
Understanding and Implementing Zorgmail SPF Records for Enhanced Email Delivery
In the world of email communication, ensuring deliverability is paramount. For organizations utilizing Zorgmail, a secure communication platform often used in healthcare, configuring Sender Policy Framework (SPF) records correctly is not just a best practice, it’s a necessity. This article provides a comprehensive guide to understanding, implementing, and troubleshooting SPF records for Zorgmail, enabling you to improve email delivery rates and protect your domain reputation.
This guide delves into the specifics of SPF records in the context of Zorgmail, going beyond the basics to address common challenges and provide actionable solutions. Learn how to properly authenticate Zorgmail as a legitimate sender for your domain, minimizing the risk of your emails being marked as spam or rejected outright.
SPF Record Basics and Zorgmail’s Role
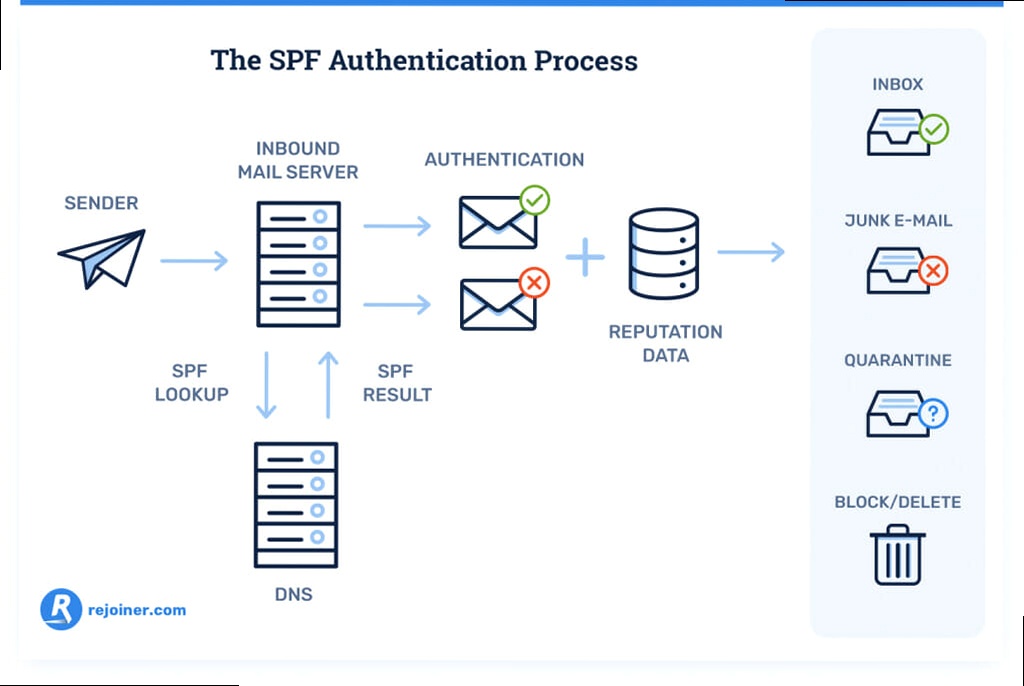
SPF, or Sender Policy Framework, is an email authentication method designed to prevent spammers from forging the “From” address in email messages. It works by allowing domain owners to specify which mail servers are authorized to send email on behalf of their domain. When a receiving mail server receives an email, it checks the SPF record of the sending domain. If the sending server is listed in the SPF record, the email passes the SPF check. If not, the email may be flagged as spam or rejected. This is especially critical when using a service like Zorgmail, as proper SPF configuration is necessary for recipients to trust that emails originating from Zorgmail are legitimate and haven’t been spoofed.
Without a correctly configured SPF record, emails sent from Zorgmail on behalf of your domain are more likely to be treated as spam by receiving mail servers. This can lead to significant communication issues, especially in the healthcare sector where timely and reliable delivery of sensitive information is paramount. Zorgmail, being a specialized platform, might have specific IP ranges or sending domains that need to be included in your SPF record to ensure proper authentication.
Understanding SPF Record Syntax
SPF records are DNS TXT records that follow a specific syntax. A basic SPF record starts with “v=spf1” followed by mechanisms that define which mail servers are authorized. Here’s a breakdown of common mechanisms:
- a: Matches the A record of the specified domain.
- mx: Matches the MX record(s) of the specified domain.
