. - Publish the SPF record: Add the SPF record as a TXT record in your domain’s DNS settings.
- Test the SPF record: Verify that the SPF record is correctly configured and accessible.
- Step 1: Start with the version tag: Begin your SPF record with
v=spf1. This tag identifies the record as an SPF record and specifies the version of SPF being used. - Step 2: Add authorized IP addresses: Use the
ip4andip6mechanisms to specify authorized IP addresses. For example,ip4:192.0.2.0/24authorizes all IP addresses in the 192.0.2.0/24 range. - Step 3: Include other domains: Use the
includemechanism to include the SPF records of other domains. This is useful when using third-party email services. For example,include:sendgrid.netincludes the SPF record of SendGrid. You MUST research and confirm the correct `include` value to use from each 3rd party. - Step 4: Specify authorized domains (A and MX records): Use the
aandmxmechanisms to authorize the IP addresses associated with your domain’s A and MX records, respectively. For example,aauthorizes the IP address of your domain’s A record, andmxauthorizes the IP addresses of your domain’s MX records. Be careful using `mx` — often the MX record points to a 3rd party that requires its own `include`. - Step 5: Use the “all” mechanism: End your SPF record with the
allmechanism to specify how to handle emails that do not match any of the preceding mechanisms. Use-allto reject emails,~allto softfail emails, or?allto treat emails neutrally.-allis generally preferred for strict enforcement.
v=spf1 ip4:203.0.113.10/32 a -allv=spf1 ip4:203.0.113.10/32 include:mailchimp.com -allv=spf1 ip4:203.0.113.10/32 include:sendgrid.net include:_spf.google.com -all- DNS Propagation: After publishing your SPF record, it may take some time for the changes to propagate across the internet. It’s recommended to wait 24-48 hours before testing the record.
- TXT Record Format: Ensure that your DNS provider supports TXT records and that the SPF record is entered correctly. Some DNS providers require you to enclose the SPF record in quotation marks (e.g.,
"v=spf1..."), while others do not.
include statements, be sure to document which services are included and why. This will make it easier to maintain and troubleshoot your SPF record in the future. Tools are available online that can help you evaluate the lookup depth of your SPF record.
Common SPF Errors and Troubleshooting for Yahoo
Even with careful planning, SPF records can sometimes be misconfigured, leading to email deliverability issues. Understanding common SPF errors and how to troubleshoot them is crucial for maintaining optimal email performance with Yahoo Mail. Common SPF Errors- Syntax Errors: Incorrect syntax, such as missing spaces, incorrect delimiters, or invalid mechanisms, can cause the SPF record to be ignored.
- Exceeding the Lookup Limit: SPF records should not exceed 10 DNS lookups. Exceeding this limit will result in a “permerror” and the SPF check will fail. This is often caused by too many nested
includestatements. - Missing Sending Sources: If your SPF record does not include all authorized sending sources, legitimate emails may be flagged as spam.
- Incorrect “all” Mechanism: Using the wrong qualifier with the
allmechanism (e.g.,+all) can negate the purpose of the SPF record. - Multiple SPF Records: Having multiple SPF records for the same domain is invalid and can cause unpredictable results.
- Step 1: Check the Syntax: Use an online SPF syntax checker to verify that your SPF record is correctly formatted. Many free tools are available online.
- Step 2: Verify the Lookup Count: Use an SPF record analyzer to determine the number of DNS lookups in your SPF record. If the lookup count exceeds 10, you will need to simplify your record by reducing the number of
includestatements. - Step 3: Confirm Sending Sources: Ensure that all authorized sending sources are included in your SPF record. Double-check your mail server settings, third-party email marketing platforms, and any other services that send emails on behalf of your domain.
- Step 4: Review the “all” Mechanism: Make sure that you are using the correct qualifier with the
allmechanism.-allis generally recommended for strict SPF enforcement. - Step 5: Check for Multiple SPF Records: Verify that you only have one SPF record for your domain. If you have multiple SPF records, delete the duplicate records.
- Step 6: Test Your SPF Record: Use online SPF testing tools to simulate the SPF check performed by receiving mail servers. These tools can help you identify potential issues with your SPF record.
v=spf1ip4:203.0.113.10/32 -allv=spf1 and ip4:203.0.113.10/32. The correct record should be:
v=spf1 ip4:203.0.113.10/32 -allv=spf1 include:example1.com include:example2.com include:example3.com include:example4.com include:example5.com include:example6.com include:example7.com include:example8.com include:example9.com include:example10.com -allinclude statements, the total number of lookups may exceed 10. To resolve this, you may need to consolidate the SPF records of these domains into a single record or use a different authentication method, such as DKIM.
Example 3: Missing Sending Source – Forgetting a Server
v=spf1 ip4:203.0.113.10/32 -allAdvanced SPF Configurations and Best Practices for Yahoo
Beyond basic SPF configuration, advanced techniques and best practices can further enhance your email deliverability and security with Yahoo Mail. These configurations involve strategies to optimize your SPF record, integrate it with other authentication methods, and implement monitoring practices. Optimizing Your SPF Record- Use CIDR Notation: Use CIDR notation (e.g.,
ip4:192.0.2.0/24) to specify IP address ranges efficiently. This reduces the number of individual IP addresses that need to be listed in your SPF record. - Consolidate “include” Statements: If possible, consolidate multiple
includestatements into a single statement. This can help reduce the number of DNS lookups and prevent exceeding the lookup limit. Some services offer a single “umbrella” include that covers all their sending sources. - Minimize Redundancy: Avoid including redundant IP addresses or domains in your SPF record. This can simplify your record and reduce the risk of errors.