- ip4: Specifies an IPv4 address or range.
- ip6: Specifies an IPv6 address or range.
- include: Includes the SPF record of another domain. This is crucial for Zorgmail.
- -all: A hard fail. Any server not explicitly authorized should be rejected.
- ~all: A soft fail. Any server not explicitly authorized should be marked.
- +all: (Discouraged) Allows all servers to send email on behalf of your domain.
The `include` mechanism is particularly important for Zorgmail. Zorgmail will provide a specific domain to include in your SPF record, which authorizes their sending servers. For example, it might look like `include:zorgmail.example.com` (This is a hypothetical example; check with Zorgmail for their official include domain).
Why SPF is Crucial for Zorgmail
Zorgmail, being a platform often used for secure and sensitive communications, relies heavily on trust. A properly configured SPF record helps establish that trust by verifying that emails originating from Zorgmail are indeed legitimate. This is vital for:
- Improved Deliverability: Reduces the chances of emails being marked as spam.
- Domain Reputation: Protects your domain’s reputation, which affects the delivery of all your emails.
- Compliance: Helps comply with email authentication standards, which are increasingly important for regulatory compliance.
- Security: Prevents email spoofing and phishing attacks that could damage your organization’s reputation and compromise sensitive information.
Example 1: Basic SPF Record Without Zorgmail:
v=spf1 a mx -allThis record allows mail servers listed in the domain’s A and MX records to send email. The `-all` mechanism ensures that any other server is rejected. This is NOT sufficient for Zorgmail.
Example 2: SPF Record Including Zorgmail (Hypothetical):
v=spf1 a mx include:zorgmail.example.com -allThis record allows mail servers listed in the domain’s A and MX records, as well as servers authorized by `zorgmail.example.com`, to send email. Important: Replace `zorgmail.example.com` with the actual domain provided by Zorgmail. The `-all` mechanism ensures that any other server is rejected.
Example 3: SPF Record Including Zorgmail and a Specific IP Address:
v=spf1 ip4:192.0.2.0/24 a mx include:zorgmail.example.com -allThis record allows mail servers with IP addresses in the 192.0.2.0/24 range, servers listed in the domain’s A and MX records, and servers authorized by `zorgmail.example.com` to send email. Again, ensure that the Zorgmail domain is the correct one provided by their documentation.
Expert Tip: Always consult Zorgmail’s official documentation or support channels for the most accurate and up-to-date information regarding their required SPF record inclusions. Failure to do so can result in email delivery issues.
Creating an SPF Record for Zorgmail: A Step-by-Step Guide
Creating an SPF record for Zorgmail involves several steps. First, you’ll need to gather the necessary information, including Zorgmail’s specific SPF include statement (if any) and any other mail servers that need authorization to send emails on behalf of your domain. Next, you’ll access your domain’s DNS settings and add or modify a TXT record with the appropriate SPF syntax. Finally, you’ll need to test and validate the record to ensure it’s working correctly.
It’s crucial to understand that you should only have one SPF record per domain. If you already have an SPF record, you’ll need to modify it to include Zorgmail’s information, rather than creating a new one. Having multiple SPF records can lead to unpredictable results and may negatively impact email delivery.
Step 1: Gather Required Information
Before you begin, gather the following information:
- Zorgmail’s SPF Include Statement: Contact Zorgmail support or consult their documentation for the exact `include:` statement required for their service. This is the most crucial piece of information. Do not guess this!
- List of Authorized Mail Servers: Identify all other mail servers that send emails on behalf of your domain. This includes your internal mail servers, marketing automation platforms, and any other third-party services. Gather their IP addresses or domain names.
- Access to DNS Settings: Ensure you have the necessary credentials to access your domain’s DNS settings. This is usually through your domain registrar or hosting provider.
Step 2: Construct the SPF Record
Based on the information gathered, construct your SPF record. Start with `v=spf1` and add the necessary mechanisms to authorize all legitimate sending sources. Remember to include Zorgmail’s `include:` statement.
Example 1: Simple SPF Record with Zorgmail Include:
v=spf1 include:zorgmail.example.com -allThis record only authorizes Zorgmail to send emails. Replace `zorgmail.example.com` with the proper value.
Example 2: SPF Record with Zorgmail, MX Records, and an IP Address:
v=spf1 mx ip4:203.0.113.0/24 include:zorgmail.example.com -allThis record authorizes servers listed in the domain’s MX records, servers within the 203.0.113.0/24 IP range, and Zorgmail. Replace `zorgmail.example.com` with the proper value.
Example 3: Modifying an Existing SPF Record to Include Zorgmail:
Let’s say your existing SPF record is:
v=spf1 a mx -allTo include Zorgmail, modify it to:
v=spf1 a mx include:zorgmail.example.com -allAgain, replace `zorgmail.example.com` with the proper value provided by Zorgmail.
Step 3: Add the SPF Record to DNS
1. Log in to your domain registrar or hosting provider’s control panel. 2. Navigate to the DNS settings. The exact location varies depending on your provider. Look for options like “DNS Zone Editor,” “DNS Records,” or similar. 3. Add a new TXT record. You may need to specify a hostname. If so, leave it blank or enter “@” to apply the record to the root domain. 4. Enter the SPF record in the “Value” or “Text” field. 5. Save the changes.
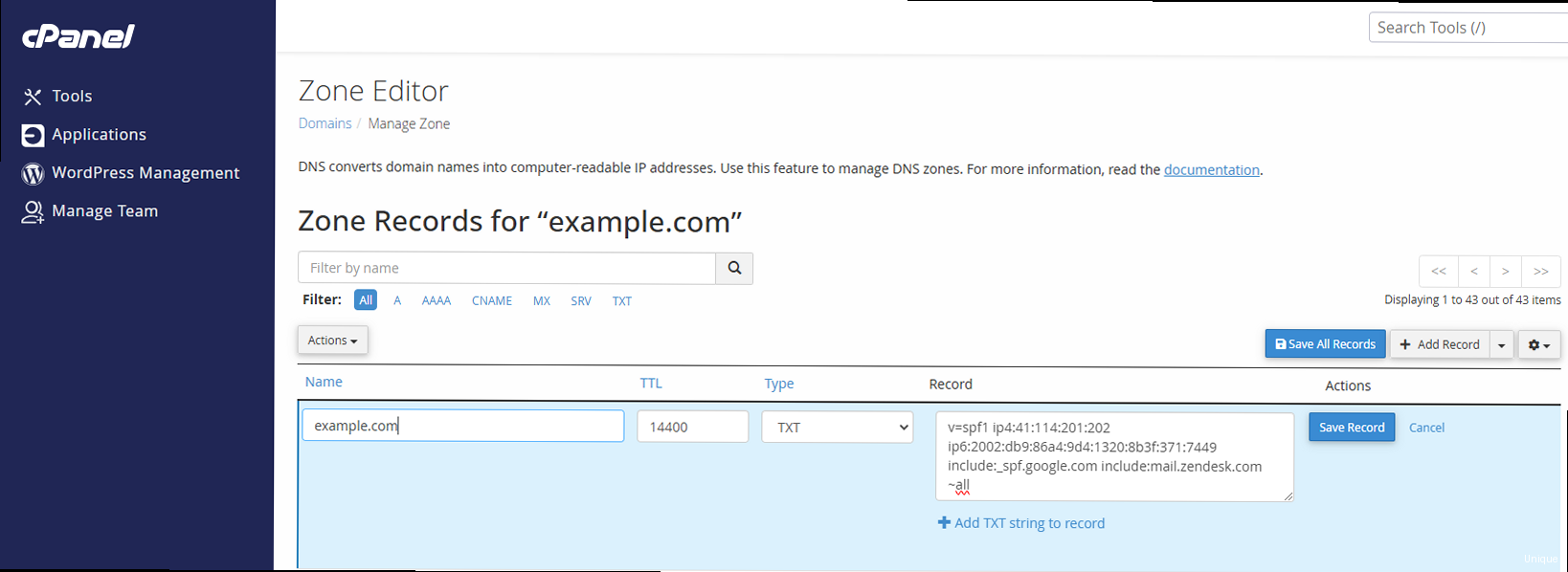
Example: Adding an SPF record in cPanel:
1. Log in to your cPanel account. 2. Go to “Zone Editor.” 3. Select the domain you want to modify. 4. Click “+ Add Record.” 5. Choose “TXT” as the record type. 6. Leave the “Name” field as your domain name (or enter “@”). 7. Enter the SPF record in the “Record” field (e.g., `v=spf1 a mx include:zorgmail.example.com -all`). 8. Click “Add Record.”