- Regularly Review and Update: Review your SPF record regularly to ensure that it is up-to-date and includes all authorized sending sources. Remove any obsolete IP addresses or domains.
- DKIM: DKIM adds a digital signature to outgoing emails, allowing receiving mail servers to verify that the email was sent by an authorized sender and that the content has not been tampered with.
- DMARC: DMARC builds upon SPF and DKIM by specifying how receiving mail servers should handle emails that fail SPF and DKIM checks. DMARC also provides reporting capabilities, allowing domain owners to monitor email authentication results and identify potential issues.
- Publish DKIM Records: Generate DKIM keys for your domain and publish the public key as a TXT record in your DNS settings.
- Configure DMARC Policy: Create a DMARC record that specifies your desired policy (e.g.,
p=none,p=quarantine,p=reject) and reporting address (rua=mailto:your-email@example.com). - Monitor DMARC Reports: Regularly monitor DMARC reports to identify any authentication failures and take corrective action.
- DMARC Reporting: DMARC reports provide valuable insights into email authentication results, including SPF and DKIM pass/fail rates. These reports can help you identify potential issues with your SPF record and take corrective action.
- SPF Monitoring Tools: Use SPF monitoring tools to track changes to your SPF record and receive alerts when potential issues are detected.
- Log Analysis: Analyze your mail server logs to identify any SPF failures and investigate the root cause.
v=spf1 ip4:192.0.2.0/24 ip4:192.0.2.1 ip4:192.0.2.2 -allv=spf1 ip4:192.0.2.0/24 -allv=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; adkim=r; aspf=r;p=quarantine), which instructs receiving mail servers to place emails that fail SPF and DKIM checks into the recipient’s spam folder. It also includes reporting addresses for aggregate reports (rua) and forensic reports (ruf). The `adkim=r` and `aspf=r` flags request that DKIM and SPF checks be strict (“relaxed” is also an option).
Example 3: Using an SPF Monitoring Tool
Several online SPF monitoring tools are available that can track changes to your SPF record and alert you to potential issues. Some popular tools include:
- Dmarcian: Offers comprehensive DMARC monitoring and reporting services, including SPF record analysis.
- EasyDMARC: Provides a user-friendly interface for monitoring your DMARC, SPF, and DKIM records.
Verifying and Maintaining Your SPF Record for Yahoo Mail
After creating and publishing your SPF record, it’s crucial to verify that it’s correctly configured and functioning as expected. Regular maintenance is also essential to ensure that your SPF record remains accurate and up-to-date. This section outlines the steps involved in verifying and maintaining your SPF record for Yahoo Mail. Verifying Your SPF Record Follow these steps to verify your SPF record:- Use Online SPF Checkers: Use online SPF checking tools to verify that your SPF record is syntactically correct and accessible. These tools can also identify potential issues, such as exceeding the lookup limit or missing sending sources.
- Check DNS Propagation: After making changes to your SPF record, it may take some time for the changes to propagate across the internet. Use online DNS propagation checkers to verify that the updated SPF record is visible from different locations.
- Send Test Emails: Send test emails from your domain to different email providers, including Yahoo Mail, and check the email headers to verify that the SPF check is passing.
- Use Command-Line Tools: Use command-line tools like
digornslookupto query your DNS records and verify that the SPF record is published correctly.
- Regularly Review Sending Sources: Review your authorized sending sources regularly to ensure that they are still accurate and up-to-date. Remove any obsolete IP addresses or domains.
- Update SPF Record as Needed: Update your SPF record whenever you add or remove sending sources. This includes changes to your mail server settings, third-party email marketing platforms, and any other services that send emails on behalf of your domain.
- Monitor DMARC Reports: Monitor DMARC reports regularly to identify any authentication failures and take corrective action. This can help you identify potential issues with your SPF record and improve your email deliverability.
- Document Changes: Document all changes made to your SPF record, including the date, the reason for the change, and the person who made the change. This will make it easier to troubleshoot issues and maintain your SPF record in the future.
- Set Reminders: Set reminders to review your SPF record on a regular basis (e.g., quarterly or annually). This will help you ensure that your SPF record remains accurate and up-to-date.
- MXToolbox SPF Record Check: https://mxtoolbox.com/spf.aspx
- Dmarcian SPF Surveyor: https://dmarcian.com/spf-survey/
dig TXT example.comAuthentication-Results header that shows the results of the SPF check. Look for a line that indicates “spf=pass”. The exact format may vary depending on the receiving mail server. Here’s an example of what you might see:
Authentication-Results: mx.google.com;
spf=pass (google.com: domain of sender@example.com designates 203.0.113.10 as permitted sender) smtp.mailfrom=sender@example.com
person
Article Monster
Email marketing expert sharing insights about cold outreach, deliverability, and sales growth strategies.