Important Considerations:
- Propagation Time: It can take up to 48 hours for DNS changes to propagate across the internet. During this time, some mail servers may use the old record, while others use the new one.
- Record Length Limit: SPF records have a length limit. Exceeding this limit can cause the record to be ignored. Keep your record concise and efficient.
- “Too Many Lookups” Error: SPF records can only have a limited number of DNS lookups (typically 10). Using too many `include:` or other mechanisms that require DNS lookups can cause an error. Simplify your record if necessary.
Expert Tip: Use a dedicated tool to analyze your SPF record for errors and potential issues before adding it to your DNS. This can save you time and prevent delivery problems. There are many free online SPF record checkers available.
SPF Record Testing and Validation for Zorgmail
Once you’ve created and deployed your SPF record, it’s essential to test and validate it to ensure it’s working correctly. This involves using various online tools and methods to verify that the record is syntactically correct, that it authorizes the intended mail servers, and that it doesn’t contain any errors that could negatively impact email delivery. Proper validation is crucial to avoid deliverability issues, especially when using Zorgmail for critical communications.
Using Online SPF Record Checkers
Several online tools can help you check your SPF record. These tools typically analyze the record for syntax errors, DNS lookup limits, and other potential issues. Here are a few popular options:
- MXToolbox SPF Record Check: A comprehensive tool that checks for various SPF issues, including syntax errors, DNS lookup limits, and common mistakes. (https://mxtoolbox.com/spf.aspx)
- Dmarcian SPF Surveyor: Provides a detailed analysis of your SPF record, including a visual representation of the DNS lookup path. (https://dmarcian.com/spf-survey/)
- SPF Record Testing Tools (EasyDMARC): Checks if your SPF record is valid and correctly formatted. (https://easydmarc.com/tools/spf-record-lookup)
To use these tools, simply enter your domain name and click “Check” or “Lookup.” The tool will then analyze your SPF record and display the results. Pay close attention to any errors or warnings, and address them accordingly.
Example: Using MXToolbox to check an SPF record:
1. Go to https://mxtoolbox.com/spf.aspx. 2. Enter your domain name in the “Domain Name” field. 3. Click “SPF Record Lookup.” 4. Review the results. The tool will highlight any errors or warnings in your SPF record. For example, it might show a “Too Many DNS Lookups” error or a syntax error. 5. If you see any errors, correct them in your DNS settings and re-run the test.
Sending Test Emails and Analyzing Headers
Another way to validate your SPF record is to send test emails from a mail server authorized by your SPF record (including Zorgmail) to an external email address (e.g., a Gmail or Yahoo account). Then, analyze the email headers to see if the SPF check passed.
To view email headers, open the email in your email client and look for an option like “View Source,” “Show Original,” or “Message Details.” The exact wording varies depending on your email client.
In the email headers, look for the “Received-SPF” header. This header indicates the result of the SPF check. A “pass” result means that the SPF check passed successfully.
Example: Analyzing email headers in Gmail:
1. Open the email in Gmail. 2. Click the three dots in the upper-right corner of the email. 3. Select “Show Original.” 4. Search for the “Received-SPF” header. It should look something like this:
Received-SPF: pass (google.com: domain of sender@yourdomain.com designates 203.0.113.1 as permitted sender) client-ip=203.0.113.1;If the `Received-SPF` header shows “pass,” then your SPF record is working correctly for that sending server. If it shows “fail,” “softfail,” or “neutral,” then there’s an issue with your SPF record that needs to be addressed.
Example Scenarios:
- Scenario 1: SPF check fails for Zorgmail: If the `Received-SPF` header shows a failure when sending from Zorgmail, double-check that you’ve included the correct `include:` statement in your SPF record, as provided by Zorgmail.
- Scenario 2: SPF check passes for some servers but fails for others: This indicates that your SPF record doesn’t authorize all legitimate sending servers. Add the missing IP addresses or `include:` statements to your record.
- Scenario 3: SPF check consistently fails: This could indicate a syntax error in your SPF record or a DNS propagation issue. Double-check your record for errors and wait for DNS propagation to complete.
Quote: “Regularly testing and validating your SPF record is crucial for maintaining optimal email deliverability. Don’t just set it and forget it!” – Email Security Expert
Troubleshooting Common SPF Issues with Zorgmail
Even with careful planning and implementation, SPF record issues can still arise. These issues can manifest as email delivery problems, such as emails being marked as spam or rejected outright. When using Zorgmail, it’s crucial to quickly identify and resolve any SPF-related issues to maintain reliable communication. This section outlines common SPF problems and provides actionable solutions specifically tailored for Zorgmail users.
Common SPF Issues and Their Solutions
| Issue | Description | Solution |
|---|---|---|
| Syntax Errors | The SPF record contains syntax errors, such as missing quotes, incorrect delimiters, or invalid mechanisms. | Carefully review the SPF record for syntax errors. Use an online SPF record checker to identify and correct any mistakes. |
| Missing Zorgmail Include | The SPF record doesn’t include the necessary `include:` statement for Zorgmail, causing emails sent from Zorgmail to fail the SPF check. | Add the correct `include:` statement for Zorgmail to your SPF record. Obtain the correct statement from Zorgmail’s documentation or support. |
| Too Many DNS Lookups | The SPF record exceeds the maximum number of DNS lookups (typically 10), causing the record to be truncated or ignored. | Simplify the SPF record by reducing the number of `include:` statements or other mechanisms that require DNS lookups. Consider using IP addresses instead of domain names where possible. |
| Multiple SPF Records | The domain has multiple SPF records, which is invalid and can lead to unpredictable results. | Remove all but one SPF record. Merge the information from the multiple records into a single, valid record. |
| DNS Propagation Issues | Changes to the SPF record haven’t propagated across the internet, causing some mail servers to use the old record while others use the new one. | Wait for DNS propagation to complete (up to 48 hours). You can use online DNS propagation checkers to monitor the progress. |
| Incorrect IP Addresses or Ranges | The SPF record includes incorrect IP addresses or ranges for authorized mail servers. | Verify that the IP addresses and ranges are correct and up-to-date. |
Specific Troubleshooting Steps for Zorgmail
When troubleshooting SPF issues specifically related to Zorgmail, consider the following steps:
- Verify the Zorgmail Include Statement: Double-check that you’re using the correct `include:` statement provided by Zorgmail. This is the most common cause of SPF failures when using Zorgmail. Contact their support if you are unsure.
- Check for IP Address Changes: Zorgmail might occasionally change its sending IP addresses. Subscribe to their announcements or contact their support to stay informed about any IP address changes and update your SPF record accordingly. While using `include:` is generally preferred to manually listing IPs, understanding if IP changes occur can help diagnose issues.
- Review Zorgmail’s Documentation: Consult Zorgmail’s official documentation for specific SPF configuration instructions and troubleshooting tips. They may have specific requirements or recommendations that are not covered in general SPF guides.
- Contact Zorgmail Support: If you’re unable to resolve the issue on your own, contact Zorgmail’s support team for assistance. They can provide specific guidance and troubleshoot the problem from their end.
Example 1: Incorrect Zorgmail Include Statement:
Let’s say you’ve added the following `include:` statement to your SPF record:
v=spf1 include:zorgmail.net -allHowever, Zorgmail has recently informed you that their correct `include:` statement is:
v=spf1 include:email.zorgmail.com -allChanging the `include:` statement to the correct value will resolve the SPF failure.
Example 2: SPF Failure Due to Too Many DNS Lookups:
Your SPF record contains multiple `include:` statements, resulting in more than 10 DNS lookups:
v=spf1 a mx include:zorgmail.example.com include:thirdparty.com include:anotherthirdparty.com -allTo resolve this, try to simplify the record by removing unnecessary `include:` statements or consolidating them into a single `include:` statement if possible. Alternatively, if `thirdparty.com` and `anotherthirdparty.com` authorize the same set of IP addresses, you might be able to replace them with explicit `ip4:` or `ip6:` mechanisms.
Example 3: Using `dig` to Verify DNS Records:
The `dig` command-line tool can be used to query DNS records and verify that your SPF record is correctly configured.
dig txt yourdomain.comThis command will display the TXT records for your domain, including your SPF record. Check that the output matches your intended SPF record configuration.
Expert Tip: Implement DMARC (Domain-based Message Authentication, Reporting & Conformance) in addition to SPF. DMARC builds upon SPF and DKIM (DomainKeys Identified Mail) to provide a more robust email authentication framework. DMARC also provides reporting capabilities, allowing you to monitor SPF and DKIM authentication results and identify potential issues.
Advanced SPF Considerations for Zorgmail and Beyond
While implementing a basic SPF record for Zorgmail is essential, there are several advanced considerations that can further enhance your email security and deliverability. These considerations include understanding SPF’s limitations, implementing DKIM and DMARC, and managing subdomains and third-party senders. By addressing these advanced topics, you can create a more robust email authentication strategy that protects your domain reputation and ensures reliable communication through Zorgmail and other channels.
SPF Limitations and How to Address Them
SPF has some inherent limitations that can affect its effectiveness. One major limitation is that SPF only authenticates the “envelope from” address, which is not always the same as the “From” address displayed in the email client. This means that spammers can still forge the “From” address, even if the SPF check passes for the “envelope from” address. Additionally, SPF can break when emails are forwarded, as the forwarding server may not be authorized by the original sender’s SPF record.
To address these limitations, it’s crucial to implement DKIM (DomainKeys Identified Mail) in conjunction with SPF. DKIM adds a digital signature to the email header, which can be verified by the receiving mail server. This signature is tied to the domain name and is not affected by forwarding. By implementing both SPF and DKIM, you provide a more comprehensive email authentication solution.
Comparison: SPF vs. DKIM
| Feature | SPF | DKIM |
|---|---|---|
| Authentication Method | Authenticates the sending server’s IP address against a list of authorized servers. | Authenticates the email content using a digital signature. |
| Address Authenticated | Authenticates the “envelope from” address. | Authenticates the domain name in the “From” address. |
| Forwarding Compatibility | Can break when emails are forwarded. | Remains valid when emails are forwarded. |
| Implementation Complexity | Relatively simple to implement. | More complex to implement, requiring key generation and DNS configuration. |
| Limitations | Only authenticates the “envelope from” address; can break with forwarding. | Requires proper key management and DNS configuration. |
Implementing DMARC for Enhanced Protection
DMARC (Domain-based Message Authentication, Reporting & Conformance) builds upon SPF and DKIM to provide a more robust email authentication framework. DMARC allows domain owners to specify how receiving mail servers should handle emails that fail SPF and DKIM checks. It also provides reporting capabilities, allowing domain owners to monitor SPF and DKIM authentication results and identify potential issues.
To implement DMARC, you need to create a DMARC record in your DNS settings. The DMARC record specifies the policy that receiving mail servers should enforce when an email fails SPF or DKIM checks. Common DMARC policies include:
- none: Monitor authentication results without taking any action.
- quarantine: Mark emails that fail authentication as spam.
- reject: Reject emails that fail authentication.
The DMARC record also specifies an email address where receiving mail servers should send reports about authentication results. These reports can be used to identify potential issues and improve your email authentication strategy.
Example: DMARC Record:
v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:dmarc-forensic@yourdomain.com; adkim=r; aspf=r;This record tells receiving mail servers to quarantine emails that fail SPF and DKIM checks and to send aggregate reports to `dmarc-reports@yourdomain.com` and forensic reports to `dmarc-forensic@yourdomain.com`. The `adkim=r` and `aspf=r` parameters specify that DKIM and SPF alignment should be “relaxed,” meaning that the domain in the “From” address doesn’t have to exactly match the domain in the DKIM signature or the SPF record.
Managing Subdomains and Third-Party Senders
If you use subdomains for different purposes (e.g., `marketing.yourdomain.com`, `support.yourdomain.com`), you may need to configure separate SPF records for each subdomain. This allows you to authorize different mail servers for each subdomain. Similarly, if you use third-party services to send emails on behalf of your domain, you need to ensure that their sending servers are authorized by your SPF record.
When managing subdomains, it’s important to remember that SPF records are inherited by subdomains unless explicitly overridden. This means that if you have an SPF record for your root domain, it will apply to all subdomains unless you create a specific SPF record for a subdomain.
When using third-party senders, it’s crucial to carefully review their SPF requirements and ensure that you include the necessary `include:` statements or IP addresses in your SPF record. You should also monitor your DMARC reports to identify any unauthorized senders and take appropriate action.
Example: Subdomain SPF Record:
Article Monster
Email marketing expert sharing insights about cold outreach, deliverability, and sales growth strategies.
Ready to Boost Your Outreach?
Try Postigo - Professional email outreach platform with AI personalization